If there’s one thing we love seeing, it’s people using NodeZero to assess their hybrid cloud at scale, especially when verifying a fix.
While unannounced zero-day vulnerabilities garner a fair bit of fear and attention, one of the greatest risks introduced to business operations are newly announced vulnerabilities, or N-days. When an easily exploitable vulnerability surfaces for a ubiquitous product, we’re all in a race condition to:
- Find any assets (especially public-facing) that are vulnerable
- Fix (remediate or mitigate) as quickly and safely as possible
- Verify the implemented fix action is actually working when attacked
For example, over the last week cybersecurity practitioners have been scrambling to remediate their Fortinet appliances to the latest CVE-2022-40684. In case you missed it, here’s a rundown to catch you up:
- N-day: a user tweets regarding an advance notification email from Fortinet on a new vulnerability with patch instructions; to date, no information has been posted to the National Vulnerability Database or MITRE CVE sites; both have “reserved” space for CVE-2022-40684.
- N+2: H3 Attack Team announces positive exploitation; H3 recommends patching now: (https://twitter.com/Horizon3Attack/status/1579285863108087810)
- N+4: H3 releases Indicators of Compromise (IOCs) (https://www.horizon3.ai/fortinet-iocs-cve-2022-40684/) following reports of the CVE being actively exploited in the wild (@GreyNoise https://twitter.com/GreyNoiseIO/status/1580557335231365123).
- N+5: H3 releases a safe and reliable exploit to NodeZero and notifies customers with vulnerable instances to find, fix, and verify their Fortinet appliances immediately. H3 publishes a Technical Deep Dive into the discovery and weaponization of the Fortinet Vulnerability (https://www.horizon3.ai/fortios-fortiproxy-and-fortiswitchmanager-authentication-bypass-technical-deep-dive-cve-2022-40684/).
