Our Vision:
The Future of Security
Criminal organizations are already using highly automated attack tools to execute ransomware attacks and other campaigns successfully. In Gartner’s latest Security Hype Cycle, Autonomous Pentesting is a rising category, recognizing the potential for applying machine learning & AI to conduct offensive cyber operations.
The future of cyber warfare will run at machine speed – algorithm vs. algorithm – with humans by exception.
– Snehal Antani, CEO and Co-Founder Horizon3.ai
It’s only a matter of time before criminals leverage autonomous attack techniques.
As an industry, we must prepare for the technological leap that Ransomware-as-a-Service and similar nefarious platforms are about to take.
In less than 3 minutes and 30 seconds
NodeZero successfully compromised Hack The Box “Active” a moderately difficult cyber range.
In 7 minutes and 19 seconds
NodeZero autonomously found multiple paths to gain Domain Admin privileges within the network of a financial services company, undetected, despite the company’s state-of-the-art security tools.
So What?
In the Near Term:
We’ll see automated attacks continue to decimate security organizations…
… that have deployed the latest tools because we don’t have a tools problem, we have an effectiveness problem. Our many siloed security tools are not designed to work together, and the seams between those tools equate to blind spots that attackers exploit.
In the Mid Term:
Sadly, we believe things will get worse…
… attackers will shift to autonomous attack platforms faster than defenders can improve the effectiveness of their security posture.
In the Long Term:
Within a decade or so, we believe cyber warfare will be “humans by exception”.
Human defenders simply cannot keep pace with how quickly attack algorithms can compromise the network. This is compounded with the fact that algorithmic attack significantly reduces the barriers to entry for threat actors, which will therefore increase the volume of attacks.
Machine Speed is the Ultimate Disruptor
Algorithm-centric attacks can make 100x more “maneuver decisions per minute” than human-centric defenders.
Humans must sift through logs, cognitively process alerts, and get permission to apply fix-actions. By the time this human-driven triage process has been executed, attack algorithms have already adapted.
In 5 years, an algorithmic attack could execute 100,000x more decisions per minute than human-centric defense, effectively rendering current security products obsolete.
Algorithmic cyber warfare will come down to “maneuver decisions per minute” – how many decisions can an attack algorithm make and how quickly can defensive algorithms anticipate & react to stifle the compromise. Therefore, the next generation of security tools will be designed for humans-out-of-the-loop, enabled by cloud-first IT environments that are inherently ephemeral, observable, segmented, revokable, and defensible, which are prerequisites for autonomous defense
Horizon3.ai’s Story
