Audit Your Password Exposure with NodeZero
Attackers don’t hack in, they log in.
Compromised credentials underpin a high percentage of cyber attacks. To make sure you’re not leaving a welcome mat out for bad actors, you should continually verify the effectiveness of your credential policies. NodeZero AD Password Audit offers you a fast and effective method for uncovering any gaps in your password policy and streamlining your remediation.
Reveals user passwords in your Active Directory (AD) environment that are likely targets for credential stuffing, password spray, credential reuse, and password cracking attacks.
Cracks passwords based on public breach data, open source intelligence (OSINT) tied to your company, and any weak password terms that you can provide.
Provides a prioritized list of risky accounts along with detailed remediation guidance.
Enables you to regularly audit passwords as employees join or leave your organization.
CISA testing estimates that valid accounts can be successfully used to gain network access 54% of the time.
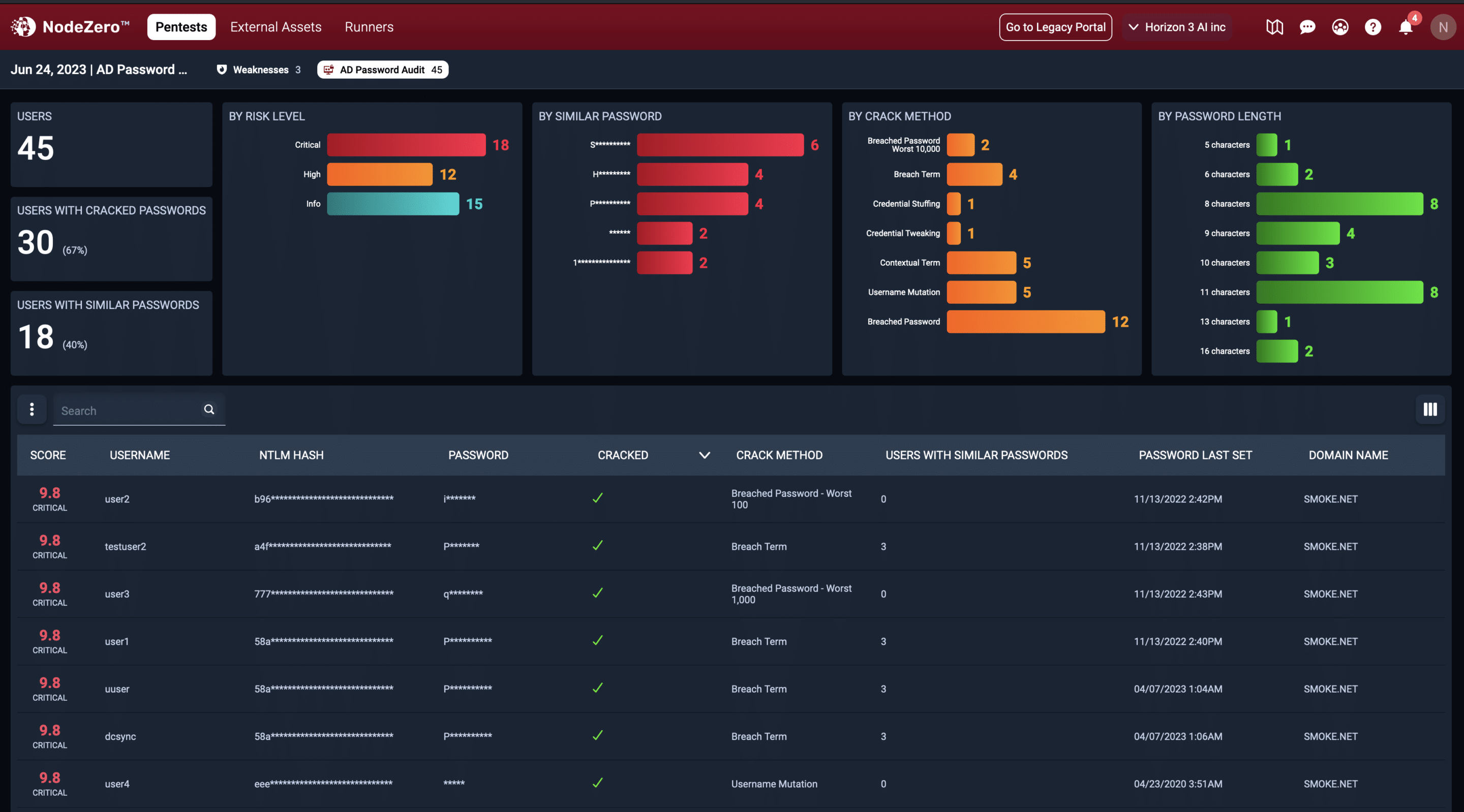
The audit ranks all users audited by their risk level, which is a function of guessability, how the password was cracked, and password similarity.
