Background
In a traditional brute force attack, an attacker targets a single account and tries to repeatedly guess the password for the account until he/she succeeds, or gives up. This type of attack rarely works unless the account happens to have a really weak password.
In a password spray attack, an attacker starts with a list of users and a shortlist of probable weak passwords. The attacker tries (i.e. “sprays”) each password, one at a time, against all all users in an attempt to compromise at least one account. Attackers usually limit the rate of their attempts to avoid causing account lockouts. Attackers know that, once they’ve compromised at least one account, they can abuse that account’s access to enumerate deeper and potentially compromise more accounts, assets, and data.
A password spray attack has a much higher chance of success than a traditional brute force attack because it only requires compromising one account out of many possible accounts. In large organizations especially, the odds are high that there are going to be some users with weak passwords who would be susceptible to password spray.
Password spray is tracked as MITRE ATT&CK technique T1110.003. APT-28 (Fancy Bear), APT-29 (Nobelium), and APT-33 (Elfin) are examples of well-known threat actors who have used this technique. But this is not a technique just reserved for nation-state threat actors. Microsoft has estimated in the past that password spray attacks account for nearly one third of account compromises. Many spraying toolkits, such as crackmapexec, are readily available, making password spray a point-and-click operation for any level of attacker.
How NodeZero Weaponizes Password Spray
Username Enumeration
The first step for an attacker executing a password spray attack is compiling a large list of users. The larger the list, the more likely the attack will succeed.
NodeZero uses about a dozen different methods to gather usernames, both internally and externally. These methods include scraping user information from social media and exploiting misconfigurations in commonly used applications such as Jira, Jenkins, ManageEngine ADManager Plus, and WordPress. In internal pentests with older domain controllers, anonymous access over SMB is an especially powerful misconfiguration for attackers because it can lead to directly enumerating all domain users. If NodeZero already has a regular domain user credential in hand, it uses that credential to enumerate other domain users.