We are a mix of US Special Operations, US National Security, and cybersecurity industry veterans. Our mission is to “turn the map around” – using the attacker’s perspective to help enterprises prioritize defensive efforts. Our team of nation-state-level, ethical hackers continuously identifies new attack vectors through autonomous pentesting and red team operations, leveraging collective intelligence to improve our products and strengthen our clients’ security. Founded in 2019, Horizon3.ai is headquartered in San Francisco, CA, and 100% made in the USA.
Our Vision
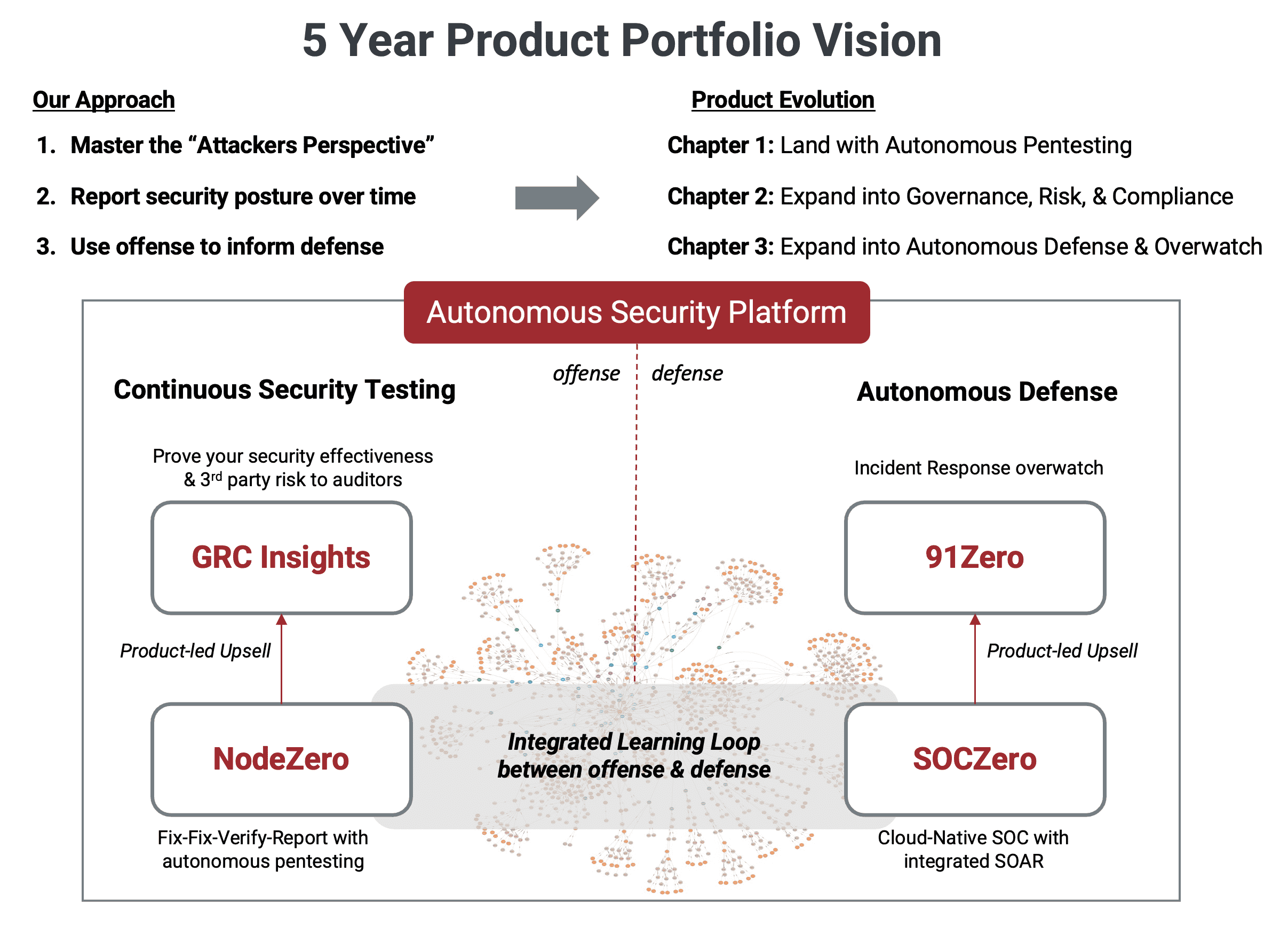
Autonomous pentesting enables organizations to see themselves through the eyes of the attacker. With this attacker’s perspective, enterprises can continuously identify their ineffective security controls and identify critical, exploitable weaknesses that they must immediately fix. However, autonomous pentesting is only part of the equation. Our larger vision is to leverage our expertise, data, and insights to build an autonomous defense designed to be humans by exception. We will deliver continuous attack, paired with continuous defense–executing an integrated learning loop that gets smarter with every interaction, delivered as an Autonomous Security Platform.
The Cyber Terrain Map, the knowledge graph at the heart of Horizon3.ai’s autonomous pentesting platform, is the critical data structure required to build autonomous security. With every pentest executed, these knowledge graphs get smarter – increasing its understanding of how an attacker can chain together harvested credentials, misconfigurations, dangerous product defaults, and exploitable vulnerabilities to compromise a system. Collective intelligence services analyze these insights and further optimize the attack algorithms. Thus, the more autonomous pentests we run, the richer our collective intelligence becomes, which leads to more efficient & effective attack algorithms.
Our Journey in 3 chapters
Our initial focus is to deliver autonomous pentesting capabilities to help customers quickly find, fix, and verify the remediation of critical security weaknesses. Think: “Pentest Wednesday” that verifies “Patch Tuesday” was successful.
Per Gartner,
“Security testing, like network penetration testing and red teaming, plays an important role in an organization’s capabilities to identify exposures, vulnerabilities and weaknesses in their defenses. Many organizations only test on an annual or ad hoc basis, rarely testing more frequently or even continuously in their environment due to the cost and lack of internal expertise… more frequent testing helps find and mitigate weaknesses faster… [with autonomous pentesting] organizations can take advantage of frequent pentesting without having to hire expensive experts.”
Our initial product focus is to give IT Administrators and Network Engineers “security superpowers,” enabling them to continuously assess their enterprise’s security & compliance posture with the skills of a 20-year pentesting veteran but at a fraction of the cost and effort.
As we build out our customer base, we will introduce features that cater to more advanced security teams – interfaces explicitly designed for penetration testers and bug bounty hunters, adversary emulation, etc. – serving as a force multiplier for these security professionals
Finally, for the most advanced security organizations, we will deliver “Purple Teaming as a Service” to enable & accelerate the collaboration between red and blue teams.
