Which is more valuable to you; the ability to identify a problem, or the ability to solve the problem?
There is a plethora of vulnerability scanning tools that do a decent job identifying vulnerabilities. Unfortunately, those tools rarely discern the possible from the exploitable.

At Horizon3.ai our motto is “Trust but Verify” and this recent testimonial from one of our newest clients reinforces our edict.
As a leader in the healthcare industry, they understood the value of proactive defense in the cybersecurity domain and were already using a suite of well-known vulnerability scanning tools prior to partnering with Horizon3.ai.
If those products delivered on every promise, there should be no problem, right? Time and time again, NodeZero proves otherwise.
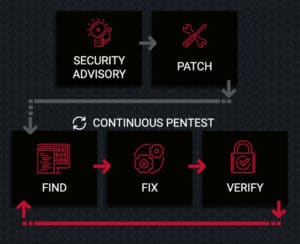
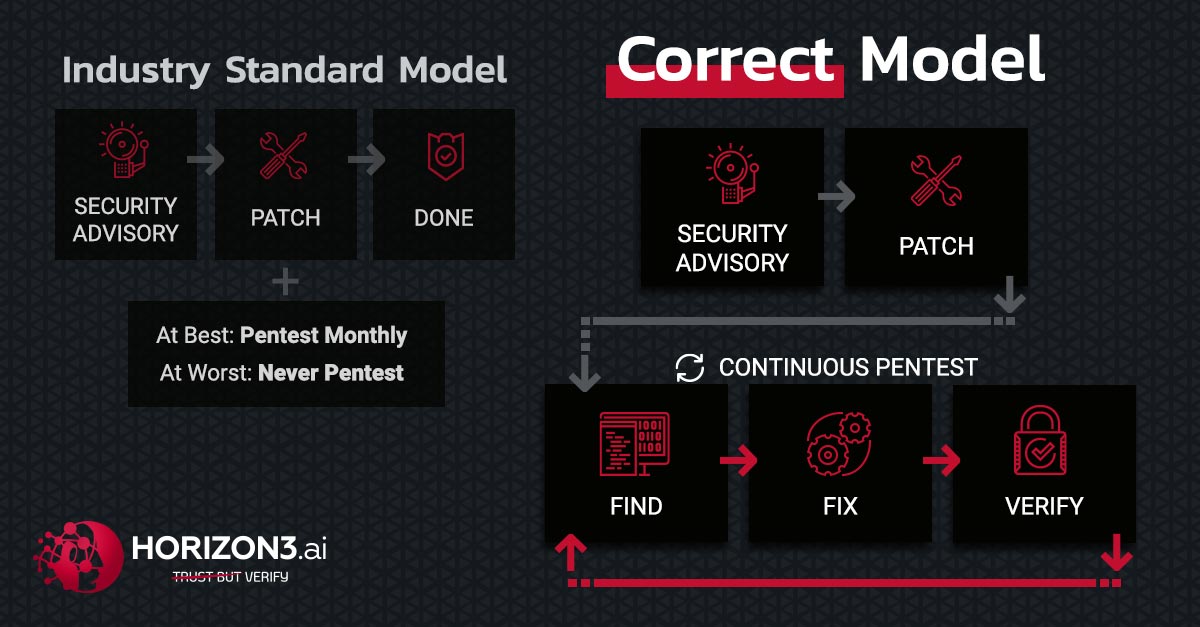
We believe the root of the problem is the current industry accepted model; patch often, pentest occasionally.
Patching a vulnerability is never enough, always verify your cybersecurity posture. Far too often, we hear our clients say, “There’s no way, we just patched that!” This is exactly why patching is not enough and the basis for our proposed model.
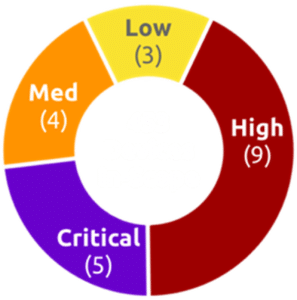
Despite our client’s previous cybersecurity efforts, on NodeZero’s first autonomous pentest, several vulnerabilities were identified including 5 deemed Critical, affecting nearly 40 hosts.
Among those was a vulnerability in the Smart Install feature of Cisco IOS Software which allows unauthenticated access which left the door open for NodeZero to gain remote code execution (RCE) fully autonomously. This critical vulnerability affected six of their Cisco devices.
After the client’s initial shock wore off, they went to work patching this vulnerability as well as the others NodeZero identified and exploited.
End of story, right? This is where the story begins! After patching what NodeZero proved exploitable, they ran a follow-on pentest. What they learned was patching actually failed for one of the Cisco devices. As far as they could tell all devices were successfully patched, that is until NodeZero exploited the same device again.
Patch Validation = Pentest
Just as we suggested, patching cannot be the end of the cybersecurity model. Another pentest MUST follow patching. For most, conducting a second pentest within months of the previous iteration is unimaginable, let alone days or hours apart. Traditional pentests are expensive, time consuming, unreliable, inconsistent, and too often concluded at the first point of critical compromise.
