Internal Pentesting
with NodeZero
What can an attacker do inside your network?
- On-premises infrastructure
- Cloud infrastructure
- Identity and access management infrastructure
- Data infrastructure
- Virtual infrastructure
Autonomous Exploits
NodeZero autonomously discovers and exploits weaknesses in your network just as an attacker would. It moves laterally in your environment by:
- Compromising credentials through credential attacks
- Mining exposed data
- Bypassing security controls
- Exploiting key vulnerabilities and misconfigurations
Reveal Critical Impacts
NodeZero orchestrates hundreds of offensive security tools and chains weaknesses together to demonstrate the types of impacts attackers seek:
- Domain compromise
- Business email compromise
- Access to sensitive data exposure
- Ransomware
- Ability to pivot to the cloud
- And more!
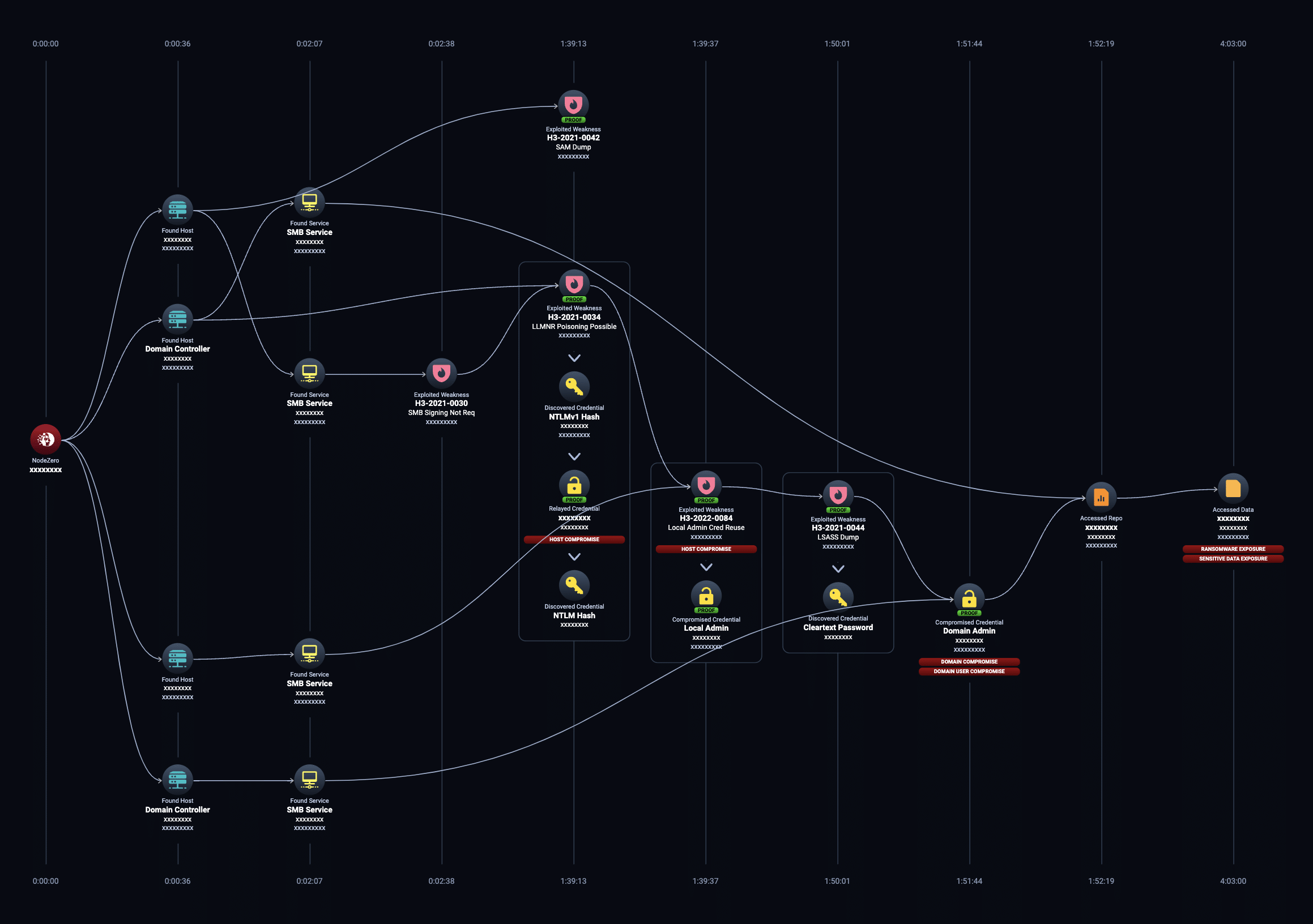
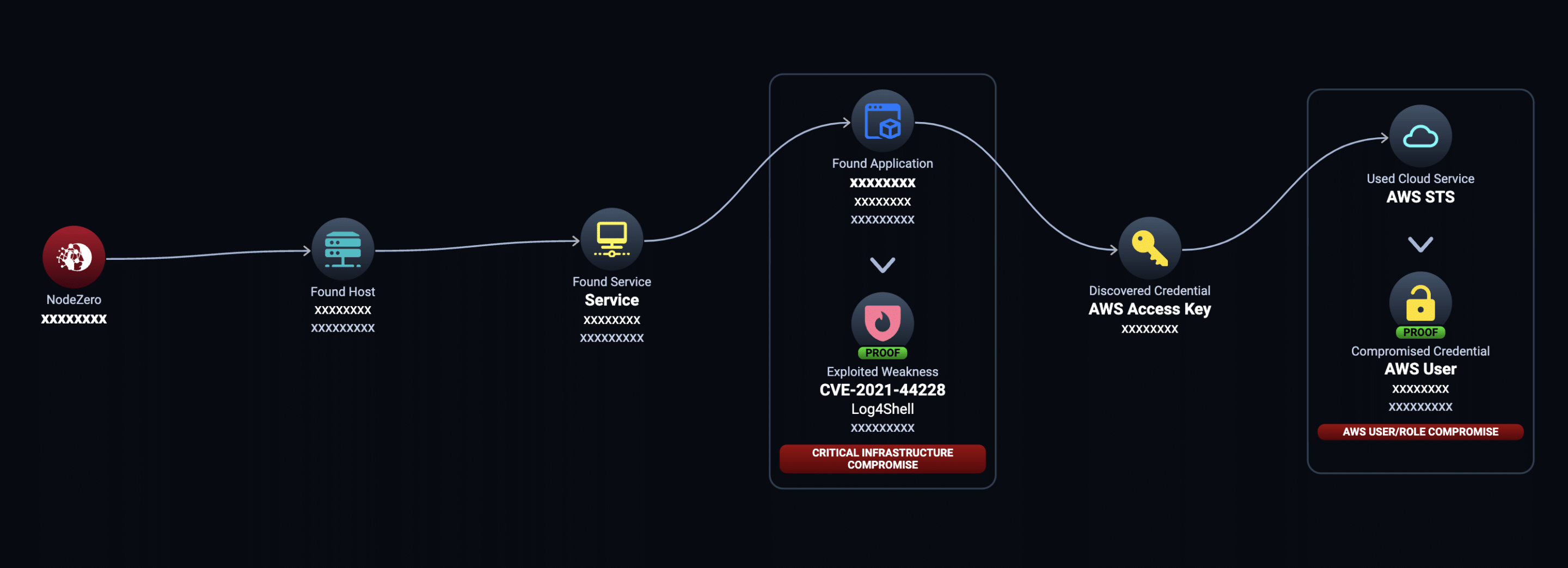
This real-world attack path shows an organization exposed to ransomware. NodeZero first compromised a domain admin account via a man-in-the-middle attack and credential dumping, and then used that account to access sensitive data.
Validate and improve your security posture, proactively protect against ransomware, and streamline your compliance initiatives.
High Speed
Kick off your NodeZero pentest in minutes instead of the weeks a manual pentest could take.
Low Maintenance
With a SaaS architecture, there’s no hardware or software to maintain and no required agents to install.
Safe by Default
Operate safely with the default settings.
