Unveiling Strategic Defense for Your Supply Chain: Learn about emerging supply chain threats, innovative solutions in supplier security, and how NodeZero™ can transform your approach to cybersecurity.

Continuously Find, Fix, and Verify Your Exploitable Attack Surface
The NodeZeroTM autonomous penetration testing platform empowers you to reduce your security risk and continuously improve your security postures.
Trusted By
Continuous Penetration Testing, At Any Scale
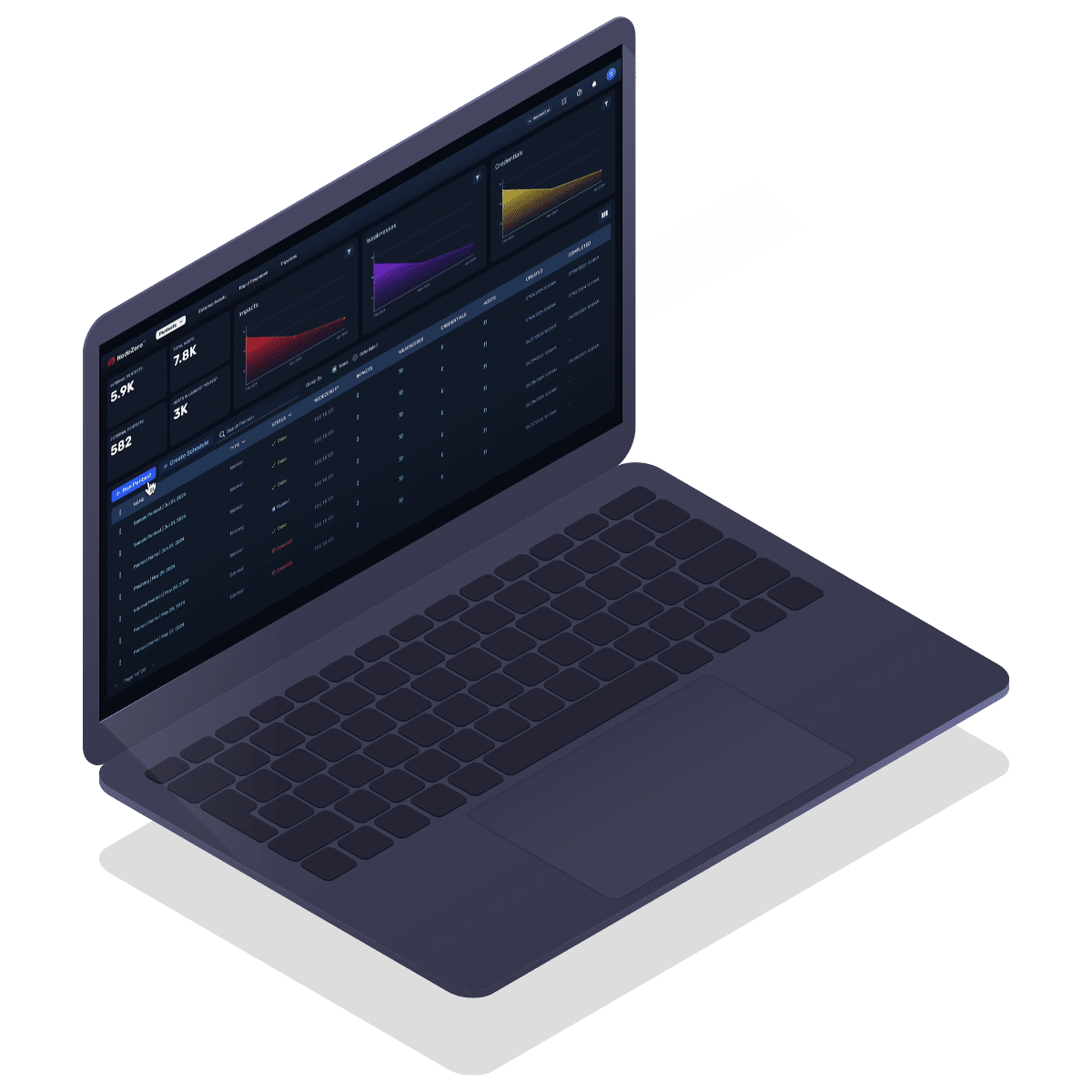
The NodeZero Platform
NodeZero is easy-to-use, safe for production, and scales to support your largest networks. You are empowered to test a very broad scope in a single test, orchestrate tests concurrently, and simultaneously test your enterprise from different attacker perspectives.