After you run a patch, is there any way to know for sure the vulnerability has been eliminated? Multiple times we have encountered this scenario; the patch failed, and the cybersecurity team was unaware. This is just one reason pentests should be conducted far more often than the industry standard currently demands. The best way to know if a vulnerability was successfully patched is to re-attempt the exploit after patching.
Since partnering with Horizon3.ai, this client has conducted over 40 unique penetration tests, with scopes ranging from just a couple hosts to several thousand. This cycle of Find, Fix, and Verify is exactly the cycle which leads to a reduced time of risk exposure and the greatest Return on Investment (ROI).
NodeZero in Action
The vulnerability detected, and re-detected, on the Cisco devices was CVE-2018-0171, a nasty vulnerability associated with the Smart Install plug-and-play configuration and image-management feature installed on many Cisco devices. The vulnerability is classified as improper validation of packet data, where an attacker could send a crafted Smart Install message via port 4786. The adverse results of an exploitation could include: a triggered reload of the device, executing arbitrary code on the device, setting the device in an indefinite loop and triggering a crash. Below is a NodeZero screenshot of the initial pentest showing the vulnerable Cisco devices:
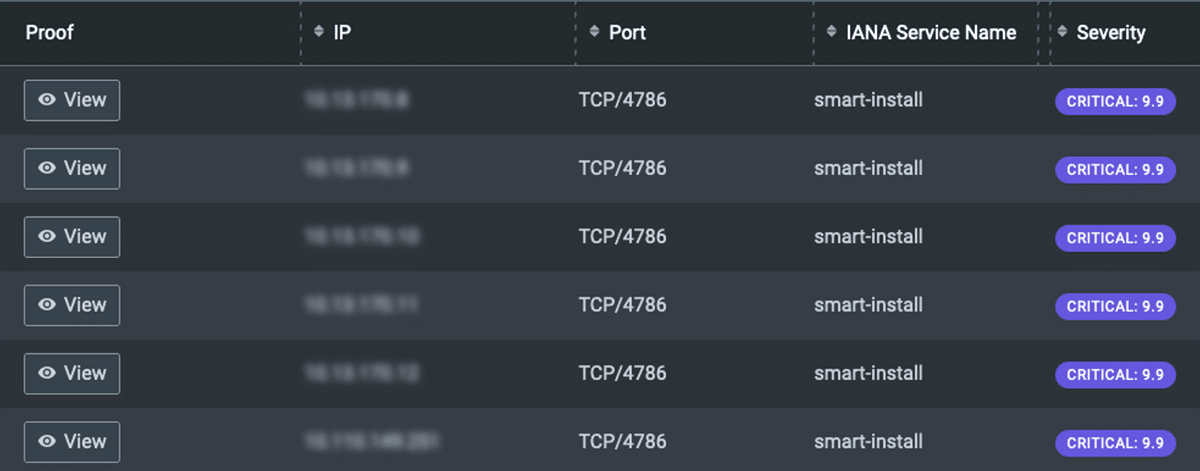
The client is always presented the attack path and proof of exploit for each device and exploited vulnerability. This particular example illustrates how NodeZero found the Smart Install Service running on Cisco devices which led to the exploit of CVE-2018-0171 for all six Cisco devices. NodeZero shows its work on every pentest:
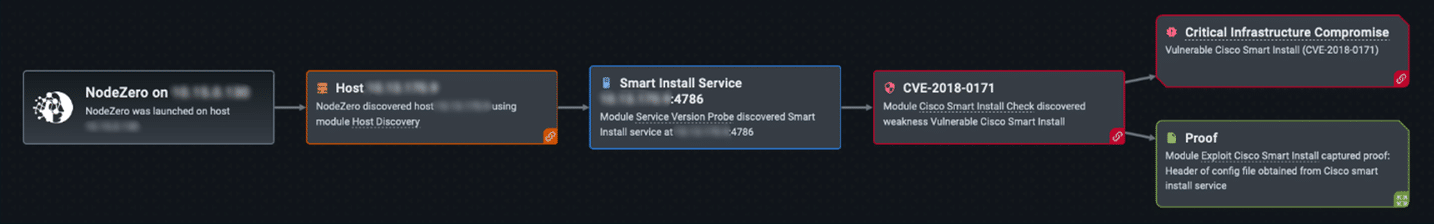
When you click “Proof” you will see the evidence of exploit, in this case NodeZero gained root-level access to the vulnerable devices and captured the header information directly from the configuration file.