These username enumeration misconfigurations are often thought to be medium or low severity issues to fix, but they can be really valuable for attackers when used in conjunction with password spray.
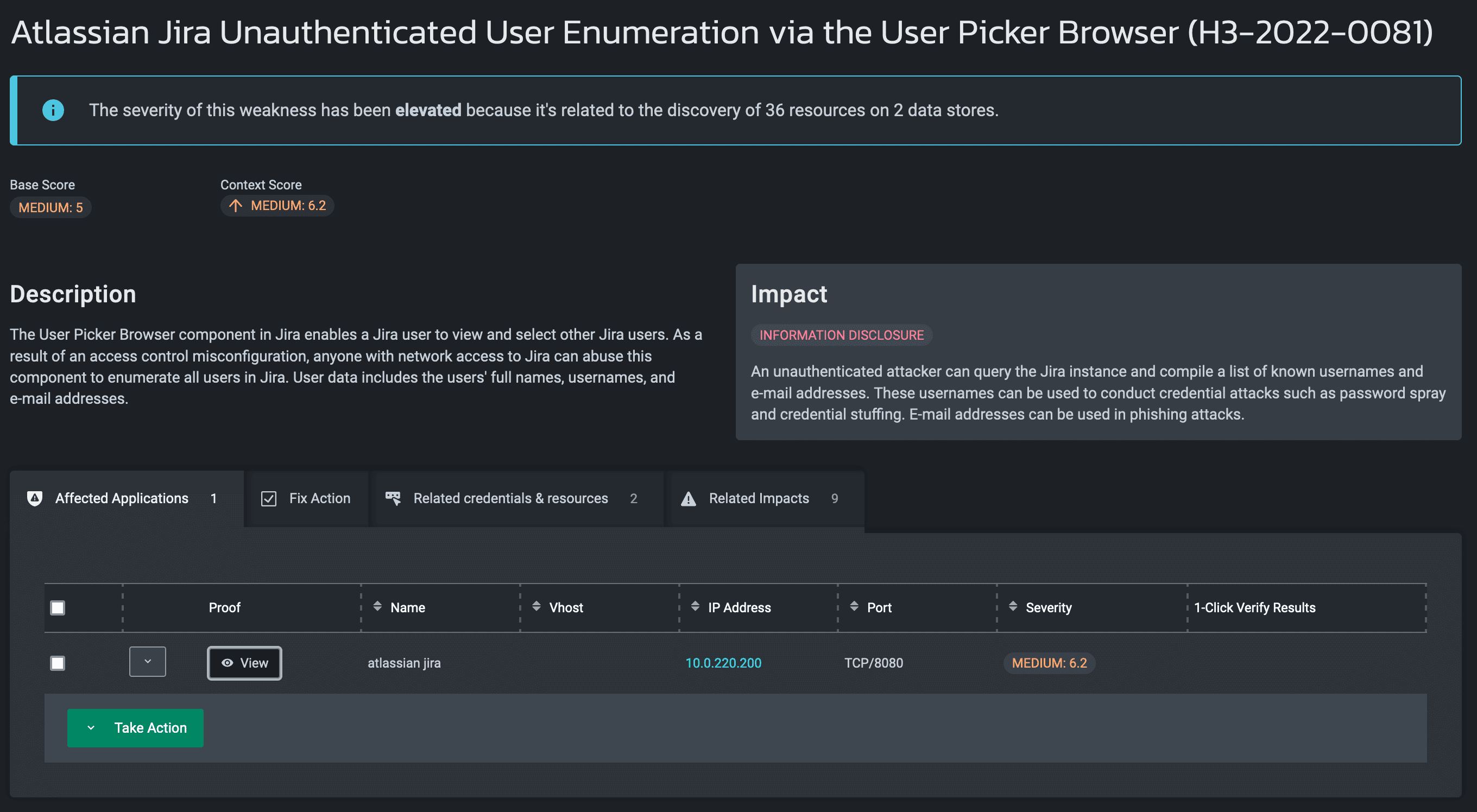
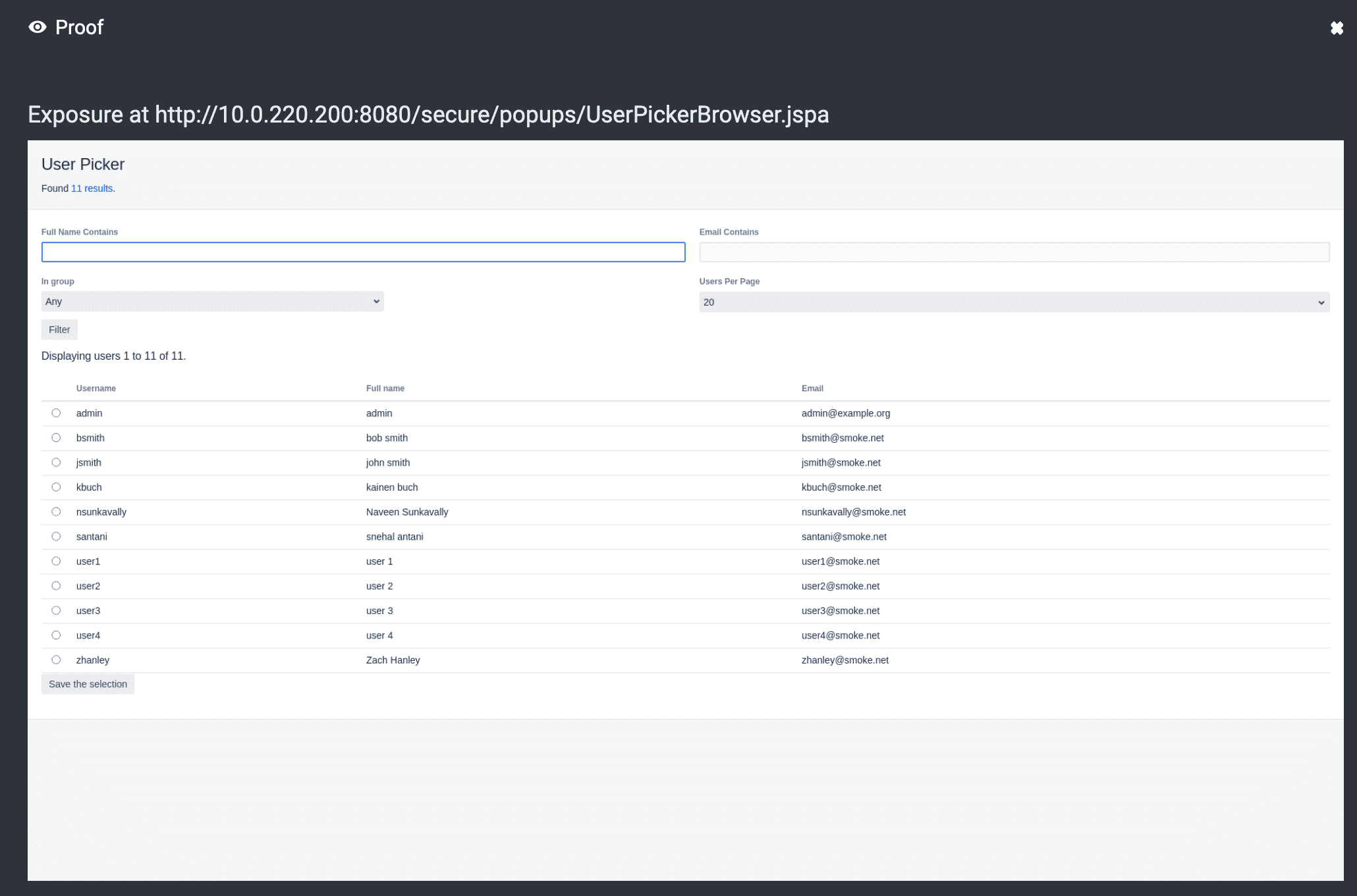
Here’s an example of a weakness raised by NodeZero after exploiting a Jira misconfiguration to enumerate all users:
Password List Generation
With a list of usernames in hand, the next step for an attacker is to come up with passwords to spray. NodeZero generates probable passwords to spray based on commonly known breached passwords, context-specific terms such as the company name or domain name, or a custom dictionary supplied by the user.
Attackers know that most companies have set up a password policy to enforce a minimum password length of 8 characters, password complexity rules (including lowercase, uppercase, digits, and special characters), and periodic rotation of passwords. Password complexity and rotation policies have ironically led users to creating more predictable passwords such as passwords starting with an uppercase letter, ending in 1!,, or containing seasons and years. NodeZero optimizes for these cases to maximize the likelihood of success.