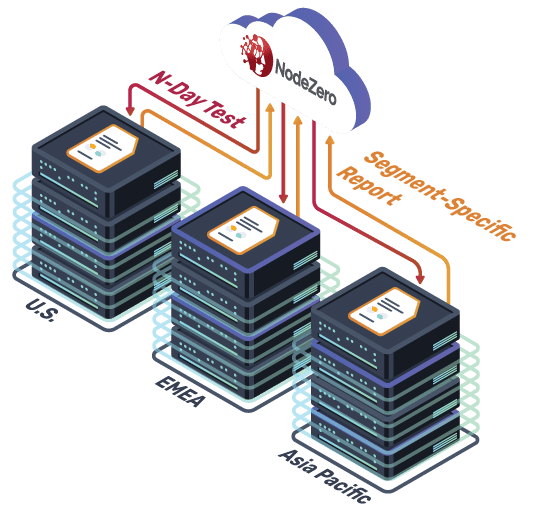
Test from different perspectives
Conducting pentests from different perspectives allows you to fully assess your network’s security. Think of NodeZero as helping you “threat model” your environment. You can test the impact of breaches in each of your network segments (server subnet, user subnet, DMZ, aka demilitarized zone, etc.) or data centers. You can also simulate what would happen if a specific user’s credential were compromised, allowing you to assess scenarios such as “What if an employee in my HR department was phished?” or “What if an employee in my IT department goes rogue?” You can also run a “black box” pentest, where NodeZero starts with no credentials and achieves initial access on its own.
Conduct large scale and concurrent testing
Unlike manual pentests, where less than one percent of a network is typically tested, NodeZero scales to support your largest networks. Your internal pentest options let you configure which IP ranges should be included and excluded in a test. You are empowered to test the whole private IP space (otherwise known as RFC 1918) if you want. You can also run multiple tests at the same time in different network segments for maximum efficiency.

