After compromising a Windows domain controller, one of the actions that NodeZero, our autonomous pentest product, performs is dumping all domain user password hashes from the Active Directory database. This is a common attacker technique, and the resulting dump is highly valuable to attackers. But did you know that this data is a great source of insight for defenders too?
In this post we’ll talk about different metrics NodeZero gathers from analyzing password hashes in the Active Directory database. You’ll see how these metrics can be used to gauge how susceptible your organization is to common attacks that take advantage of weak passwords: password cracking, password spray, and credential re-use. These metrics can then be used as a lever to adjust password policy, improving the long-term cyber resilience of your organization.
Credential Analytics
Password Cracking Metrics
After dumping password hashes from a domain controller, NodeZero attempts to crack them all. This cracking is done without the need to set up dedicated hardware (i.e. GPUs). NodeZero uses a regularly updated wordlist containing billions of potential passwords, including all publicly disclosed breached passwords. NodeZero also tries to crack hashes based on contextual terms such as a company’s name and domain names.
If NodeZero is able to crack any hashes for active users, NodeZero will surface a weakness entitled Weak or Default Credentials - Cracked Credentials from Active Directory Services Database (NTDS).
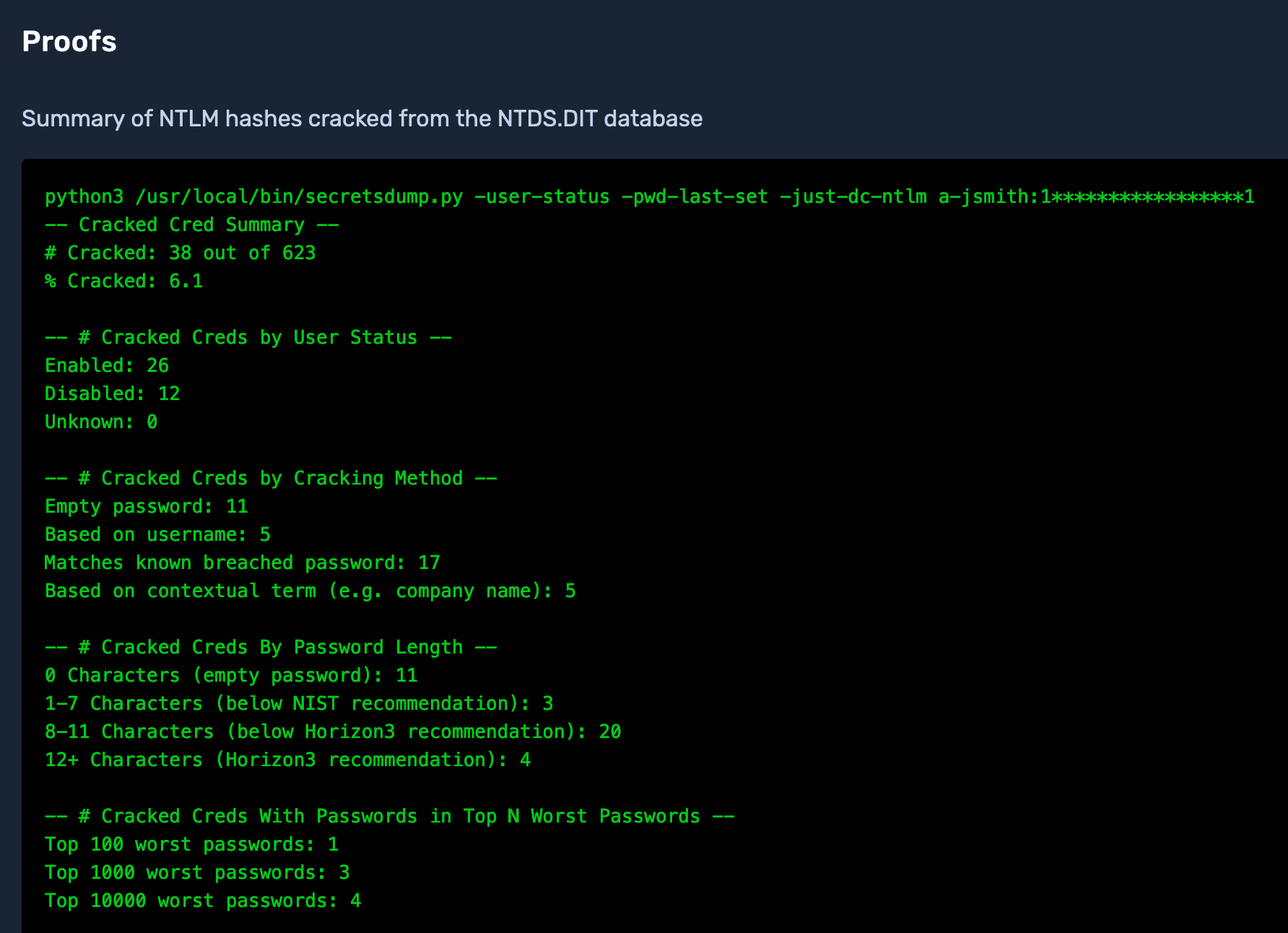
The proof for this weakness will contain a summary report with metrics covering:
-
Number and percentage of users whose password hashes were cracked
-
Number of cracked accounts broken down by user status (enabled or disabled)
-
Number of cracked accounts broken down by cracking method (empty password, based on username, known breached password, or using a contextual term).
-
Number of cracked accounts broken down by password length
-
Number of cracked accounts with passwords appearing in the list of the top 100, top 1000, and top 10000 worst known passwords
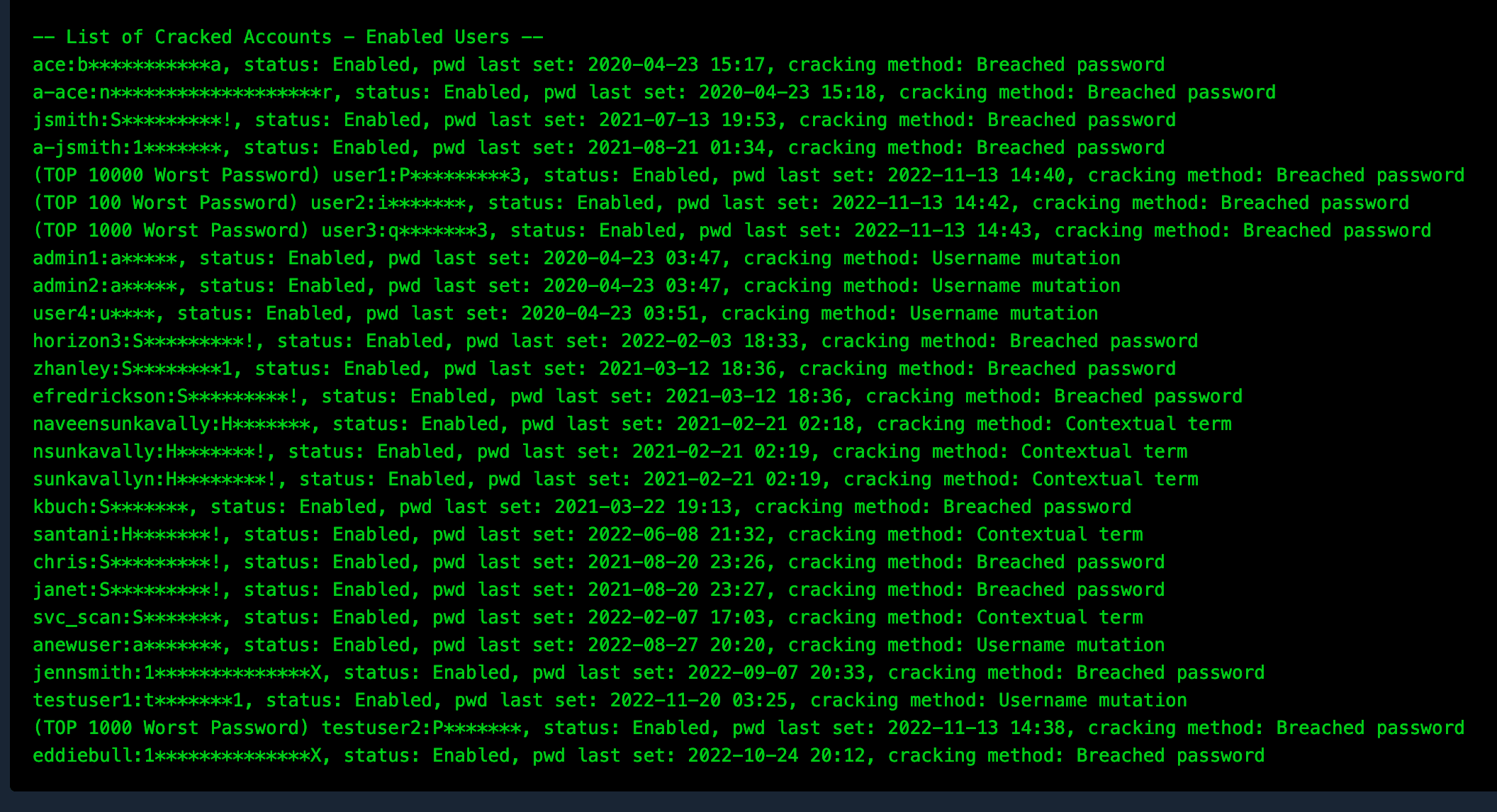
Also included in the proof is the list of active accounts whose passwords were cracked and the methods used to crack them.
Password Similarity Metrics
In addition to hash cracking, NodeZero analyzes the data dump for password reuse: cases where different users are using the exact same or similar passwords. If at least two active users are found to be using the exact same or similar password, NodeZero surfaces a weakness entitled Password Reuse Found in Active Directory Services Database (NTDS).
Password reuse analysis can be done even if no passwords are cracked. Password hashes are dumped from the Active Directory database in NTLM format, which are unsalted MD4 hashes of the passwords. This means that two accounts with the same NTLM hash are using the same password.
If NodeZero is able to crack any password hashes, it goes one step further in its analysis. It compares cleartext passwords with each other to see how similar they are based on the normalized edit distance metric. If two cleartext passwords are at least 70% similar, then NodeZero presumes that an attacker would be able to guess one password from the other.
For instance, suppose we’re comparing two cleartext passwords: Horizon3 and Horizon1!. The edit distance between these two passwords is 2, because 2 modifications are required to turn the first password into the second.
-
Horizon3 → Horizon1 (replace 1 with 3)
-
Horizon1 → Horizon1! (add !)
Based on this, NodeZero determines that these two passwords are ~78% similar – close enough for an attacker to easily guess.
Using this type of analysis, NodeZero surfaces the following metrics in the proof for the Password Reuse weakness.
-
Number and percentage of active users using a password similar to another user
-
Worst case and average age password reuse “blast radius”
-
This is a novel metric NodeZero surfaces to indicate the number of additional accounts that can be compromised if a single account is compromised. NodeZero assumes an attacker can simply take a compromised password or simple variation of it and attempt it against other accounts.