In addition to spraying probable weak passwords, NodeZero also attempts to spray any passwords it finds organically during the course of a pentest, just like a real-world attacker would do. These are passwords that may be found through unintended data exposure or exploitation, and they may not necessarily be weak. This form of password spray is used to exploit password reuse across multiple accounts.
Password Spray Execution
In internal pentests, NodeZero conducts password spray against domain controllers in the hope of landing a domain user for initial access. If it already has a domain user in hand, NodeZero will further conduct targeted password spray against privileged domain users in an attempt to compromise the entire domain. In real-world pentests, NodeZero has fully compromised organizations through password spray alone.
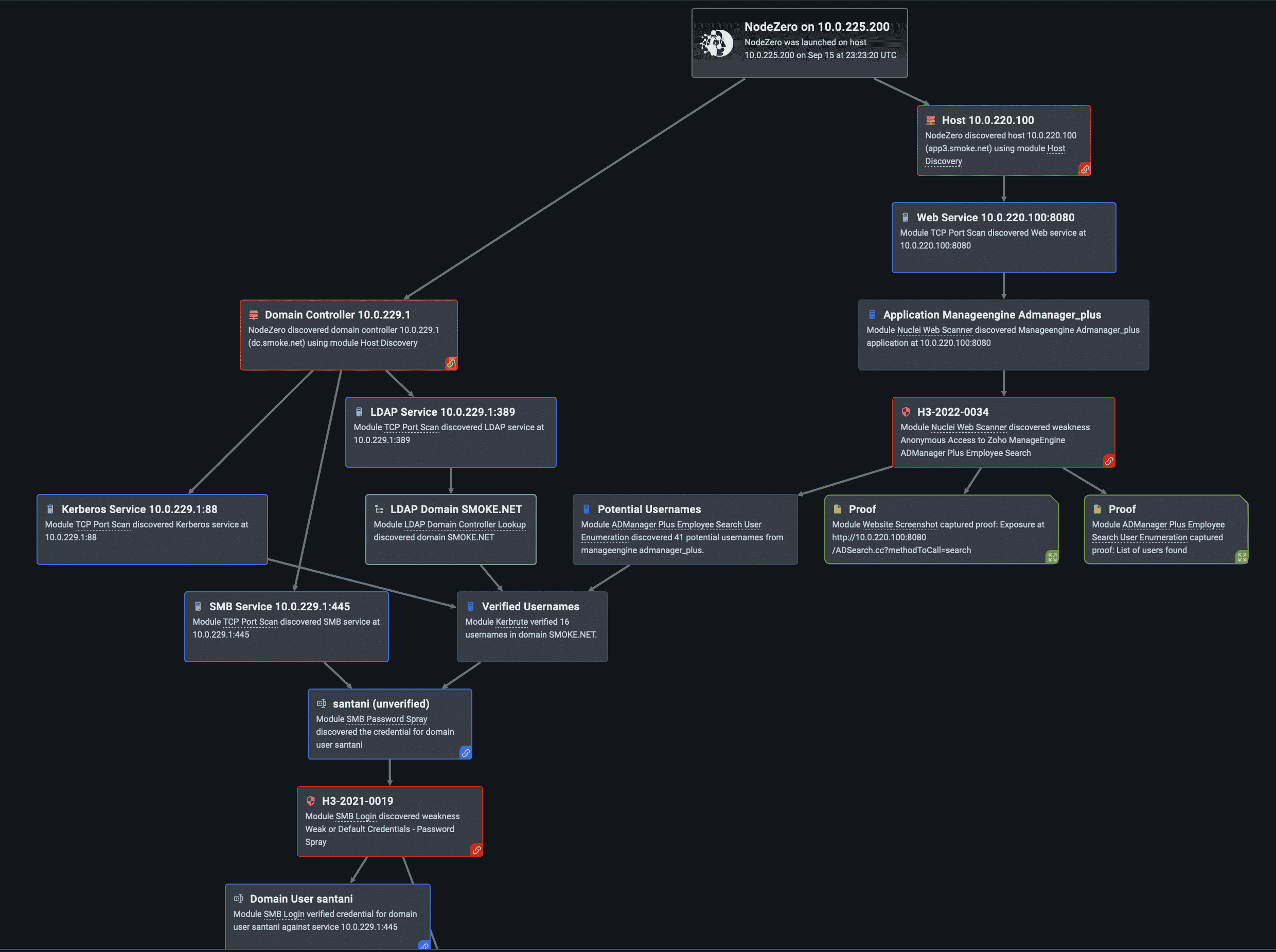