To summarize, our thesis is that autonomous pentesting is the equivalent of continuous integration testing in software development. In addition, enterprises need a “sparring partner” to verify the effectiveness of their security posture, and autonomous pentesting is the only cost-effective option to help enterprises identify weaknesses in their security controls. The alternative is to wait for a breach to determine if you made a mistake configuring your security tools.
Become the most trusted security testing and risk assessment platform.
To build Cyber Terrain Maps and execute autonomous pentesting requires that we map the internal and external attack surface, prioritize exploitable vulnerabilities, understand the change in security posture over time, and report on our findings to drive fix-actions. We will productize these capabilities through feature-flag integrations with our core platform, increasing the spend of existing customers and capturing net-new customers by targeting adjacent, siloed, expensive tools that are laborious to maintain, including:
- External Attack Surface Management (EASM)
- Cyber Asset Attack Surface Management (CAASM)
- Pentesting as-a-Service (PTaaS)
- Breach & Attack Simulation
- Vulnerability Prioritization Technology (VPT)
- Integrated Risk Management
Early indications from our customer base validate our ability to expand into these categories. For example, a multi-billion-dollar manufacturing firm with nascent security capabilities initially used our autonomous pentesting product to find, fix, and verify their security issues frequently. They quickly evolved to answer attack surface management questions, more advanced pentesting activities, and improve the prioritization of their vulnerabilities. Per their feedback, they no longer have a reason to buy another siloed tool. Our platform can more accurately answer the questions these tools answer but at a fraction of the cost. This experience gives us confidence that we can evolve into an integrated security testing & risk management platform that simplifies the number of tools required by customers, lowers overall costs, and delivers superior insights.
Become the most trusted autonomous defense platform in the industry.
Current technologies were designed to be open and interoperable, with security as an afterthought. Future systems must be “defensible by design” – adhering to the following characteristics, exposed as API’s that algorithmic defense services can control:
- Ephemeral. Future systems must be ephemeral by design – eliminating the concept of “patching,” which takes effort and imposes a risk to availability. Instead, these future systems must quickly reconstitute – be destroyed and rapidly recreated with the latest software versions, with minimal disruption to the end-user.