- N+6: H3 publishes a short video explaining the Fortinet vulnerability and exploit (https://www.youtube.com/watch?v=yJovc9sNrX4).
A quick online search reveals several articles outlining the vulnerability and its ongoing mass exploitation. When an easily exploitable vulnerability surfaces for such a ubiquitous product, we’re all in a race condition to fix while attackers are trying to exploit.
In the image below, you will see part of an administrator’s NodeZero operations summary screen, where several of our customers and new free-trial users are quickly verifying their security posture.
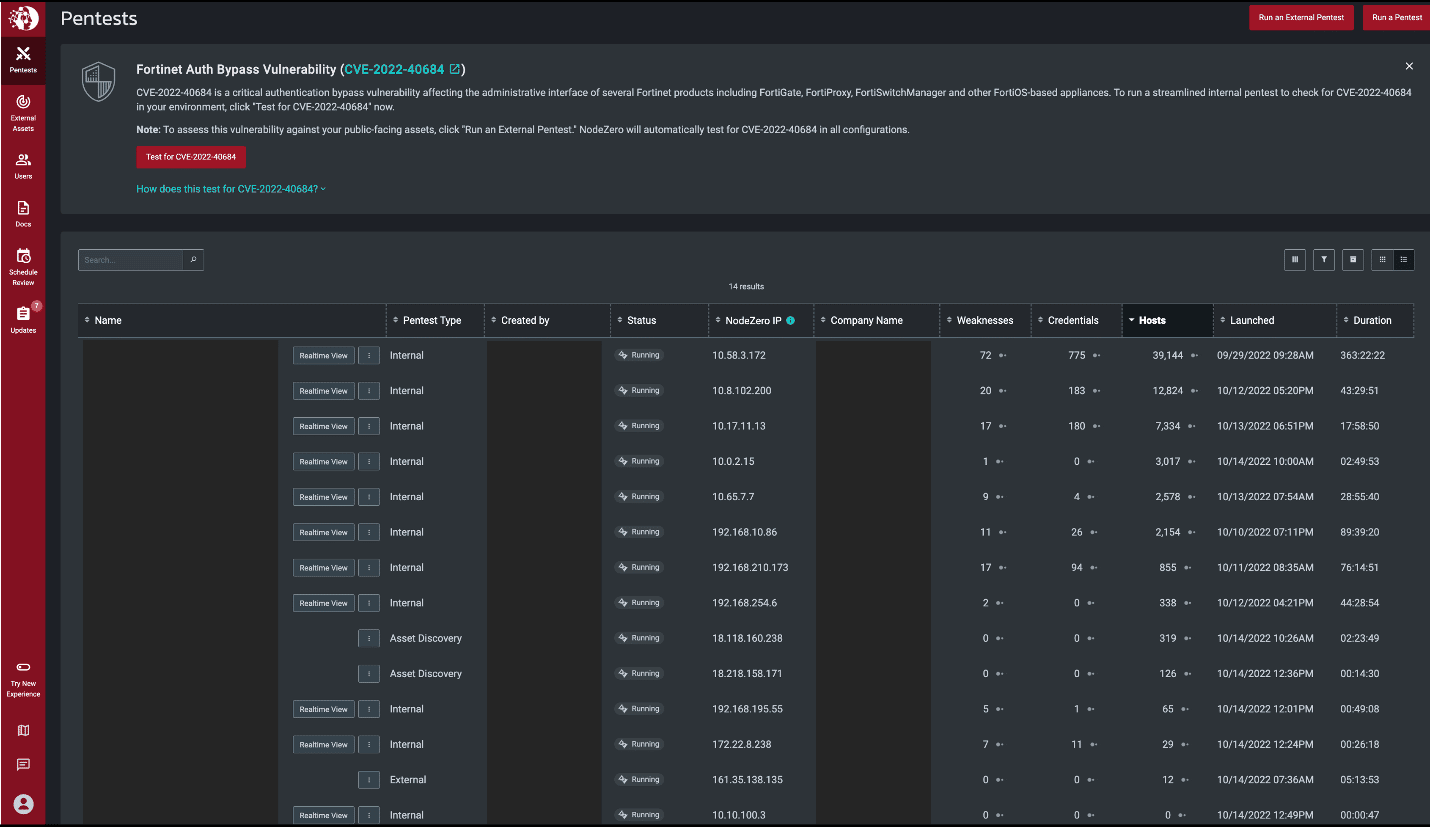
Some wanted to focus on specific known hosts running the vulnerable OS, while others wanted to find, fix, and verify “at-scale” across their entire enterprise product network. This is how our users find that appliance that wasn’t supposed to be public-facing anymore, where that host set up by marketing that was supposed to have been decommissioned years ago, or where those third-party authentications your developers utilized while your product was in stage didn’t promote to prod. This is how we all verify that our weekend fix-actions are effective.
For instance, here’s how one client used NodeZero:
They used NodeZero to find and verify their Fortinet appliance was vulnerable, reachable, and exploitable from their chosen perspective, or launch point. They didn’t need to install an agent, create a script, and load a credential. They just used our simple Course of Action card, specified a scope, and launched a pentest.
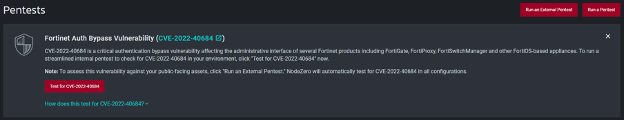
Their first test came back confirming their appliance was exploitable.
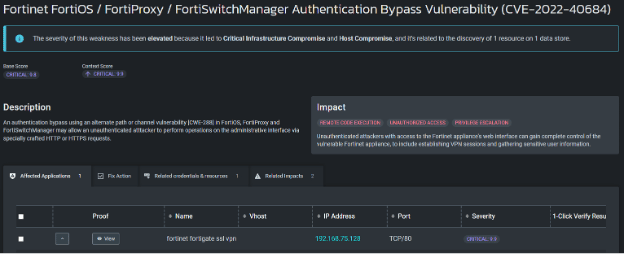
This is the attack path NodeZero took enroute to compromising this host and critical infrastructure.