Here’s an example of the attack graph generated from a successful password spray of a domain user in an internal pentest. In this case NodeZero scraped users off an ManageEngine ADManager Plus instance and guessed the password for the “santani” user using a password derived from a company name.
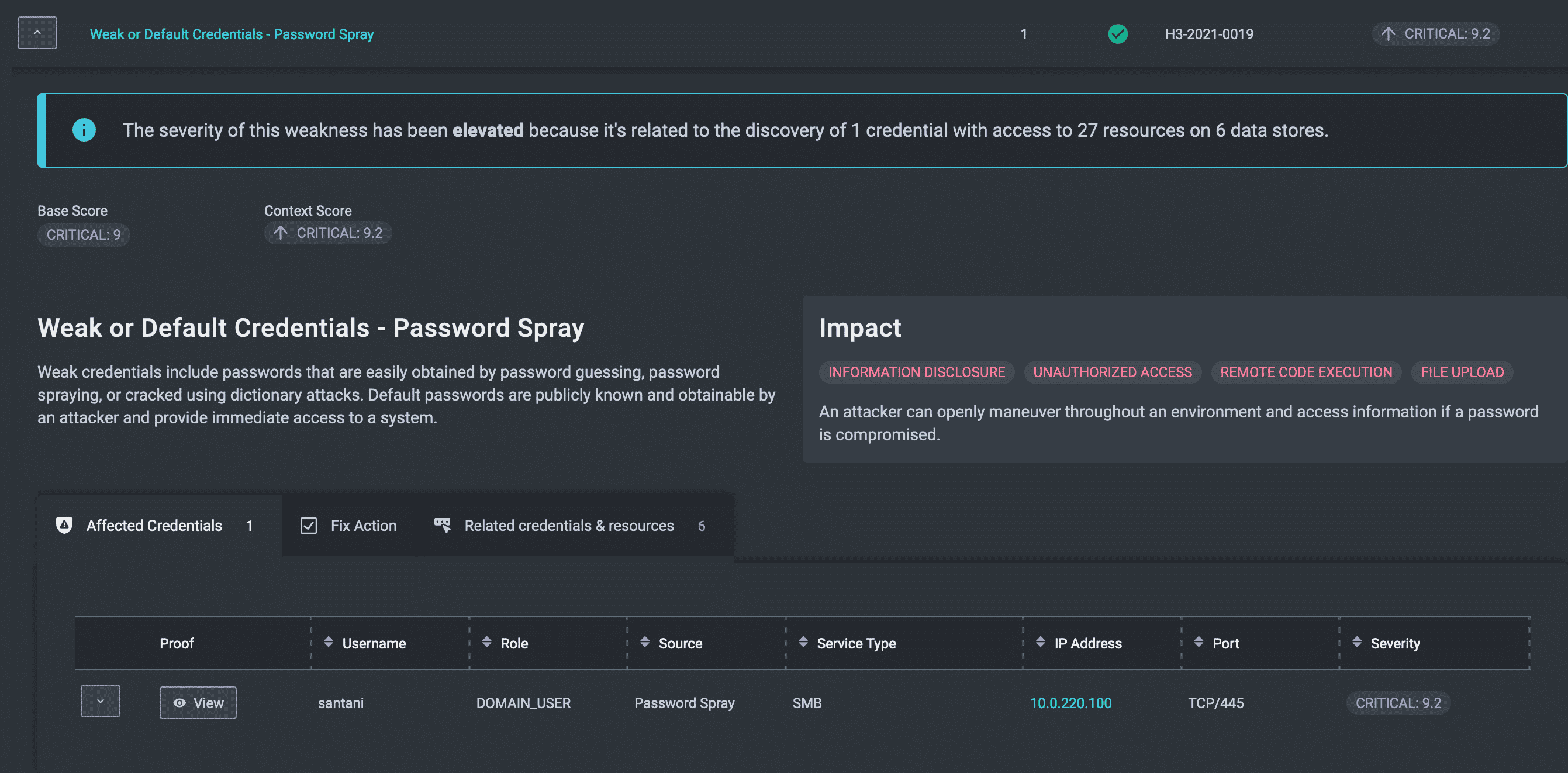
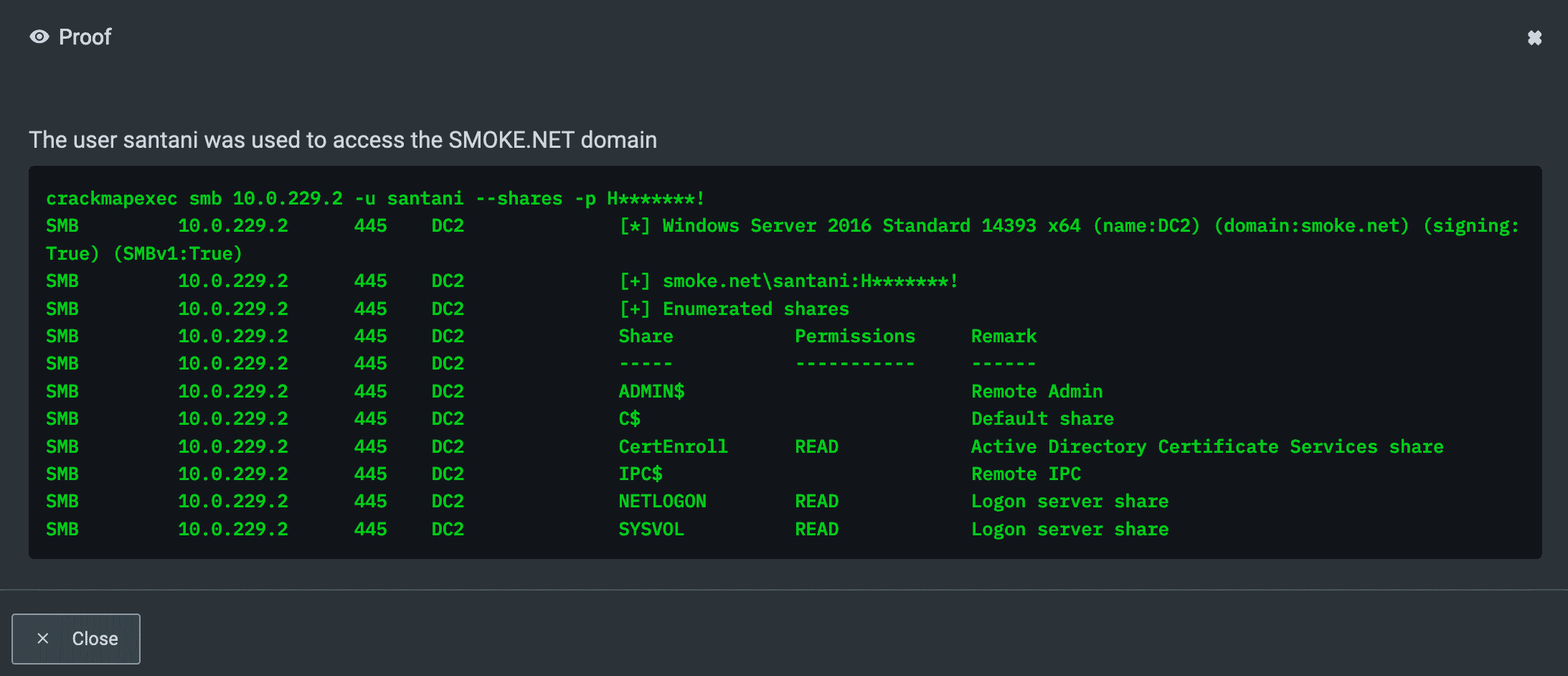
In external pentests, NodeZero conducts password spray against Azure AD in the hope of landing an Azure AD user to access Microsoft365 services or backend Azure services such as the Azure Graph API. NodeZero uses a new public IP address each time it sprays in an effort to evade detection.
Here’s an example of an attack graph NodeZero generates from a successful password spray of an Azure AD user in an external pentest. In this case NodeZero scraped users off an externally accessible Jenkins instance and guessed the password for the “santani” user. NodeZero went on to access the user’s Microsoft365 Outlook mailbox.
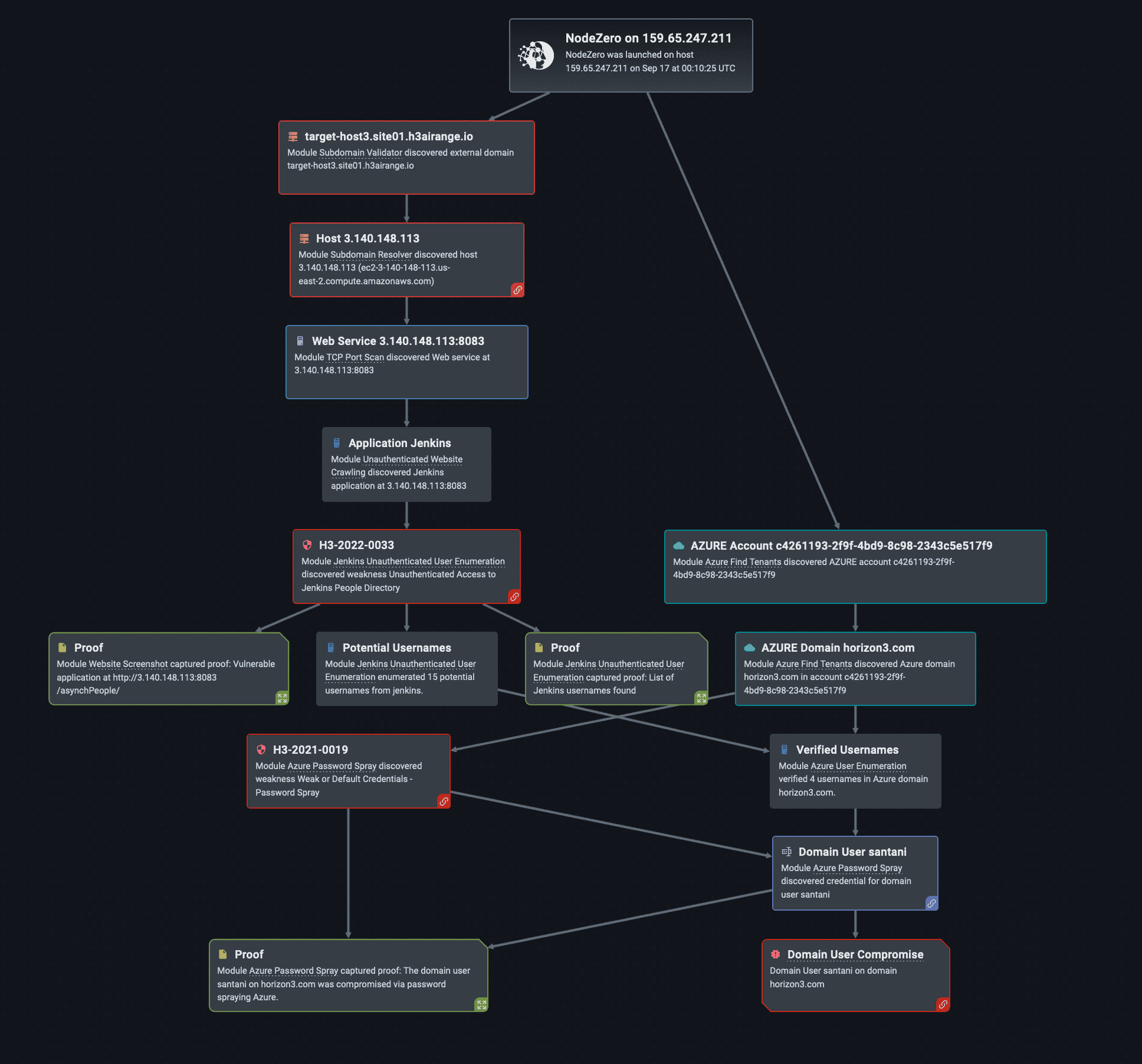
Tips for Defenders
Increasing Attacker Difficulty
- Ban certain terms and their variants from appearing in passwords. These terms include dictionary words, known breached passwords and company-specific terms such as the company name. This is important because it makes attackers have to think outside the box to come up with passwords to spray. Consider using Azure AD Password Protection.
