Summary
CVE-2023-39143 is a critical vulnerability we disclosed to PaperCut that affects the widely used PaperCut NG/MF print management software. It affects PaperCut NG/MF running on Windows, prior to version 22.1.3. If you are a user of PaperCut on Windows, and have it exposed to the Internet, we recommend you check out the July 2023 PaperCut security bulletin and immediately patch to the latest version if you haven’t already.
Impact
CVE-2023-39143 enables unauthenticated attackers to potentially read, delete, and upload arbitrary files to the PaperCut MF/NG application server, resulting in remote code execution in certain configurations.
In particular, the vulnerability affects PaperCut servers running on Windows. File upload leading to remote code execution is possible when the external device integration setting is enabled. This setting is on by default with certain installations of PaperCut, such as the PaperCut NG Commercial version or PaperCut MF.
Based on sample data we have collected at Horizon3 from real-world environments, we estimate that the vast majority of PaperCut installations are running on Windows with the external device integration setting turned on.
Exploitability
PaperCut has been on the radar of threat actors. Threat actors launched campaigns earlier this year targeting PaperCut servers vulnerable to CVE-2023-27350, a previously disclosed unauthenticated remote code execution vulnerability.
Compared to CVE-2023-27350, CVE-2023-39143 also does not require attackers to have any prior privileges to exploit, and no user interaction is required.
In contrast to CVE-2023-27350, CVE-2023-39143 is more complex to exploit, involving multiple issues that must be chained together to compromise a server. It is not a “one-shot” RCE vulnerability.
Detection
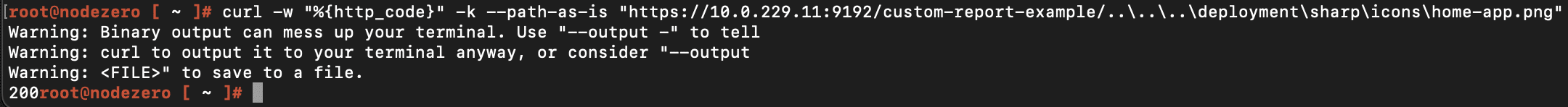
The following command checks if a PaperCut server is not patched and running on Windows.
curl -w "%{http_code}" -k --path-as-is "https://<IP>:<port>/custom-report-example/..\..\..\deployment\sharp\icons\home-app.png"
A 200 response indicates the server has not been patched and is running on Windows. A 404 response indicates the server has been patched or not running on Windows.
We are not releasing further details at this time to provide users adequate time to upgrade.
Remediation
We recommend upgrading to the latest PaperCut NG/MF version, 22.1.3 as of this writing.
If upgrading is not possible, it is possible to mitigate this vulnerability by configuring an allowlist of device IP addresses that are permitted to communicate with the PaperCut server. Refer to the “IP Address Allow-listing” section of the PaperCut security best practices guide.
Timeline
- May 30, 2023: Horizon3 sends initial disclosure to the PaperCut team
- May 31, 2023: PaperCut acknowledges receipt of disclosure
- June 5, 2023: Horizon3 updates disclosure to include impact of remote code execution
- June 8, 2023: PaperCut confirms it is able to validate findings in disclosure
- June/July 2023: Horizon3/PaperCut work together to test interim builds and coordinate disclosure
- July 24, 2023: Horizon3 reserves CVE-2023-39143 with MITRE
- July 25, 2023: PaperCut releases patch version 22.1.3
- Aug. 4, 2023: This advisory
We’d like to extend our thanks to the PaperCut team for their prompt response and close collaboration to address this vulnerability.