Add OSINT to your testing
NodeZero can also make use of open-source intelligence (OSINT) to inform certain attacks, just like a real-world attacker might do. If you configure NodeZero with basic seed information such as your company name or domains, NodeZero will gather publicly available information related to your company and incorporate it into the pentest.
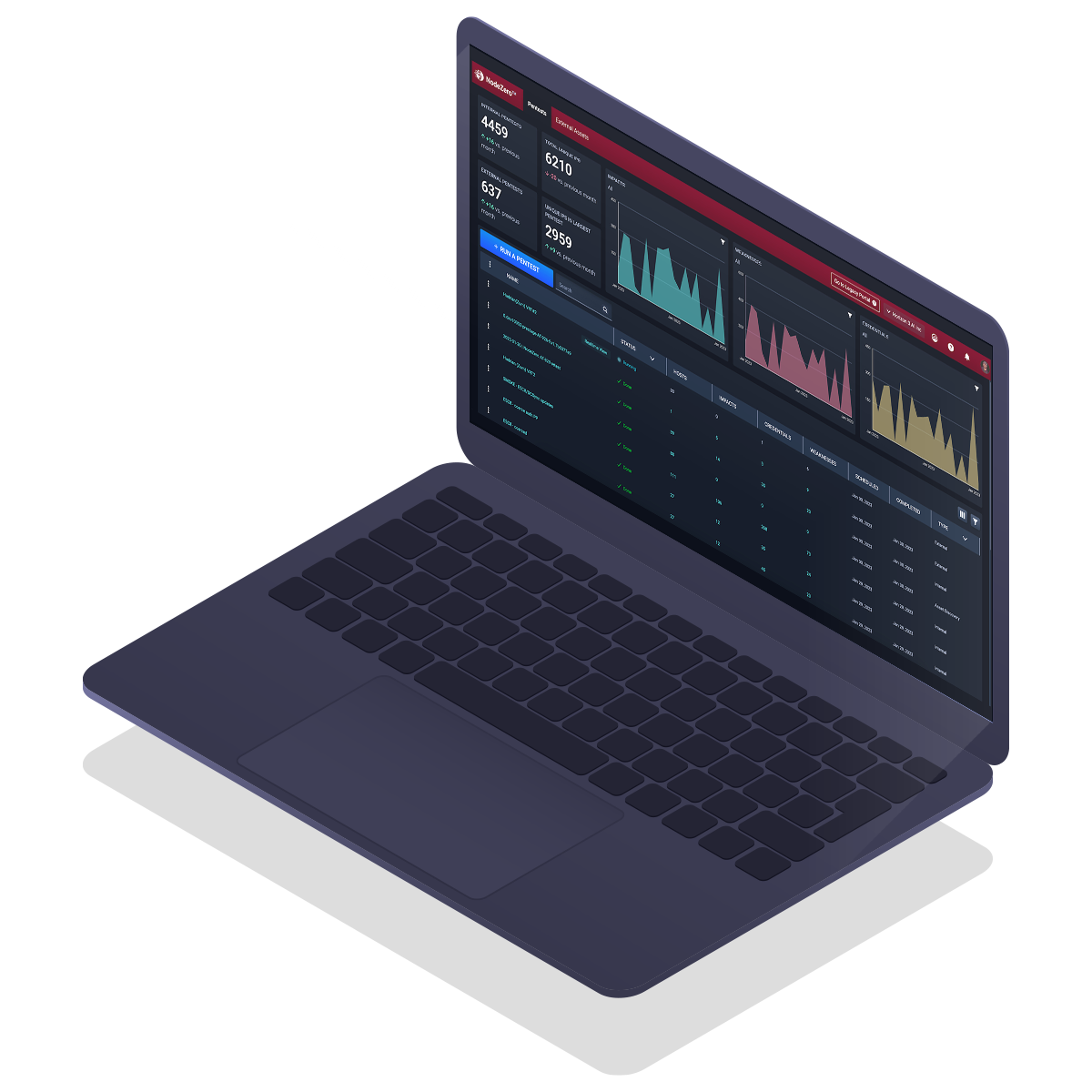
Internal Pentest Features
Discovers assets and enumerates your network
During the discovery/network enumeration phase of the test, NodeZero finds assets, which include hosts, devices, cloud services, and running applications. It fingerprints different types of network assets such as routers, domain controllers, VMware vCenter servers, and databases. The platform scans for open TCP (transmission control protocol) and UDP (user datagram protocol) ports and fingerprints the services running on those ports. It also fingerprints operating systems, web servers, and applications.
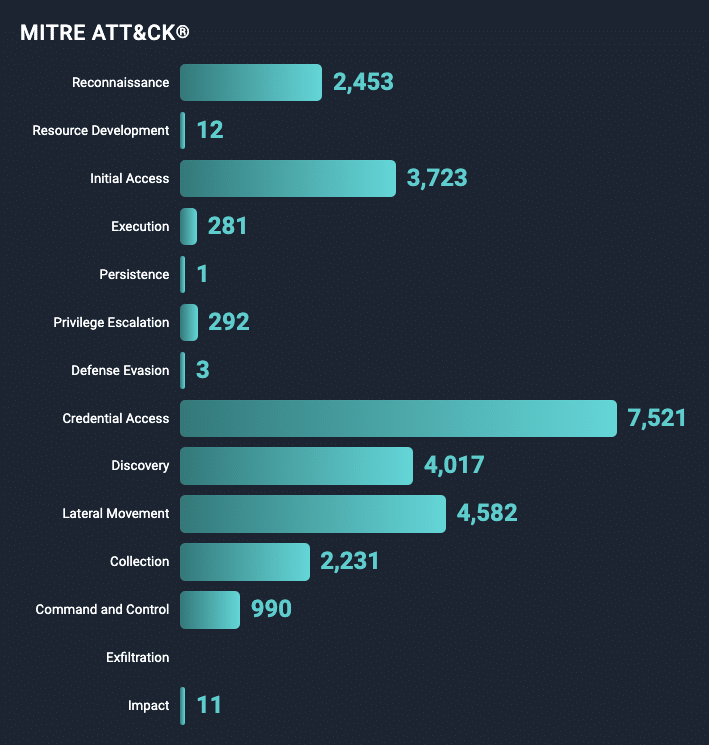
You can see how the attack modules used in your pentest align to the MITRE ATT&CK framework.
