NodeZero is a generational leap beyond a traditional pentest – organizations often see that for themselves from the moment they give our autonomous pentesting platform a shot. NodeZero surfaces risks and weaknesses that would never have come up during a general vulnerability scan as it chains together attack tactics and techniques to illuminate your most critical impacts an attacker could generate.
Take for example a recent NodeZero operation run by an organization in the wholesale distribution sector. What at first appeared to be minor “password issues” led to a high-risk attack path enabling NodeZero to access the domain admin accounts, and even break into the organization’s Azure cloud environment.
From here, NodeZero could pivot and impact day-to-day operations, such as compromising their business email, but more to follow on that below.
To start, NodeZero performed a host discovery and found weaknesses through the LLMNR (Link-Local Multicast Name Resolution) protocol, poisoning a host and capturing an unverified credential. (LLMNR is a service used by Windows to resolve hostnames to IP addresses when a DNS request fails in a network.)
The first thing NodeZero did at that point was to try to crack the hash, which it did in under five minutes.
NodeZero obfuscates usernames and passwords prior to destroying those records after every pentest, in order to verify that NodeZero was successfully able to obtain them. In this case, “when we see a capital P at the beginning and an exclamation point at the end, that doesn’t bode well,” says Monti Knode, Director of Customer Success with Horizon3.ai. This usually, as you likely already know, means it’s a default or extremely common password.
Making matters worse, this was a privileged account.
Now that NodeZero had the name and password, it attempted to log in to the domain – and in this case, it was able to do so as a Domain Administrator immediately leading to a domain compromise on this domain controller with full read/write access permissions.
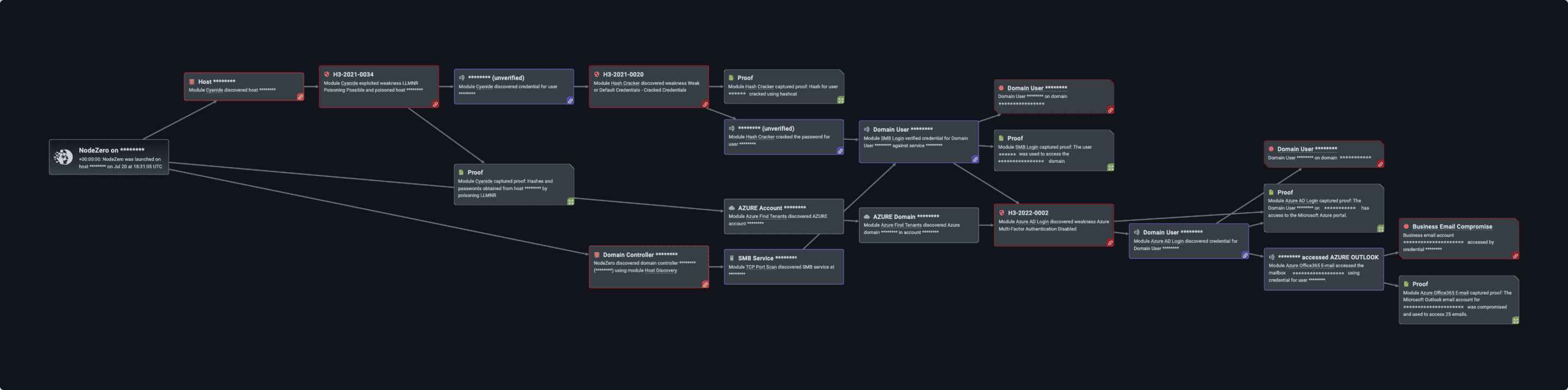
An attack graph demonstrating how NodeZero obtained access to the customer’s Azure Cloud.
Domain compromise not once but twice
A business email compromise enabled NodeZero to take a regular user’s credentials – found while trying to log into the domain – and leverage that to find other credentials. It then could find a domain user, impersonate them, and gain additional control over a second domain admin.
With this second credential, NodeZero elevated a regular user with no rights to domain admin by taking advantage of the noPAC vulnerability. A little background: In mid-December 2021, noPac, a public exploit that combined two Microsoft Active Directory design flaws, was released; it allowed escalation of privileges of a regular domain user to domain admin, which then enabled malicious actors to launch multiple attacks, including domain takeovers or ransomware attacks.
“That’s why this vulnerability is at the top of the weakness list,” says Knode. “If we were to recommend one thing to fix in this case, it would be that noPac vulnerability.”
NodeZero offers a Fix Action linking to the knowledge base information needed so the organization could move on a fix action to get those domain controllers patched and protected.
NodeZero offers context for the vulnerability, related credentials and impacts, and the knowledge needed to fix and maintain so the organization has the education and tools to keep it updated in the future.
The impact component is vitally important, as by offering context scoring, the customer can see why a weakness that leads to critical impacts in a network gets prioritized to the top of the list of recommended fixes.
The customer can even rerun a “1-click Verify” pentest on just those hosts where there is a known weakness. “Something like this should be a fairly easy one to do, and we highly recommend it – follow our Fix Actions for those noPac vulnerabilities, select the 1-click Verify option to follow up, and then rerun this more surgical operation as soon as you get the chance,” says Knode.
Business email compromise
NodeZero was also able to execute a business email compromise chaining an attack from the previously successful LLMNR poisoning technique. In this case, NodeZero found that this user was a tenant on the company’s Azure account and from the domain user, was able to pivot for further access. Multi-factor authentication (MFA) was not activated, so NodeZero was able to gain access into their Azure cloud environment and then get into Outlook.
With this valid domain account, NodeZero accessed 25 business emails, and as proof, NodeZero showed the customer the subject lines of the emails it was able to access.
“NodeZero took advantage of the Active Directory login because MFA was disabled on Azure,” says Knode.
With MFA turned off, NodeZero stuffed the newly captured credential and the issue bumped up to a 9.9 on the criticality scale. Implementing Multi Factor Authentication is recommended throughout network zones and data access points, and it was highly recommended that MFA was turned “on” for cloud access, limiting an attacker’s ability to take advantage of their Azure service.
Some of these paths can get complicated, but there are fix-actions the customer can go forward with.
“They have password and credential policy problems, but there were some really high priority fixes they could remediate and see immediate risk reduction,” says Knode. “You don’t have to fix everything. You can fix what matters most, and then verify the fix by running a pentest and aligning it to the scope to see immediately if the fix worked.”
What are you using, and does it work?
One question that comes up time and time again in IT is: are the solutions I’ve already paid for effective?
The NodeZero customer success team asks an organization if they received any alerts about this vulnerability. Was it detected, logged, alerted to, and was it stopped?
In these instances, this did not happen.
When NodeZero was able to dump these credentials, an EDR should absolutely have issued an alert and their antivirus solution should have stopped it.
“We recommend looking into this,” says Knode. “We’re transparent with every action NodeZero takes, so you can go through and see. Export the report and take a look.”
We recommended this organization go back, check logs to see if the incident was detected and logged, and if it wasn’t, ask how someone was able to dump your credentials and why it wasn’t logged, alerted, or stopped.
“Nobody should be able to do this without setting off a trigger and an alert,” says Knode.
From there Horizon3.ai went through the ops, helped plan a strategy, and looked at next steps. Customers can also take the information NodeZero provides in its reporting features to take the steps on their own.
“We’re not trying to ‘pwn’ organizations, we’re not trying to poke them in the face and make them look bad – we want to make sure their security stack is putting out every ounce of protection they want from it,” says Knode.
Want to see NodeZero in action for yourself? Schedule a demo today.