Resource Center
Welcome to our cybersecurity resource center where we uncover how malicious actors exploit weaknesses in systems, while going beyond the technical aspects and examining real-world perspectives across various industries.
Here you’ll find extensive research and insight from the well-known Horizon3.ai attack team, intuitive perspectives on everything security, and real-world attack path short stories that come directly from discoveries made by NodeZero.
Filters
Showing 13–18 of 417 results
NodeZero: More than a concept — a Proof of Value
See your enterprise through the eyes of an attacker - More than a concept — a Proof of Value
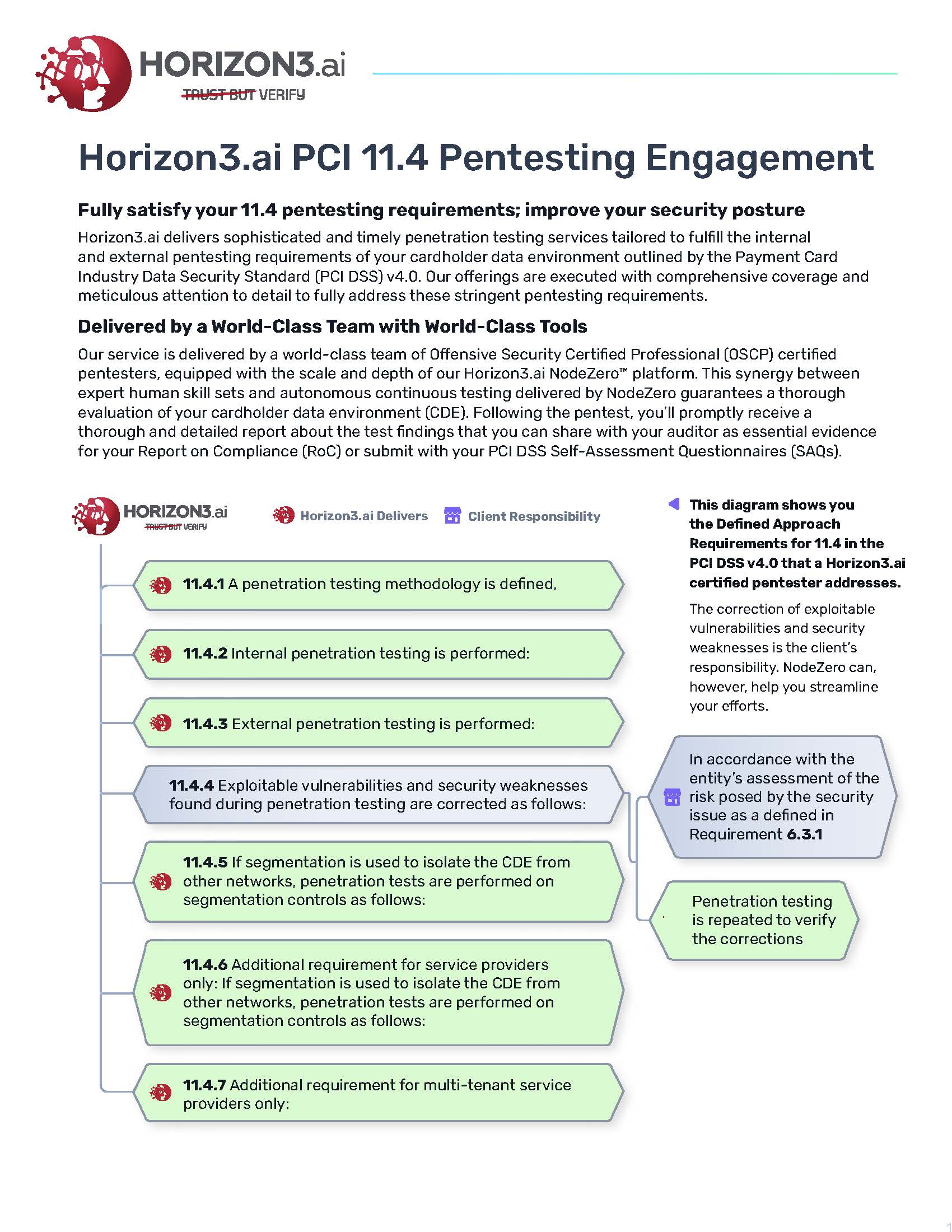
Read More Horizon3.ai PCI 11.4 Pentesting Engagement
Horizon3.ai delivers sophisticated and timely penetration testing services tailored to fulfill the internal and external pentesting requirements of your cardholder data environment outlined by the Payment Card Industry Data Security Standard (PCI DSS) v4.0. Our offerings are executed with comprehensive coverage and meticulous attention to detail to fully address these stringent pentesting requirements.
Read More Security Today Govies Award
Winner, Security Today Govies for Autonomous Penetration Testing
Read More Autonomous Penetration Testing with Horizon3.ai
The NodeZero platform is easy-to-use, safe for production, and scales to support your largest networks. You are empowered to test a very broad scope in a single test, orchestrate tests concurrently, and simultaneously test your enterprise from different attacker perspectives.
Read More NodeZero Capability Statement
The NodeZero platform empowers your organization to reduce your security risk by autonomously finding exploitable weaknesses in your network, giving you detailed guidance about how to prioritize and fix them, and helping you immediately verify that your fixes are effective.
Read More Empowering Educational Compliance: Navigating the Future with Autonomous Pentesting in Academia
How Autonomous Pentesting with NodeZero Transformed University Protection
Read More