VMware vRealize Log Insight VMSA-2023-0001 Technical Deep Dive
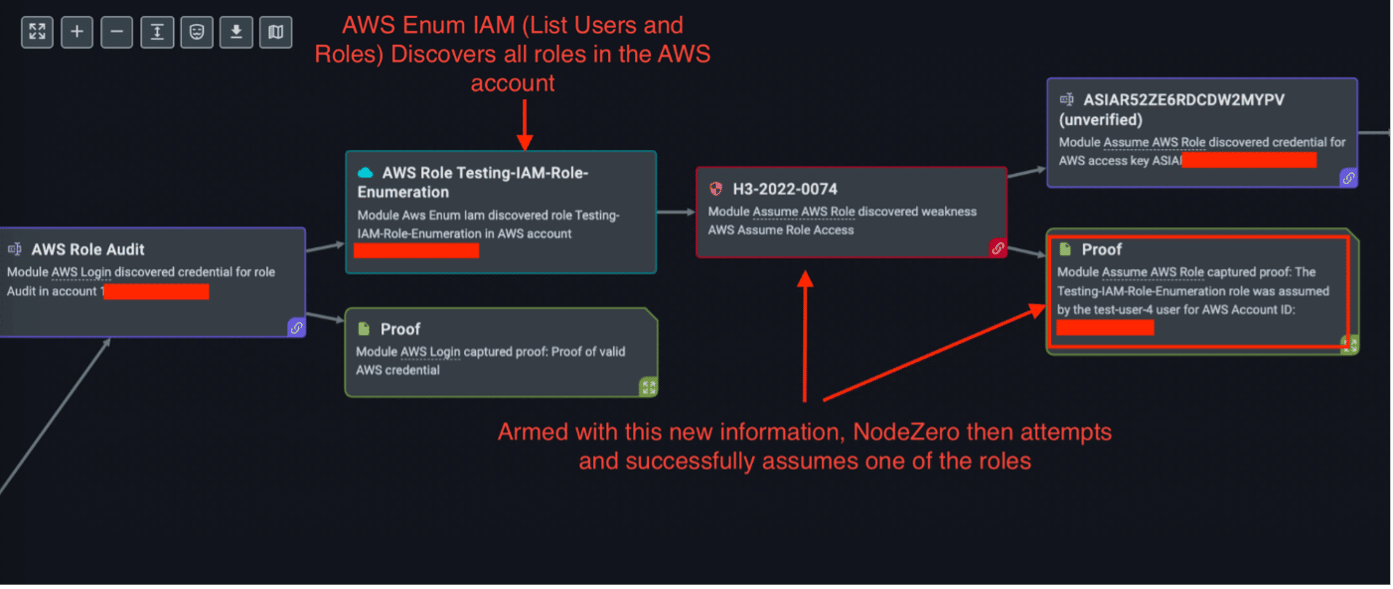
Introduction The recent VMware VMSA describes four new CVEs affecting VMware vRealize Log Insight, reported by ZDI. Three of these CVEs can be combined to give an attacker remote code execution as root. This vulnerability is exploitable in the default configuration for VMware vRealize Log Insight. We have successfully reproduced this exploit and would like to provide the technical details...
Read More