Exploitable CVEs

Tool Validation

Compromised Credentials

Asset Discovery

Misconfigurations and Dangerous Defaults

Ineffective Policies
Don’t just take our word for it
We are rated 4.7 ★ on

Play offense. Inform defense.
How does NodeZero Do it?





In an internal pentest, the NodeZero platform takes the perspective of an attacker or malicious insider who has already gained access to your internal network.
In an external pentest, the NodeZero platform takes the perspective of an attacker to assess your assets and digital risk at the perimeter. Don’t miss a single blind spot.

NodeZero's AD Password Audit quickly identifies risky passwords in your Active Directory environment, providing prioritized guidance for mitigation, including proof of cracked passwords and blast radius impact analysis.
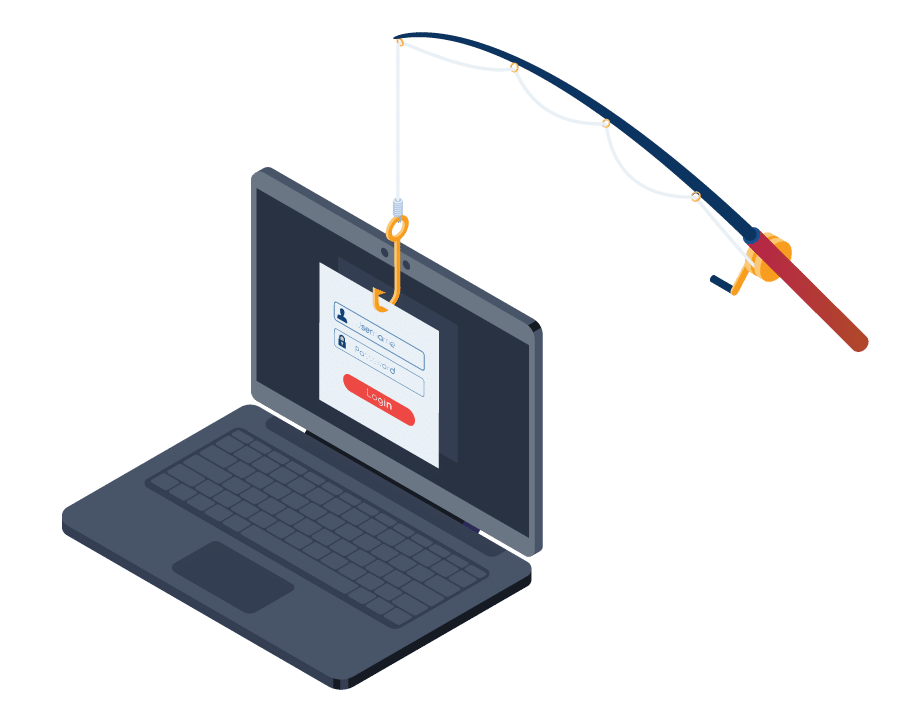
NodeZero's Phishing Impact Testing feature provides comprehensive insights into the true impact of phishing attacks on an organization.

NodeZero's Rapid Response service offers users early intelligence on emerging cyber threats, enabling swift identification, verification, and mitigation of N-day and zero-day vulnerabilities before they become widely exploited.
Recognized By
Rising Cyber Award 2024
Rising Cyber Award 2024
VSA Top Innovation Award 2024
VSA Top Innovation Award 2024
VSA Cybersecurity Award 2024
VSA Cybersecurity Award 2024
2024 Cybersecurity Excellence Awards
2024 Cybersecurity Excellence Awards
Security Today Govies Award
Winner, Security Today Govies for Autonomous Penetration Testing
