- Segmented. Future systems must be designed with segmentation strategies that stifle lateral movement while minimizing administrative overhead. For example, two systems that have no business reason to reach other should be isolated from one another. Segmentation should occur at all levels of the technology stack –hardware based enforcement (e.g. logical partitions in mainframes and gaming consoles), to emerging named-data networking concepts that separate the logical network from the physical network, to micro-segmented networks that align to zero trust concepts.
- Revocable. Future systems must quickly grant or revoke access to data, systems, and services based on need or suspected abuse.
- Observable. Future systems must be instrumented by design, allowing for the understanding of internal system behavior, its correlation with the behavior of other components, and quickly identify potential abuse.
- Private. Every aspect of the system should be encrypted by default. Only those systems, services, and users that “need to know” – observe network traffic, view data, etc. – should be able to see those artifacts, and even then, access should be granted for a limited time to maximize privacy.
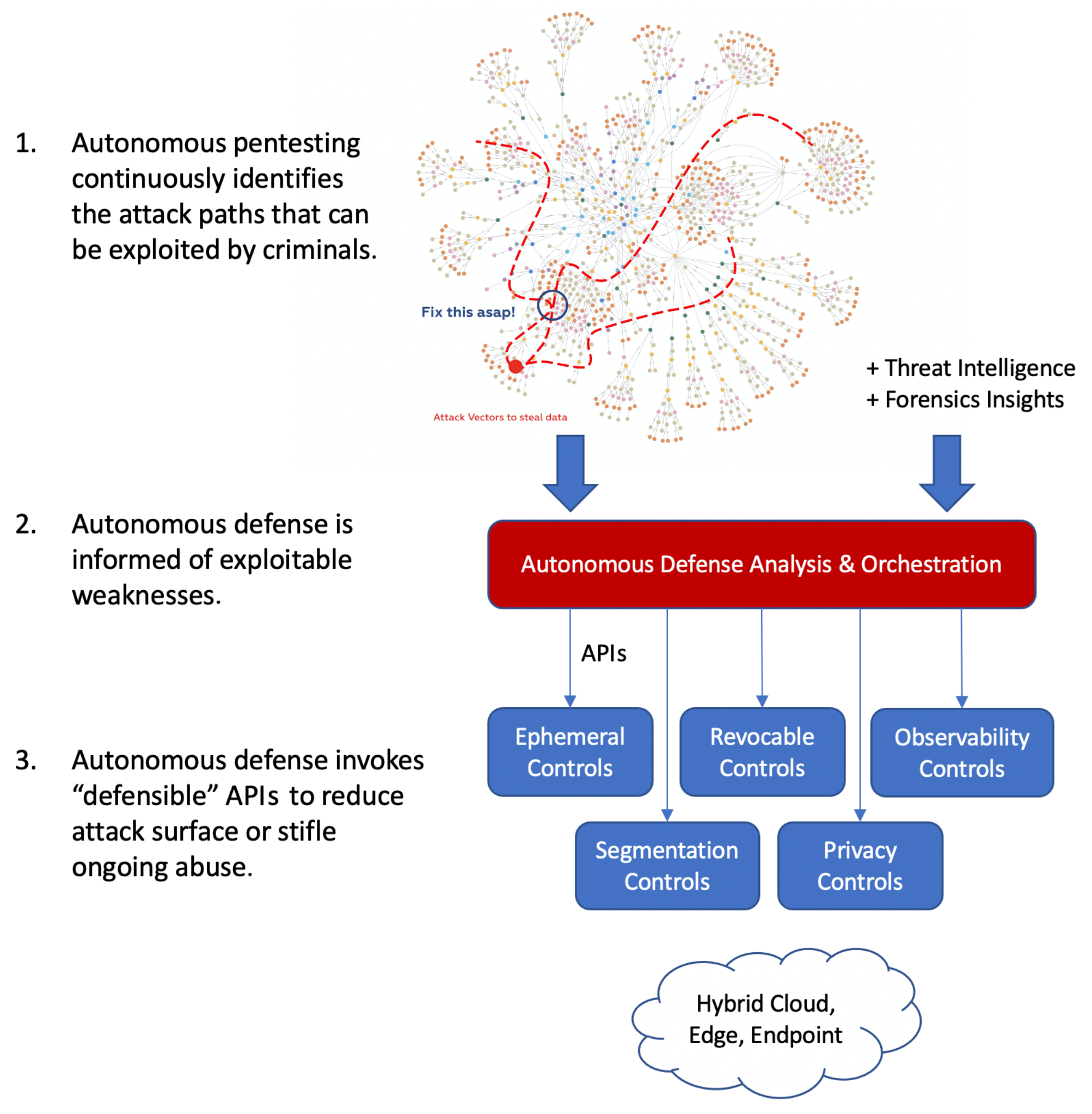
The role of Horizon3.ai in this era of “defensible by design” is that of “orchestrator” that manipulates the various “knobs” and “levers” exposed as API’s to reduce the attack surface of the enterprise and stifle on-going attacks. Cloud-native architectures are best suited to implement these characteristics, with Zero Trust and other security trends serving as a catalyst for building new digital services with the right controllable defensibility services.
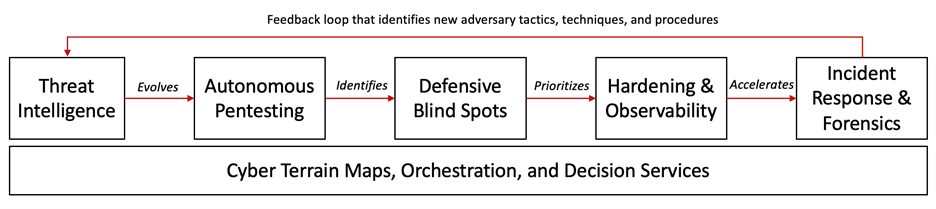
The use of autonomous pentesting, which provides the attackers’ perspective, gives us a comprehensive and detailed understanding of how various threat actors can maneuver throughout an enterprise to compromise critical data and systems. This “sparring partner” gives us two advantages: First, at development time, it enables us to build CI/CD-like pipelines to test the efficacy of defensive algorithms; and second, at execution time, the collective intelligence services provide input to the defensive algorithms for where to harden and observe for abuse. We will be positioned to develop and deploy highly effective algorithmic defense capabilities, enabling us to become the most trusted Autonomous Defense platform in the industry.
In this new paradigm, autonomous pentesting is continuously attacking using the same techniques as threat actors. Autonomous defense constantly observes the critical waypoints that enable attacks, hardening components that allowed the attacker – both benign pentesting and malicious actors – to succeed.
The more frequent the interaction between offense and defense, the more robust the learning loop between the two sides, and the harder it becomes for real threat actors to compromise systems.
The learning loop between offense and defense accelerates understanding, with offense incorporating new adversary behavior through threat intelligence and forensics, offensive notifying defense of new weaknesses and waypoints, and defense manipulating the defensible characteristics of systems to stifle attack. All this is executing with “humans by exception.”