Introduction
On February 19, 2023, ConnectWise published a security advisory for their ScreenConnect remote management tool. In the advisory, they describe two vulnerabilities, an authentication bypass with CVSS 10.0 and a path traversal with CVSS 8.4 (both currently without assigned CVE IDs). In this post we will dive into the technical details of the authentication bypass. You can view our POC here.
Update: On February 21, 2023, the authentication bypass vulnerability was assigned as CVE-2024-1709 and added to CISA’s Known Exploited Vulnerability (KEV) catalog.
Patch Diffing
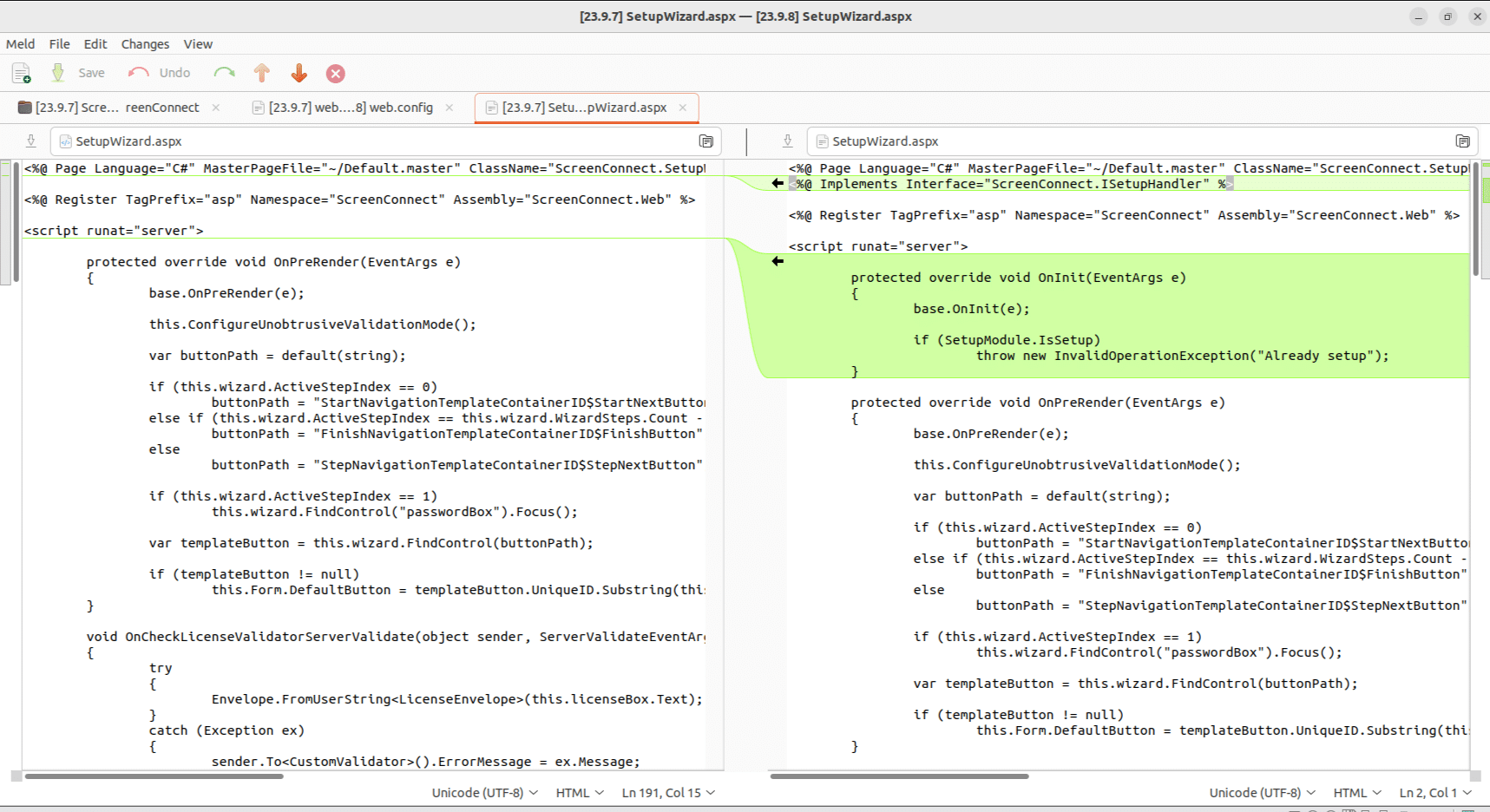
Comparing versions 23.9.7.8804 and 23.9.8.8811, we find a small update to SetupWizard.aspx. We see that a check was added to make sure that the initial application setup has not been completed if a user it trying to access the SetupWizard. The SetupWizard is responsible for creating an initial user and password, so it makes sense that this page should be locked down after an initial user has been created.
Figure 1. SetupWizard.aspx
The Vulnerability
There is a HTTP request filter in SetupModule.cs that has two responsibilities:
- If the application hasn’t been setup, redirect all requests to
SetupWizard.aspx - If the application has been setup, deny any requests to
SetupWizard.aspxor redirect toAdministration.aspx
Figure 2. SetupModule.cs OnBeginRequest
However, there is an issue with how this code checks if the request URL is SetupPage.aspx. The use of string.Equals checks for exact equality, so a URL like <app_url>/SetupWizard.aspx will match. However, there are other URLs that resolve to SetupWizard.aspx that don’t match. If we simply add a forward slash to the end of the URL (<app_url>/SetupWizard.aspx/) we get access to the setup wizard, even after the application is already setup.
Figure 3. SetupWizard.aspx
We can observe the differences in responses using Burp Suite. Notice the request path /SetupWizard.aspx responds with a 302, but the malicious path /SetupWizard.aspx/ responds with a 200.
Indicators of Compromise
The application’s Admin -> Audit page displays a list of recent login attempts along with the IP address. You can check this page for any unrecognized users or IP addresses.
As soon as we had sufficient information, we shared it with GreyNoise for which they developed a tag. Check out their tag here: https://viz.greynoise.io/tags/connectwise-screenconnect-auth-bypass-rce-attempt?days=1
Summary
This vulnerability allows an attacker to create their own administrative user on the ScreenConnect server, giving them full control over the server. This vulnerability follows a theme of other recent vulnerabilities that allow attackers to reinitialize applications or create initial users after setup. See our recent writeup for a CVE-2024-0204 as an example.
Unfortunately, this vulnerability has not yet been assigned a CVE. Users of ConnectWise ScreenConnect should patch immediately to prevent attackers from leveraging this vulnerability.
NodeZero
Horizon3.ai clients and free-trial users alike can run a NodeZero operation to determine the exposure and exploitability of this issue.
Sign up for a free trial and quickly verify you’re not exploitable.