Goes far beyond CVEs
Find and eliminate the weaknesses that attackers can access in your internal network. NodeZero identifies and exploits critical weaknesses that go far beyond the common vulnerabilities and exposures (CVEs) that vulnerability scanners focus on. And unlike other automated tools, it autonomously chains the weaknesses together without a predefined script, behaving just as an attacker would, to move laterally through your network. Many of the attack paths NodeZero executes don’t involve exploiting any CVEs.
Once the test is complete, the scoring of the impacts and weaknesses reflects what NodeZero was able to accomplish. This is significantly different than the CVE scoring that vulnerability scanners use, where the score is static for every organization regardless of whether that vulnerability is actually exploitable or whether it could be combined with another weakness to disrupt your operations.
NodeZero also shows you how the attack modules used in your pentest align to the MITRE ATT&CK framework. The mapping includes the specific combination of a MITRE tactic, technique, and optionally a sub-technique.
Weaknesses uncovered in your internal pentest may include
- Vulnerable services
- Misconfigured network devices, servers, and applications
- Weak authentication
- Gaps in your security controls
- Data leakage
- Data exposure
- Weak network segmentation
- Exposed credentials
Vulnerable services running on network hosts that have known CVEs. NodeZero exploits these vulnerabilities to perform activities such as executing remote commands on the host, dumping credentials, or accessing sensitive data. New N-day tests are continually added to NodeZero.
Misconfigured network devices, servers, and applications that include weak passwords, default configurations, open ports, and insecure network settings.
Weak authentication mechanisms, such as default or easily guessable passwords. NodeZero attempts to exploit them to gain unauthorized access to systems or accounts.
Gaps in your security controls that NodeZero reveals with use of tactics, techniques and procedures to test whether your security controls are working as they should be. It may, for example, identify that your endpoint detection and response (EDR) tool didn’t prevent certain techniques for OS credential dumping.
Data leakage such as misconfigured file shares, insecure data transfer protocols, or weak access controls.
Data exposure including payment card information, social security card numbers, and other personally identifiable information (PII) that increases your risk of ransomware and can jeopardize your overall security and regulatory compliance.
Weak network segmentation such as misconfigured firewall rules or improper network zoning, which could allow unauthorized access between different network segments.
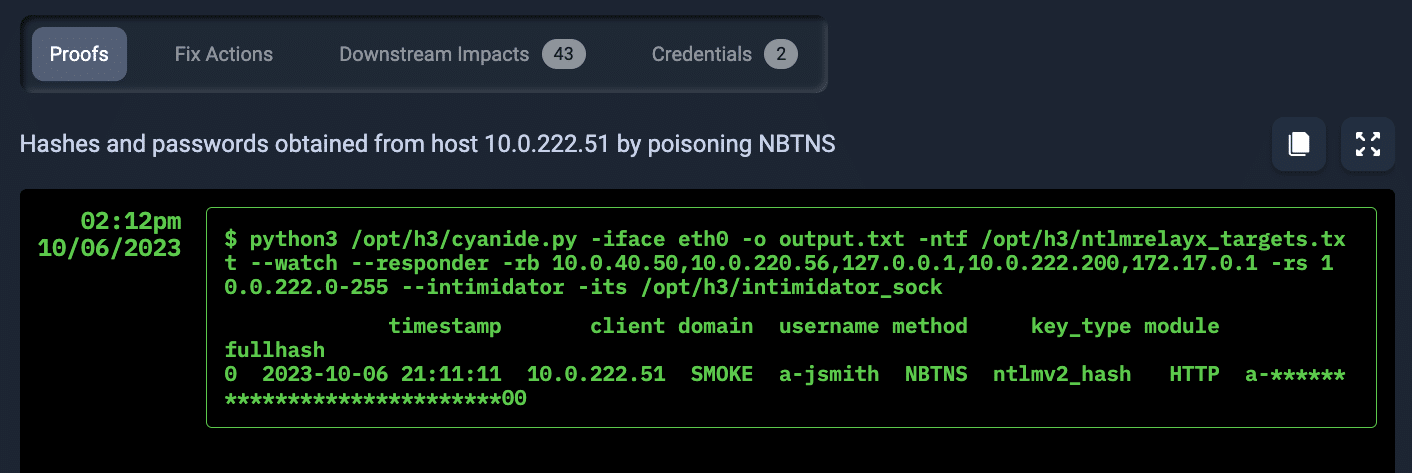
Exposed credentials include Man-in-the-middle (MiTM) attacks, password cracking, password spraying, and credential phishing where NodeZero harvests entered credentials from internal phishing campaign assets for further exploitation attempts. : NodeZero simulates executes various attack techniques to obtain login credentials from within the target network during an internal pentest. You can also run regular password audits with NodeZero.
