This will be a series following my “journey to secure” since joining my organization. I want to preface that this is in no way a blueprint everyone can follow, but it is logic and items that I used to understand the business, current security state, and leadership visions for building an internal security program. Our job as security practitioners is to keep the needle moving forward by maturing security for an organization. The “journey to secure” never stops, and is crucially important in the highly interconnected digital age we live in.
The culture of the company dictates how easy this journey to secure can be, or the trials and tribulations you will face. The sad truth for the “blue team” about protecting your organization is your goal is 100% perfection. It’s an impossible task as no one is perfect. The flip side to this is the bad guys just have to be right once. The bad guys can have millions of failures and it is acceptable. That single attempt that worked for the bad guys and got through the perfect defense of the blue team is all that matters.
Understand that this is a journey. You won’t solve the world’s problems tomorrow. You need to be agile enough to respond to new threats, you need to have enough vision to plan out your journey and increase the security posture for your organization.
First 90 Days
DON’T MAKE CHANGES!!! This kills me every time I see people trying to implement or change a process almost immediately out of the gate when they join a company. In my experience, once you embark at a new company, you haven’t even been fully onboarded yet in your first 90 days. You don’t fully understand the company and what makes it tick. You don’t know how your change will affect the day-to-day work of users. In reality I’ve seen the average onboarding time for when people feel comfortable and know who to ask to get answers is about 6 months. You have to understand the current state and the environment. You need to LISTEN to your subordinates, peers, and leaders. You have to ABSORB this data and information so you can make tactical changes to actually improve a process or seal a gap. Am I saying don’t do anything at all during this time? No. You can plan and start laying out your roadmap and vision as you learn what’s currently in place as well as what’s missing. You need to identify gaps as well as enhancements that you can bring to the company to move the needle forward for security. You need to make sure that you’re doing meaningful security practices and not security theater that so many people are blinded with.
In my first 90 days, I listened to everyone I could have conversations with. I started to develop my “network” within the company so people would know who I am and what my visions and goals are. This allowed me to listen, absorb, and see what are the systemic issues currently being faced within the organization as well as the things that are being done really well already. This gave me credibility with the team to know that I’m here to help them and not be a burden. At the end of the day we are one team. We all work at the same company and want it to thrive and be successful. By ingraining myself into the team this gave me personal relationships so people understood who I am as a person, and that deep down I intend to do the right thing even if it’s not the popular thing. I realized this is a startup company, a highly specialized cybersecurity startup–so there are some very intelligent individuals within this organization who have been implementing security controls since the inception of it. I had 5,000,000 things going through my head for questions and I still do. What’s our attack surface? What are our biggest risks? What controls do we have in place? Are the policies and standards accurate? Are we doing what we are stating in our policies? I can go on and on with the amount of questions I had going through my head and asking teams to get data and notes. I asked questions, made notes, and devised a plan while being agile enough to be ready to swap what I thought was a priority to something else based on feedback or trends we were seeing that needed to be addressed. Always ask questions. The moment you stop asking questions is the moment you stop learning.
First 90 Done, What now?