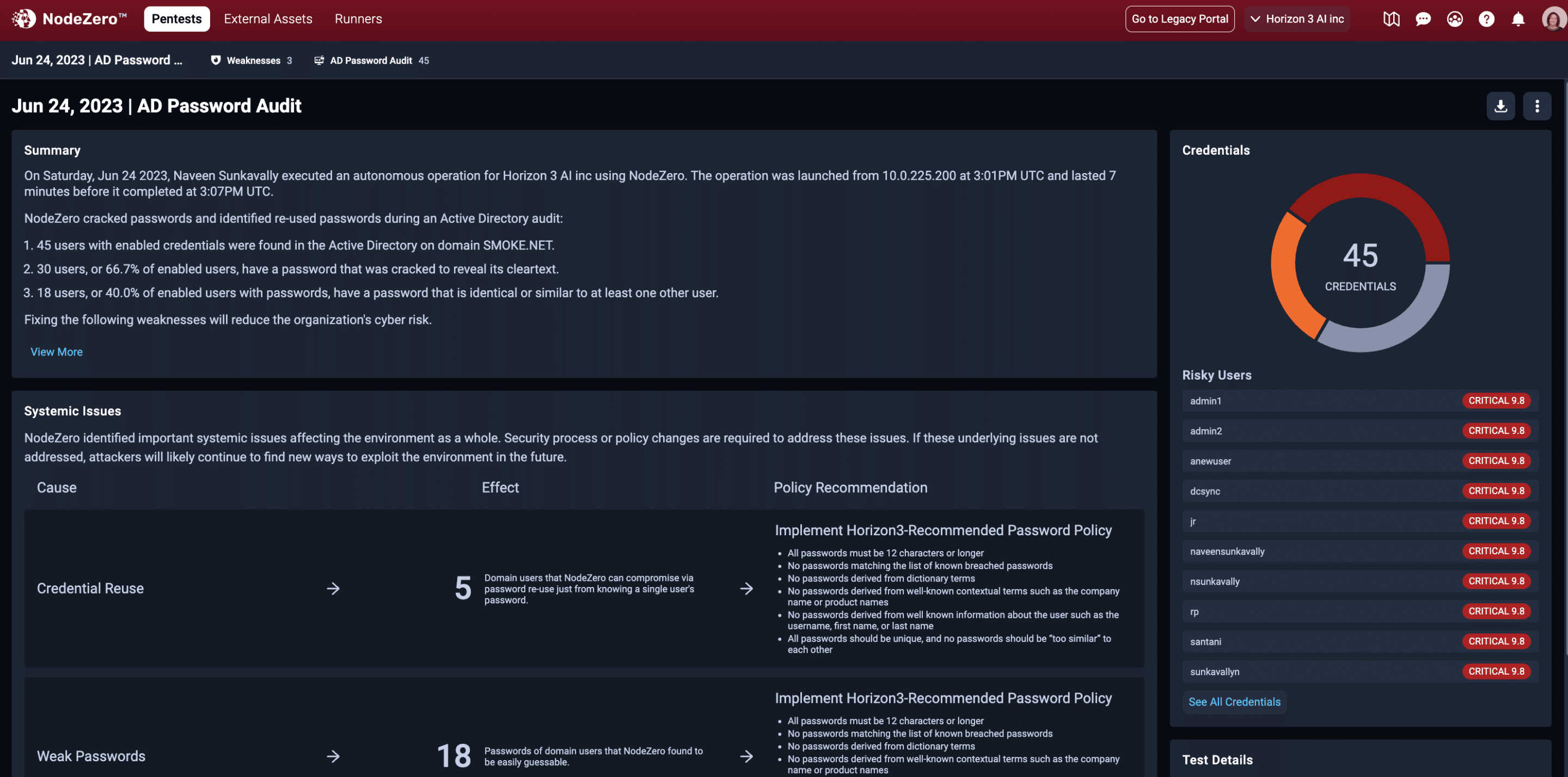
When the audit is complete, NodeZero gives you a detailed and actionable summary and ranks your users by their credential risk. You can drill into specifics, and NodeZero provides the proof that the password was cracked, as well as mitigation steps and guidance for improving your overall password policy.