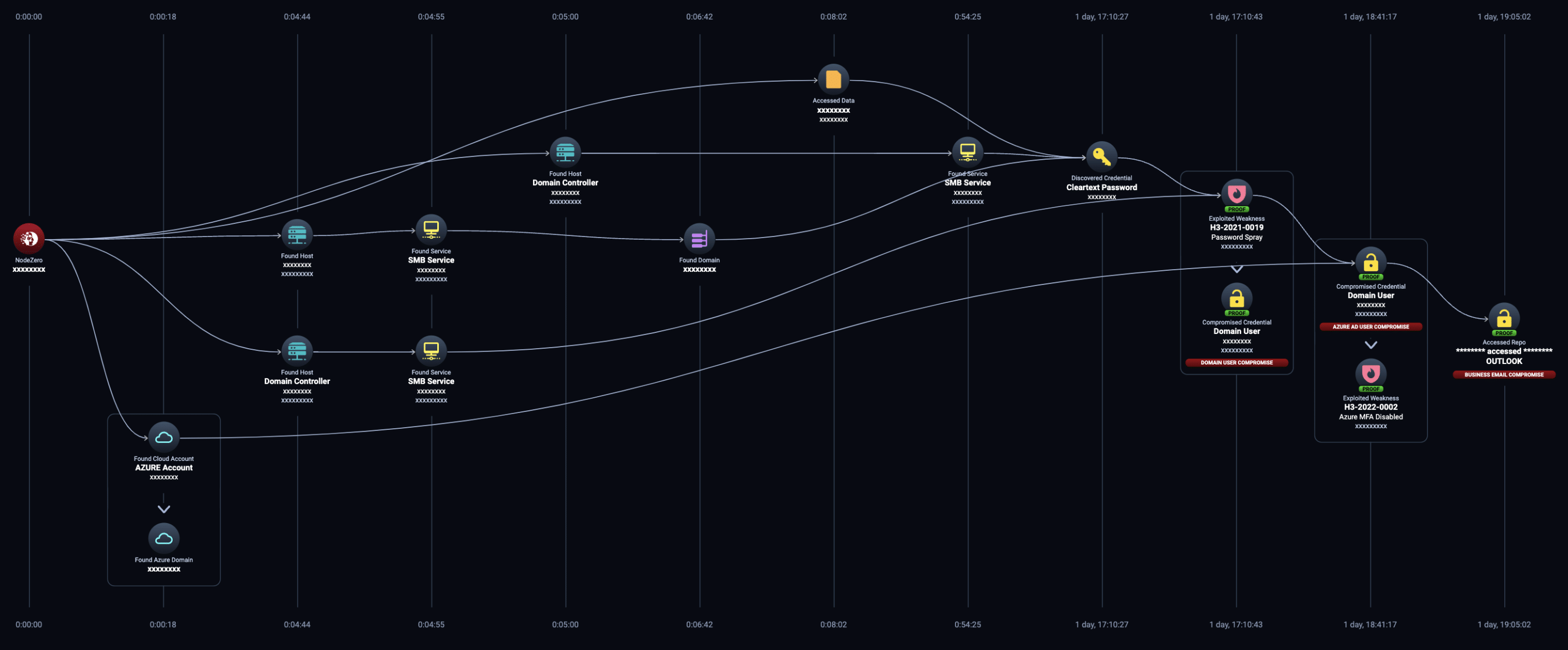
Pivots into the cloud
During your internal pentest, NodeZero will try to pivot into your cloud environments, identifying attack paths leading to the compromise of cloud assets and data hosted in the cloud. This includes Amazon S3 storage buckets, Amazon Elastic Compute Cloud (Amazon EC2) instances, Microsoft 365 cloud-based services, and Microsoft Azure virtual machines. These pivots expose weaknesses that could have significant impact on your organization.