From the first 90 days I saw a recurring trend coming from VRAs (Vendor Risk Assessments) from prospective clients, emails between teammates, and chat messages. We had variations of Phishing and Smishing attempts happening within the org. We had our annual Cybersecurity awareness training that met the checkbox for all regulatory requirements. Does meeting the checkbox for compliance mean that what you have in place is effective? No, it does not. We had a baseline that allowed us to meet regulatory compliance but everyone was not on the same page for what to do when they got phishing, smishing, or vishing attempts. The company didn’t have a repeatable process for users to follow in that situation. They didn’t know what to do. So I set out with a focus on the below (not in any specific order):
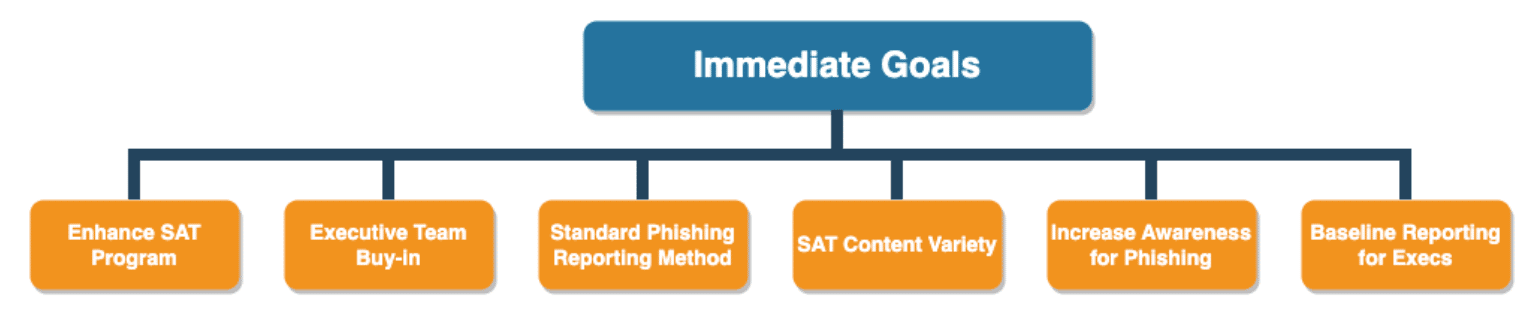
The security awareness training and process for handling phishing attempts needed to be improved. Based on the population size of the company this wouldn’t be a huge overhaul though it would be challenging, but would allow me to solve a systemic problem. Technical wouldn’t be the challenge here as there are a lot of solutions that provide simulated phishing and Security Awareness Training (SAT). The challenge with this program is the human aspect of it. We needed to change human behavior. We need to coach people on what to do and how to do it. So how do you achieve that change?
The first thing you need is to make sure you have leadership buy in. The leadership buy in allows them to go to bat for you and support the program when you have push back. Any one who has ever implemented any security solution will know there will always be pushback. So you need the leadership buy-in to have a leg to stand on for when the pushback happens.
For me it ended up being the perfect storm as I got lucky on the timing of everything. I paired the launch of our Phishing and SAT platform with Cybersecurity Awareness Month. This allowed me to pair the launch with frequent communication to the organization so they adopted instant familiarity with the platform. In preparation of the launch I created a SAT Policy that used a “rewards” based system. Those rewards were for successes as well as failures. Well how do you reward a failure? You reward it with training and education. Educating someone so we can be better as individuals is a great reward. For full transparency there are some negative rewards for failures as well, but I made sure when developing the phishing and SAT program I gave every opportunity to the users before those come to fruition.
I wanted basic repeatable metrics that clearly told the story that I was trying to tell, which at the end of the day metrics are just stories of what you’re telling. I decided to use the below as my quarterly reporting areas to show where we needed to educate the company.
- Phishing
- Some failure criteria metrics per a phishing campaign such as these
- Clicked Links
- Data Entered
- Replied to
- Success which in my mind is the more important metric out of all of these
- Reported
- Some failure criteria metrics per a phishing campaign such as these
- Training
- Completed percentage for a training campaigns
Outcome so far
Since the overhaul of the program this is what we are currently showing.
- We are seeing increased conversations around phishing and security awareness training happening in our internal chat platform. This includes both good, bad, sarcastic, and indifferent conversations.
- Showing a continual increase of users reporting phishing or suspicious emails via the phishing button that was implemented.
- Security Awareness Training there was a large adoption rate for the security content and material.
Is what I implemented perfect? No, even though I would love to think that it is. Does it give us a foundation to improve from? Yes! Does it provide value? YES! Education is one of the strongest things you can do for users. Not only is this education intended for the users but it’s education for myself and the team on creating effective playbooks for handling situations and improving. This allows the most seasoned professional or the person fresh into the workforce getting their foot into cybersecurity to have the same response to the situation every time. We have built a SAT program to give monthly training modules to everyone. I now have the platform to iterate through the feedback that I’m getting from the user population to make things better. I can do this by driving our users towards not blindly clicking links, reporting something they and don’t assume someone else has, and raising our security awareness as we being cybersecurity professionals aren’t excluded from the lessons we preach. As I stated at the beginning of this, no one is perfect, but we can always strive to be better. That’s what I’m trying to achieve here. Make myself better a security practitioner and leader, but also make the company better via our security practices and a smiling face that is here to help anyone and everyone that I can.
Until the next time.
Stay vigilant.



