“Who cares that the intern was phished during our phishing campaign? It’s an intern, they don’t have access to anything important.”
As a security practitioner, that mindset among business leaders drove me nuts. There are many ways a credential as innocuous as an intern’s could be used by an attacker to compromise a domain or gain access to sensitive data, but it was very difficult to articulate the “blast radius” of a phished credential.
That’s why I’m really excited to launch the new Phishing test type within NodeZero…
- A user sets up a phishing campaign using KnowBe4, Proofpoint, Mimecast or other phishing test tools.
- That user adds a few lines of javascript generated by NodeZero to their phishing page.
- Credentials caught by KnowBe4 are automatically injected into a running NodeZero pentest via the javascript copied into the phishing page.
- NodeZero then uses those phished credentials as part of its attack, finding ways to chain together credentials, misconfigurations, CVEs, and dangerous product defaults to achieve a technical objective (e.g. Domain Compromise, Sensitive Data Exposure, etc).
- The user gets a detailed report of the blast radius for every credential phished by the KnowBe4 campaign.
The NodeZero Phishing Impact test is first-to-market and gives you the ammunition required to drive meaningful improvements to the credential attack surface of your organization.
“Actually boss, the intern’s credentials enabled the attacker—NodeZero—to gain access to our sensitive financial data. Take a look for yourself…”
Why is understanding the blast radius of a phished credential important? Here’s a real-world example of how a phished credential led to a domain admin compromise…
Setup:
- A phishing campaign was configured and executed using KnowBe4.
- A few lines of javascript were added to the fake KnowBe4 page to safely channel phished credentials into a running NodeZero internal pentest.
- As phished credentials started flowing into NodeZero, NodeZero used them as part of its attack.
Attack path:
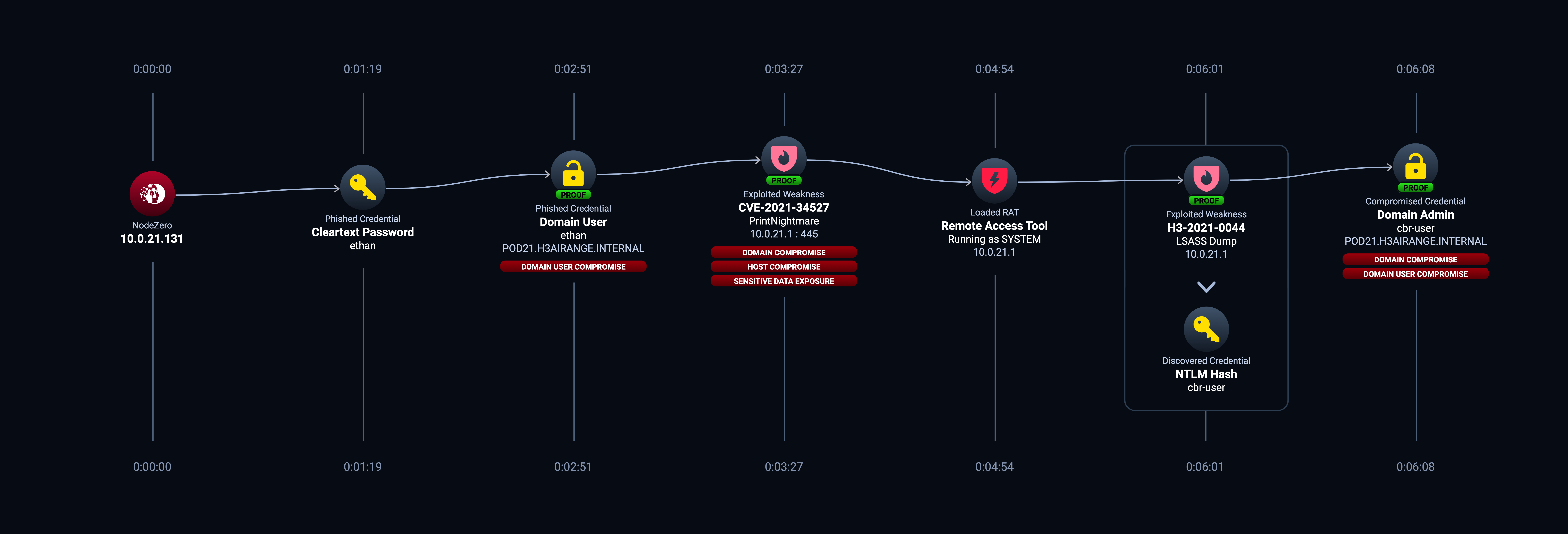
- NodeZero uses the phished credential to successfully exploit PrintNightmare on Host1. PrintNightmare (CVE-2021-34527) is a remote code execution vulnerability in the Windows Print Spooler service that allows an attacker to run arbitrary code with system privileges. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
- With those system privileges, NodeZero successfully drops a remote access tool (RAT) on the compromised host, which allows it to access sensitive processes like Security Account Manager (SAM), LSA, etc. A properly configured EDR like CrowdStrike, SentinelOne, or Fortinet is supposed to prevent the RAT from successfully deploying, but it’s easy to misconfigure these tools.
- With the RAT successfully deployed, NodeZero then dumps SAM and harvests several user-ids and their corresponding NTLM hashes. SAM is a database that is present on Windows machines that stores user accounts and security descriptors for users on that machine.
- The compromised credential has both local admin privileges on the host and has domain admin privileges within the domain. This means the attacker (NodeZero) now has the keys to the kingdom.
tl;dr PrintNightmare is the CVE that enabled the attack path. An attacker requires a valid domain user credential in order to exploit Printnightmare. In this case, the attacker – NodeZero – successfully obtained that valid domain user credential via the phishing integration.
In addition, the customer had to investigate why their EDR did not successfully stop the deployment of the RAT on the compromised host, which provided the second critical step in the journey to domain admin compromise.