The audit ranks all users audited by their risk level, which is a function of guessability, how the password was cracked, and password similarity.
Why are password audits important?
Cyber threat actors commonly use valid accounts for initial access, lateral movement, and privilege escalation. The CISA Analysis: Fiscal Year 2022 Risk and Vulnerability Assessments finds valid accounts can be used to:
Gain initial access 54.3% of the time.
Maintain persistence 56.1% of the time.
Escalate privileges 42.9% of the time.
“To guard against the successful Valid Accounts technique, critical infrastructure entities must implement strong password policies, such as phishing-resistant MFA, and monitor access logs and network communication logs to detect abnormal access. Swift identification of abnormalities can reduce damage caused by a cyber intrusion,” the analysis says.
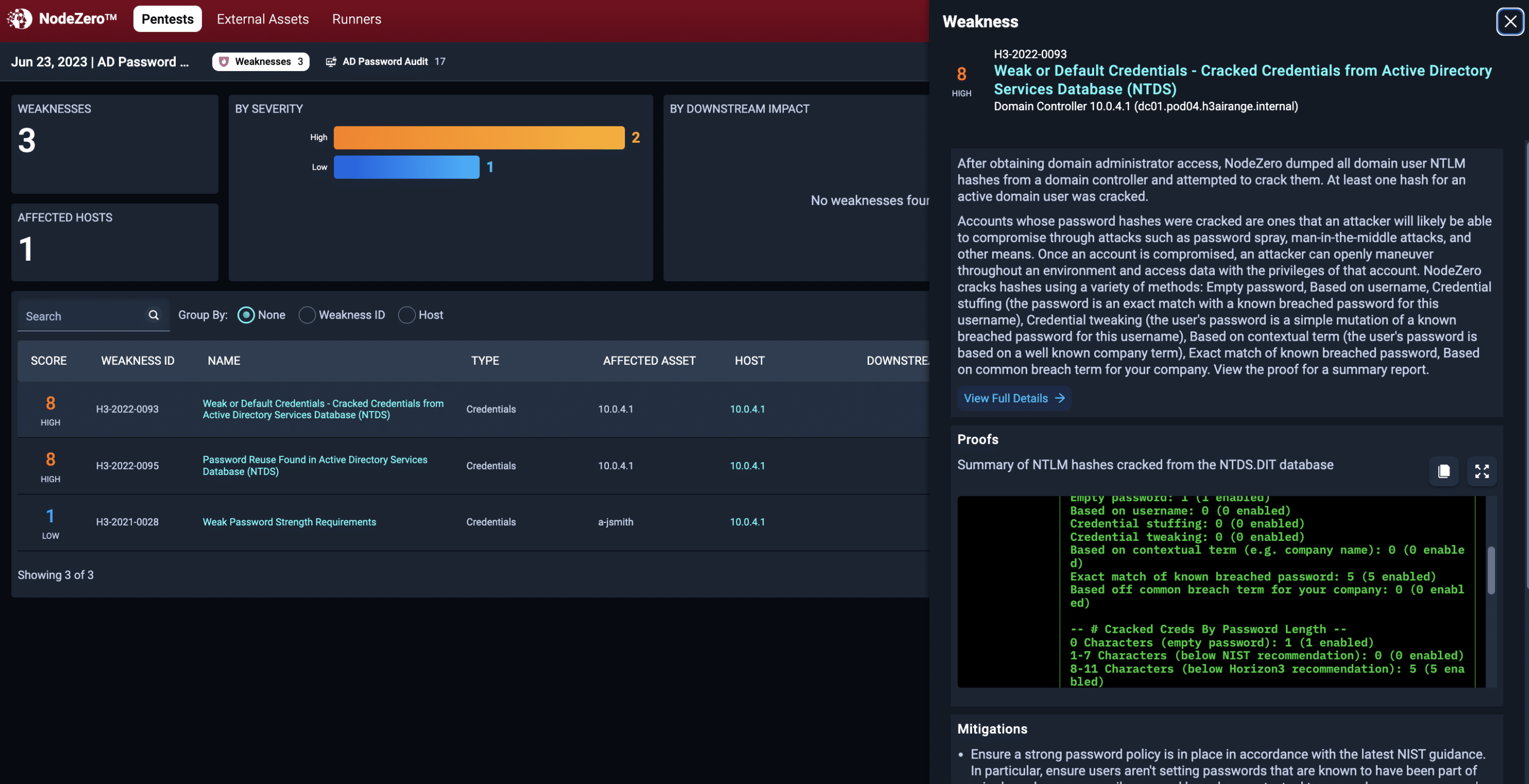
Poor password policies and lack of best practices enforcement remain an issue in most organizations. In real-world tests, it’s not uncommon for NodeZero to crack more than 50% of the passwords it tests as part of an initial audit, and to find hundreds of accounts sharing the same password.
With NodeZero, you can easily and regularly audit your organization and receive prioritized guidance for your riskiest accounts. NodeZero rates accounts with easily guessable passwords as critical. These accounts are the ones most at risk of being compromised by online attacks such as password spray and credential stuffing.