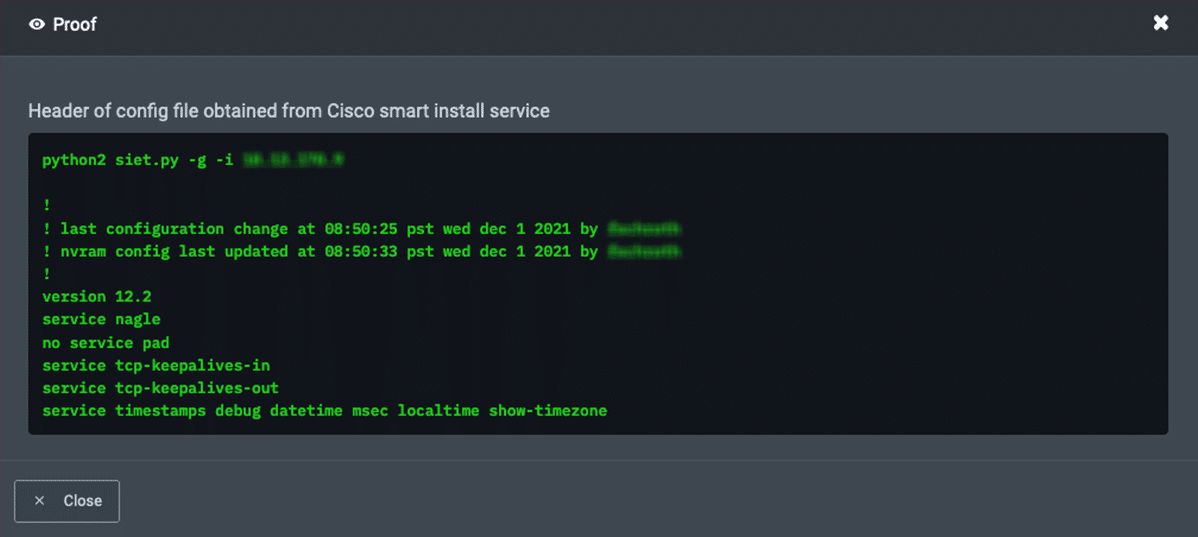
NodeZero had the access hackers dream about, but NodeZero plays nice!
Fix
Following the initial pentest, NodeZero provided fix-action reports which detail recommended remediations.
In this case, the client was presented the mitigating options; upgrade the IOS to a secure version, or disable the Smart Install Service, or apply firewall whitelist rules.
After working with Horizon3.ai team, the client decided their best approach was to upgrade Cisco IOS to 12.2(55)SE12 on all devices.
Verify
Verification is important for two reasons:
- Did your fixes actually take?
- In patching, did you create a new vulnerability/open a new attack path?
After running the updates, our client ran a limited-scope verification pentest and to their surprise, one device was still exploitable while the others were not. The screenshot below from the NodeZero portal shows the critical vulnerability remained in one Cisco device:
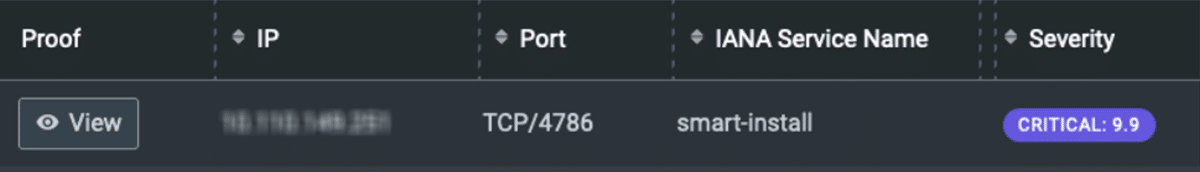
As each customer has a direct line to the Horizon3.ai dedicated Customer Success team, the network engineer reached out to ask that we investigate the “false positive” reported on the Cisco device.
The other devices had the same vulnerability, and the same fix action was already performed. They were sure NodeZero was triggering a false-positive… the “f word” we hate most at Horizon3.ai. Horizon3.ai Customer Success team immediately went to work with our customer.
With a quick investigation, we learned the IOS upgrade actually failed for that one device which NodeZero reported vulnerable. Not a false-positive!
False-Positive Fatigue
We understand the urge to call a “false-positive” after running hundreds of common vuln scans… you get used to it.
NodeZero is not reporting a potentially vulnerable device, NodeZero is literally running an exploit, capturing evidence, and then backing out gracefully to ensure no harm to your system. There are no false positives, this is one reason NodeZero stands apart from the standard common vulnerability scanner.
After the successful IOS install, the customer immediately ran another quick pentest of the single affected host, where NodeZero was able to verify the upgrade took and the vulnerability was indeed eliminated from their network!
NodeZero is the product. Horizon3.ai is your partner.
Horizon3.ai Customer Success Team and our newest client worked together securing their network. Here is the breakdown of events:
- Client ran an initial NodeZero pentest.
- NodeZero discovered 21 weaknesses affecting 40 hosts.
- Client deployed patch management and ran a follow-on NodeZero pentest.
- Customer Success Team and our client discovered a patch failed for a critical vulnerability.
- Client deployed patch management again where required.
- NodeZero verified successful remediation through another pentest.
If you run a patch, pentest. If you run an update, pentest. If you install new equipment, pentest. If you forgot the last time a pentest was ran, pentest. If your smart-toaster burned your English muffin, pentest!