-
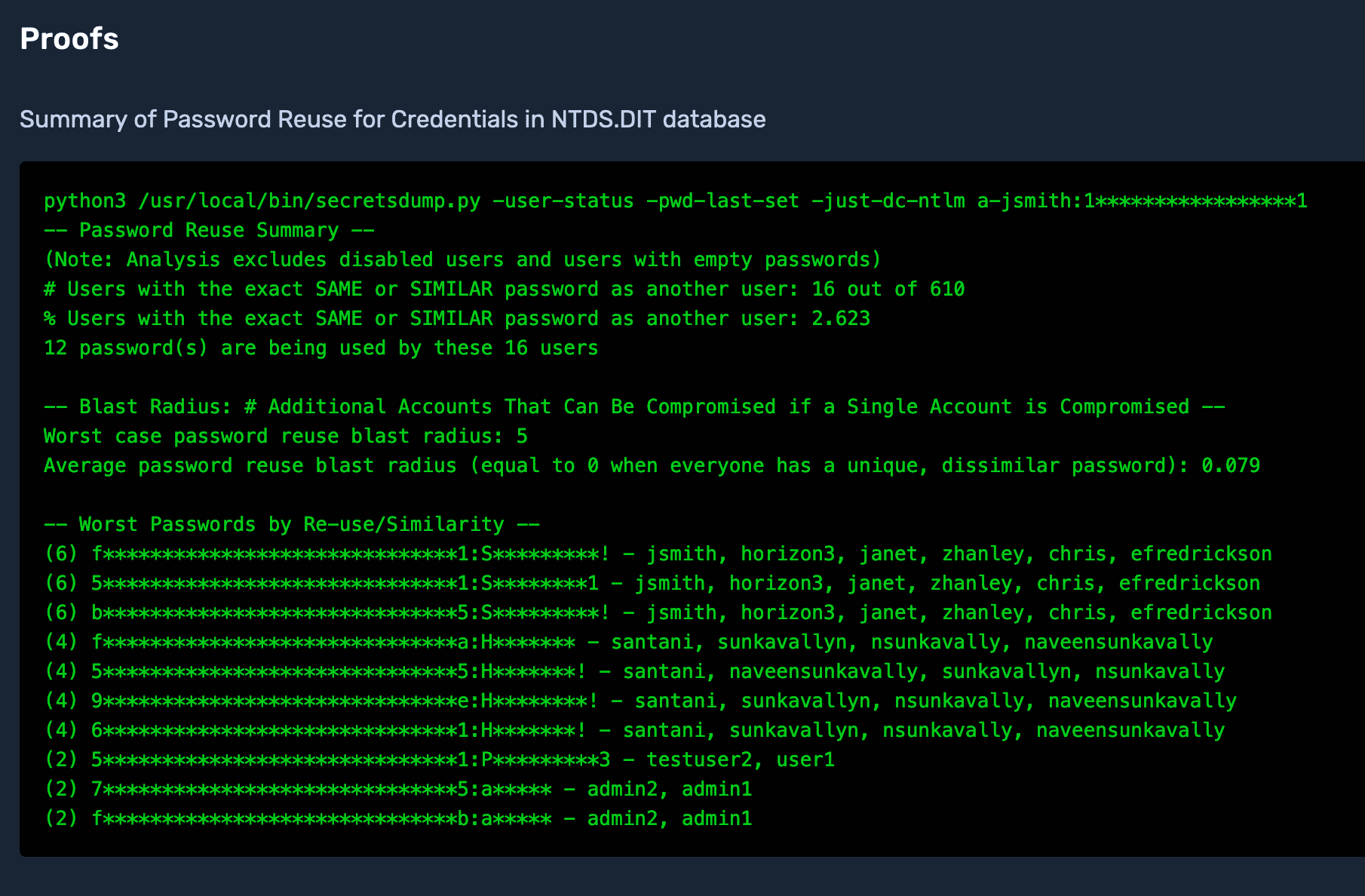
The top reused passwords are also provided in the proof.
Using Metrics to Gauge Attack Defense Readiness
Now let’s talk about how the metrics above can be used to assess an organization’s susceptibility to different types of attacks.
Defending Against Password Spray Attacks
In a password spray attack, an attacker starts with a list of users and a shortlist of probable weak passwords. The attacker tries (i.e. “sprays”) each password, one at a time, against all users in an attempt to compromise at least one account. Attackers are just trying to take over any account because they know that, once they’ve compromised a single account, they can abuse that account’s access to go further into the network. Password spray attacks are carried out both for initial access and lateral movement.
To avoid account lockouts, attackers usually perform password sprays over long periods of time, limiting the rate of login attempts. Suppose an attacker has a shortlist of 10000 passwords and is spraying at a rate of 4 attempts per hour. It would take the attacker more than a 100 days to complete the spray. This means, to defend against password spray attacks, it’s most important to eliminate any easily guessable passwords that would make an attacker’s shortlist to spray. Even if a password hash is cracked, it doesn’t mean it’s easily guessable – it could be entry number 100,000,000 in a breached password list, and an attacker won’t realistically have the time to attempt that password.