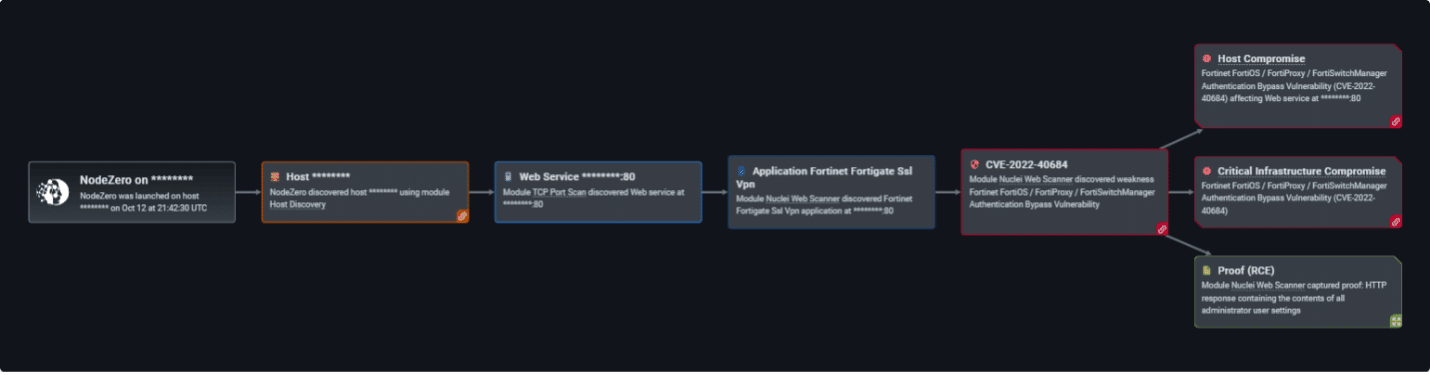
You can see NodeZero autonomously discovered the host, checked that the web service on Port 80 was up and running, found that the Fortigate SSL VPN application was running, then ran our exploit, taking advantage of the appliance OS browser header and looking for a specific server IP address as authoritative, told it to reach out to our interact server, and once compromising the host NodeZero provides proof by showing the contents of the administrator user settings.
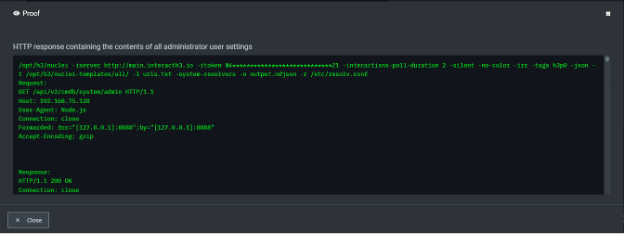
Now that they know it’s exploitable, what did they do? 17 minutes later they ran a second attack just to verify it really was. After confirming, the next pentest we see is the following morning:
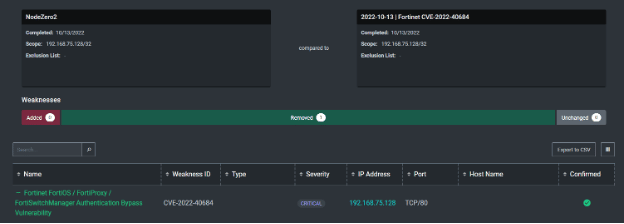
And now you can see the comparison, where the hosts are still reachable but no longer vulnerable nor exploitable.
This is how we win.
Bottom Line: we’re simplifying the ability for anyone to verify if their appliances are reachable, vulnerable, and exploitable. Can your other tools do that at speed and scale?
This article was authored by Monti Knode, Director of Customer and Partner Success at Horizon3.ai.