In this example, NodeZero AD Password Audit identified 30 users with cracked passwords, 18 users with similar passwords that should be updated, and prioritized the risk levels for the passwords examined. Crack methods included Worst 10,000, Breach Terms, Credential Stuffing, Credential Tweaking, Contextual Terms, Username Mutation, and Breached Password.
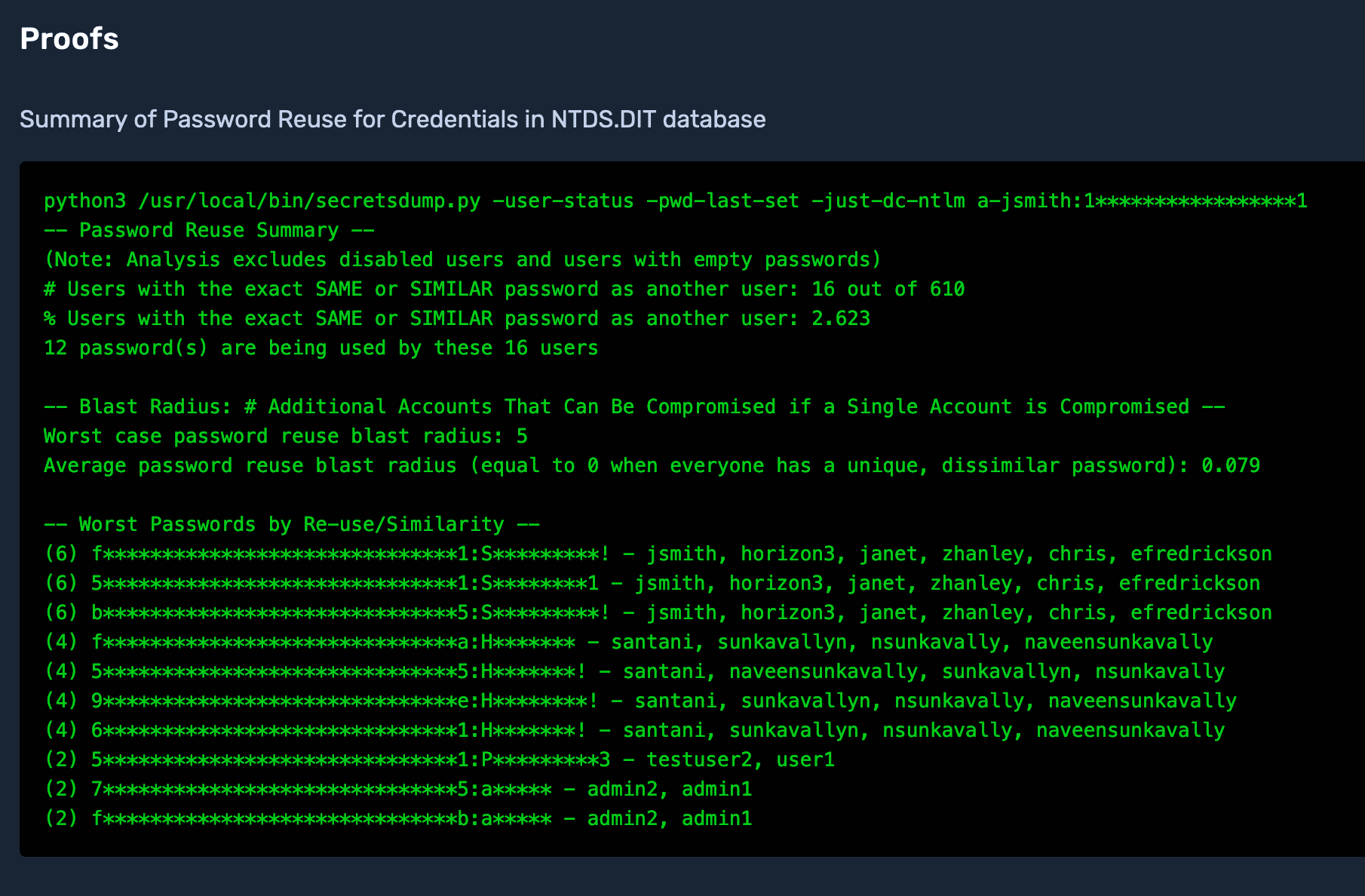
Blast Radius Impact
Credential reuse is a simple and common technique that attackers use to gain access to more Valid Accounts.
NodeZero AD Password Audit compares all account passwords to see how similar they are to each other. It then determines the number of additional accounts that can be accessed from a particular compromised credential in a novel metric known as “blast radius.”
NodeZero assumes an attacker can simply take a compromised password or simple variation of it and attempt to use it against other accounts. With the blast radius metric, you can defend against credential reuse attack techniques.
Remediation
A Fix Action Report is delivered with the results of your AD Password Audit operation. NodeZero provides:

Risky accounts that require immediate attention in a prioritized list
Guidance on how to improve your password policy in accordance with National Institute of Standards and Technology (NIST) standards
Output you can feed into other tools, like Splunk, to investigate attacker use of risky accounts in the past
You can also use your NodeZero audit results to create a remediation workflow to take specific actions: increased monitoring of risky accounts, for example, or resetting risky passwords.
It’s Easy to Get Started
When setting up your AD Password Audit, you are asked to enter a single IP address, add a credential, and basic information about your company such as its name and domain name. With that information, NodeZero uses OSINT to add more context about your company — context that an attacker may be able to leverage to guess weak passwords.
NodeZero uses your company domains to look up dark web data associated with your company. If you have any well-known weak passwords at your company that you want to weed out, you can add them into the “Weak Password Terms” section and NodeZero will attempt to use them (and variations of them) while cracking.
Evaluate your credential exposure today with your NodeZero free trial

Want to learn more about why the metrics that NodeZero shows you in AD Password Audit really matter?
In his blog, Metrics That Matter: An Attacker’s Perspective on Assessing Password Policy, Naveen Sunkavally, Chief Architect at Horizon3.ai, explains how to gauge the strength of your organization’s password policy against common attacker techniques like password spray, credential reuse, and password cracking.