So the metrics that matter most for guarding against password spray attacks are:
-
# Accounts cracked with passwords that appear in the list of top 10000 known worst passwords
-
# Accounts cracked with passwords that are derived from a user’s username
-
# Accounts cracked with passwords derived from a contextual term such as a company name
-
# Enabled accounts with empty passwords
Weak passwords in all of the above categories are ones attackers can easily come up with to generate a shortlist for spraying.
Defending Against Password Cracking Attacks
In a password cracking attack, an attacker has a password hash in hand and seeks to crack it to recover the cleartext. An attacker typically acquires hashes after initial access through attacks such as OS credential dumping, Kerberoasting, or LLMNR/NBT-NS Poisoning.
It is generally hard to defend against password cracking because motivated attackers may have significant cracking hardware at their disposal. Cracking hardware has matured to the point now that an NTLM hash for any password 8 characters or less can be cracked within a few hours or less. There are even publicly available rainbow tables for all NTLM hashed passwords of 9 characters.
If NodeZero was able to crack any hashes at all, you can expect an attacker will also be able to crack them. It’s not unusual for NodeZero to crack more than 50% of an organization’s credentials.
The single best defense against password cracking attacks is to require long passwords. We recommend passwords at least 12 characters in length. This is more than NIST’s guidance of an 8 character minimum.
The metrics that matter most for defending against password cracking attacks are:
-
# Accounts cracked (total amount)
-
# Accounts cracked with password length < 12 characters
Defending Against Credential Reuse Attacks
In a credential reuse attack, an attacker starts with a compromised account and tries to take over other accounts by trying to login with the same password, or a similar password. This is typically carried out as part of lateral movement.
Organizations routinely have a common password or base term that is shared across many accounts. For instance, this base term could be derived from the password new users get when they first join an organization, or a temporary password used as part of a password reset, or a password used for test accounts.
If an attacker is able to compromise a single account using one of these common passwords, you can assume that all other accounts that share that password can also be easily compromised. An attacker may be able to significantly escalate his or her privileges depending on the level of access those additional accounts have.
The Password Reuse Blast Radius metric tracks the number of additional accounts that can be taken over if a single account is compromised. Below are the trackable metrics most useful to defend against the credential re-use attack technique.
-
Worst case password reuse blast radius
-
Average password reuse blast radius
It’s not uncommon for NodeZero to find hundreds of accounts sharing the exact same password or passwords derived from a single base term. Ideally all accounts should be using a unique and dissimilar password.
A Plan For Continuous Assessment and Improvement
The Metrics That Matter
The following chart summarizes the metrics gathered by NodeZero and how they can be used to assess your organization’s posture against different types of attacks.
|
Password Spray |
Initial Access Lateral Movement Credential Access |
# Accounts cracked with passwords that appear in the list of top 10000 known worst passwords |
|
|
# Accounts cracked with passwords that are derived from a user’s username |
|
|
|
# Accounts cracked with passwords derived from a contextual term such as a company name |
|
|
|
# Active accounts with empty passwords |
|
|
Password Cracking |
Lateral Movement Credential Access |
# Accounts cracked (total amount) |
|
|
# Accounts cracked with password length < 12 characters |
|
|
Credential Reuse |
Lateral Movement Credential Access |
Worst case password reuse blast radius |
|
|
Average password reuse blast radius |
Horizon3’s Password Policy Recommendations
Based on the above, Horizon3 recommends the following organizational password policy. Our guidance extends and hardens the latest recommendations from NIST Special Publication 800-63B.
- All passwords must be 12 characters or longer
- No passwords matching the list of known breached passwords
- No passwords derived from dictionary terms
- No passwords derived from well-known contextual terms such as the company name, product, etc
- No passwords derived from well known information about the user such as the username, first name, or last name
- All passwords should be unique, and no passwords should be “too similar” to each other
We recommend a program of continuously running NodeZero to verify your posture and adherence to password policy. NodeZero automatically surfaces the metrics in this post whenever it acquires domain admin rights, or if it’s set up to run with a domain admin credential. Check out the free trial here to learn more!




