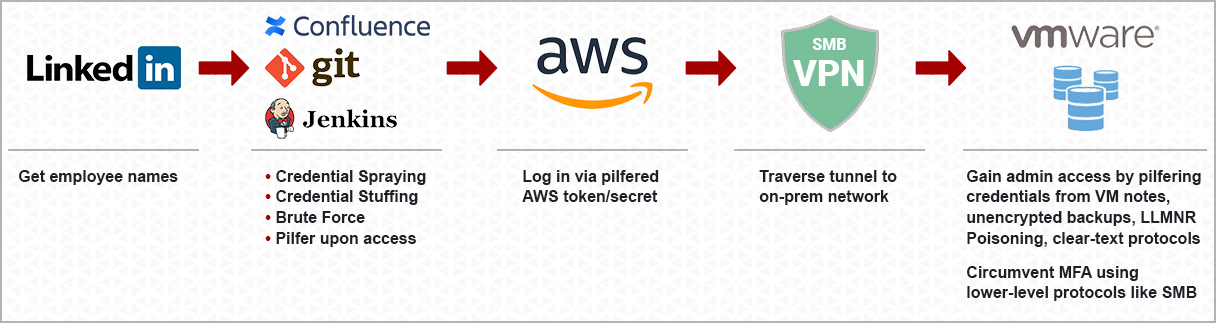
Credential Attacks

Attackers don’t hack in, they log in.
Attackers usually don’t have to hack into your systems like in the movies; oftentimes, they log into your systems like valid users using credential attacks.
What are credential attacks?
Attackers collect usernames
Exploit poor password policies to obtain domain user credentials
Leverage misconfigurations to elevate privileges to domain administrator
…where they end up with the keys to the kingdom.