- Do away with password complexity and password rotation policies. For a long time people who were advised that password complexity is important and passwords need to be rotated, but this advice has only led to people creating more predictable, easier-to-guess passwords. Our guidance on this is in line with the latest guidance from NIST Special Publication 800-63B.
- Enforce a minimum password length – we recommend at least 12 characters. This is higher than the NIST-recommended minimum of 8 characters.
- Set a relatively low account lockout threshold, but not too low. A lower account lockout threshold makes it so attackers have to spend more time conducting the spray. At the same time, if it’s too low, regular users may end up calling the IT helpdesk often after mistyping their passwords, and it’ll also enable attackers to easily perform a denial of service (DoS) attack against the organization. We recommend a threshold between 5 and 10 attempts before lockout.
- Monitor application and domain controller logs, and setup alerts for login failure events happening across many users within a short window of time.
- Fix any misconfigurations related to username enumeration, especially ones that yield a full snapshot of all users in the domain. Note that motivated attackers will still be able to compile a list of users, but it’s better to make it harder.
Other Controls
Multi-factor authentication (MFA) is a must-have for any external exposed endpoints. And if there’s an endpoint that doesn’t support MFA, it should not be exposed externally under any circumstances. The advantage of MFA is that, even if an attacker succeeds at password spray, he/she will have another hurdle to get through before fully compromising an account.
For internal networks, MFA won’t help much because there are many lower level endpoints using non-MFA protocols such as SMB, RPC, LDAP, and Kerberos that an attacker can spray against.
We also strongly recommend adhering to the standard principle of least privilege, ensuring all users are provisioned with only the access they need. Security is about defense in depth, and it’s important to minimize the blast radius – a single user being compromised should not instantly cascade into the rest of the organization also being compromised.