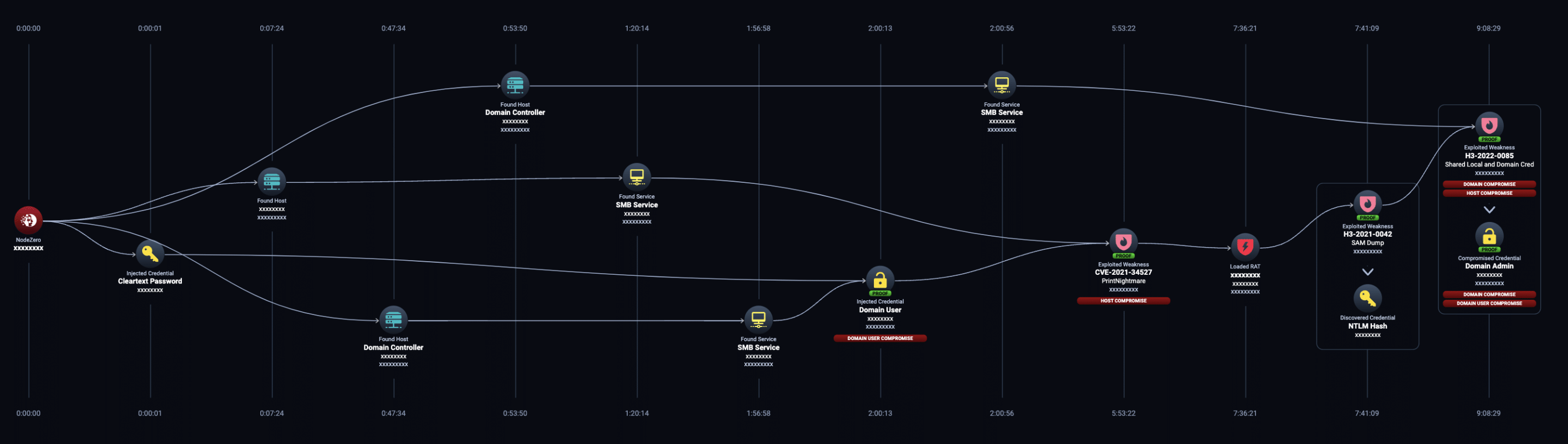
In this real-world attack path, NodeZero exploited a PrintNightmare vulnerability to install the NodeZero RAT and then used the RAT to dump credentials for the domain admin account. The result is full domain compromise.

Conducts advanced post-exploitation with NodeZero RAT
NodeZero implants and orchestrates remote access tools (RATs) into internal pentests. This feature allows the platform to leverage detected weaknesses and vulnerabilities that could then be used by attackers to achieve remote access. Once the platform has access, it continues to explore available attack paths, such as credential dumping, and assesses the impact on your organization. NodeZero implants these RATs to conduct more extensive post-exploitation on hosts, including common MITRE ATT&CK® techniques such as system information gathering and credential dumping.
In this real-world attack path, NodeZero exploited a PrintNightmare vulnerability to install the NodeZero RAT and then used the RAT to dump credentials for the domain admin account. The result is full domain compromise.
Provides full transparency of the test elements and results
NodeZero provides you with full transparency during your internal pentest so you know precisely what exploits are being run and can tell which hosts or users NodeZero has compromised.
After the pentest is complete, NodeZero delivers a clear and prioritized summary of the impact of the test findings on your organization. You have complete visibility into proven attack paths with step-by-step summaries of each path, including the points where credentials were compromised or remote access tools were used midstream. For every weakness identified, you can see the proofs showing that it was exploited by NodeZero, along with downstream impacts that arose from exploiting the weakness, and fix actions for remediating it.

Delivers meaningful reporting
NodeZero has a rich – and always growing – set of available reports for you to use throughout your workflow. They include:
- Executive Summary
- Pentest report
- Segmentation report
- Fix Actions Report
Reports are easily customized and co-branded.
Continuous
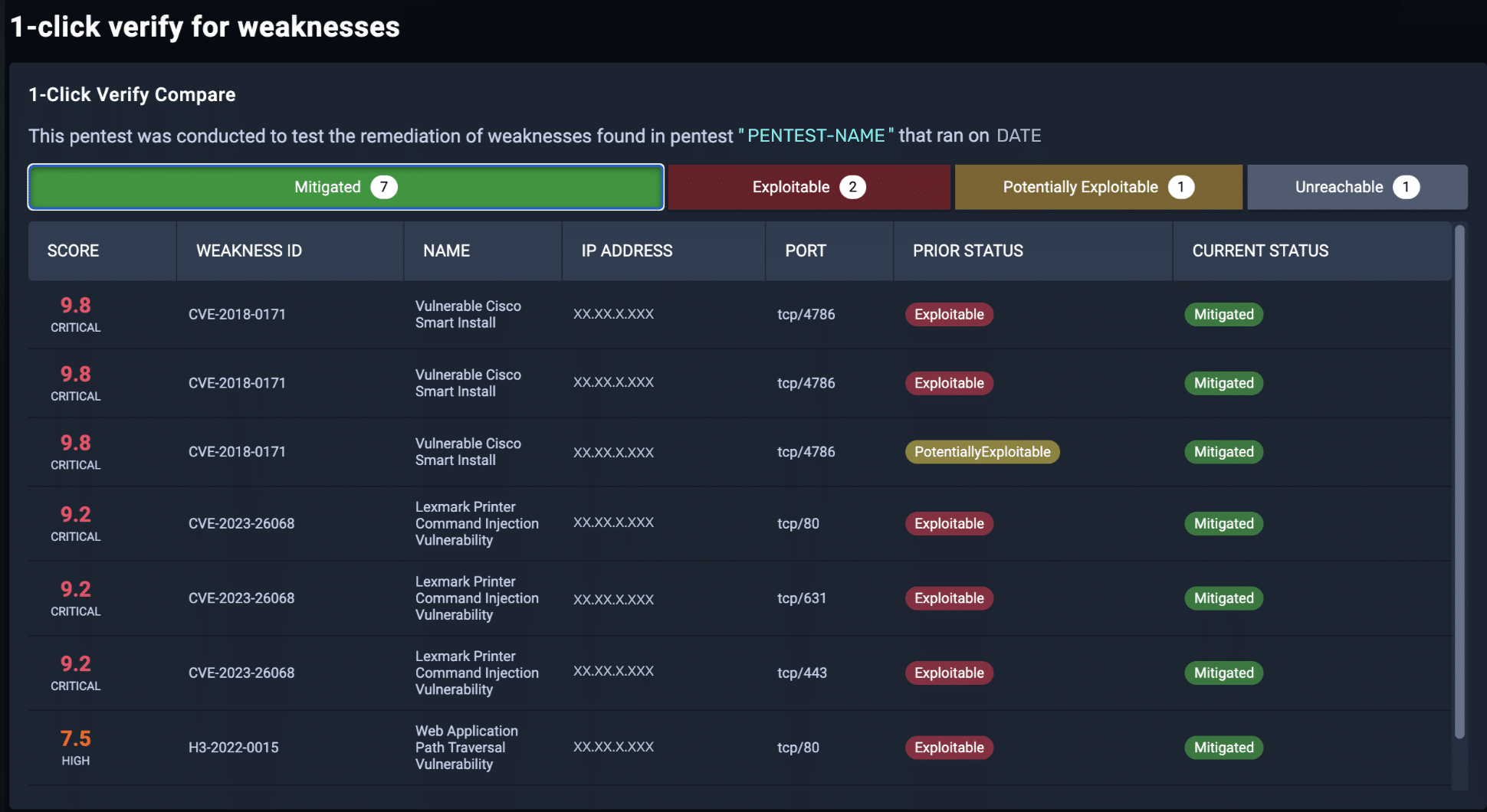
Don’t just rely on a point-in-time pentest. Continuously assess your security posture, and quickly compare NodeZero results to verify your fixes and identify new weaknesses.
You can easily create a schedule so that your pentests run automatically on a recurring basis once a week (recommended) or whatever time frame you choose. This delivers continuous autonomous pentesting without any user intervention – no need to launch the tests, or even sign in to the portal to initiate them.
Get started now!