Is your TrendMicro Apex One EDR working as it should? If your answer to the question is ‘yes,’ then think again!
Endpoint, detection, and response (EDR) solutions are designed to detect, log, alert, and potentially stop malicious activities by cyber threat actors. NodeZero, Horizon3.ai’s fully autonomous pentesting platform, is designed to identify whether your security stack, including your EDR, works as expected. Whenever NodeZero runs a pentest and dumps credentials, it is apparent that our customer’s EDR solution did not stop the technique. The question then arises: was it able to detect, log, and alert the activity?
Internal NodeZero data collected from our customers’ operations shows that credential dumping-related techniques have been successfully launched on a majority of clients with the TrendMicro Apex One EDR solution.
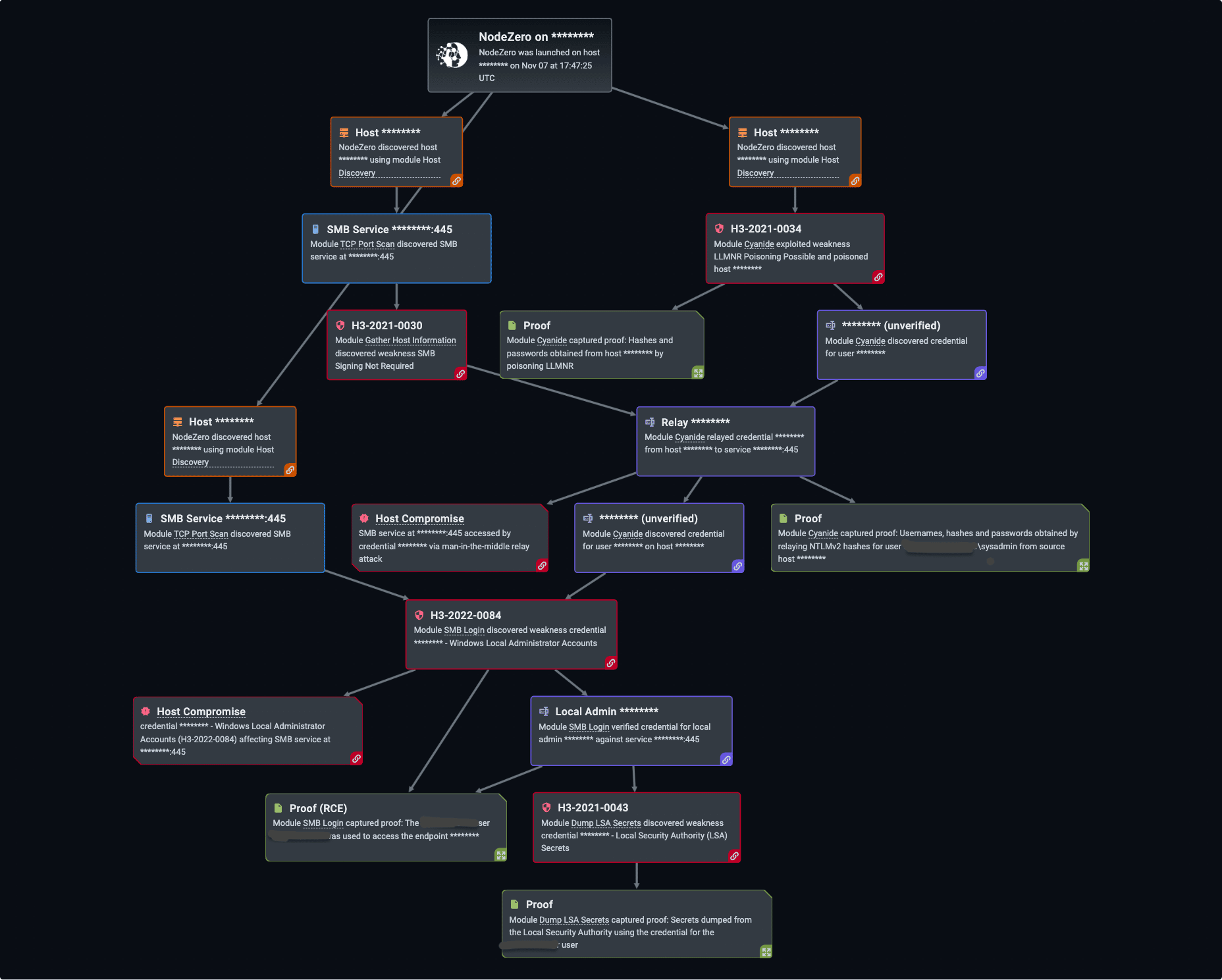
In one case, NodeZero ran on a customer’s single network with a scope of 131 subnets. NodeZero was able to exploit multiple attack paths, dumped credentials, and provided the proof on:
- 153 credentials from LSA (Local Security Authority)
- 141 credentials from LSASS (Local Security Authority Subsystem Service)
- 154 credentials from SAM (Security Account Manager)
- 170 credentials from credential reuse
This customer employed TrendMicro’s Apex ONE, an EDR with behavioral machine learning (ML). They were certain their EDR should have detected and blocked the attack. While all the hosts in question had the TrendMicro agent installed and running, the agents weren’t able to:
- Stop: The EDR solution did not prevent the credential dumping and NodeZero was able to execute T1003 ATT&CK with impunity.
- Alert: Correlating time and target data between NodeZero’s “Action Logs” and Apex One on the customer’s side proves the EDR did not generate any alerts, and their security team confirmed not receiving any notifications.
- Log: After an exhaustive review with the client, there was no evidence that the EDR logged credential dumping on any of the hosts.
- Detect: Without any log for the record, there was no evidence that the EDR detected the activity.
The absence of detection, logs, alerts, and prevention is a clear indication that the EDR is not tuned and working as it should.
TrendMicro Apex ONE identifies activities with CVEs and MITRE ATT&CK tactics and techniques. For OS credential dumping detection, the T1003.001 (LSASS), T1003.002 (SAM) and T1003.004 (LSA) flags should be checked and enabled. This is a pull-down menu where a customer can select if they’d like to only log the detected activity, escalate, and alert on the activity, and even prevent a credential dump when detected. In this case, and upon further review, the Horizon3.ai team discovered that the EDR credential dumping detection was turned off by default.
We continue to help many of our clients to fine-tune their EDR solutions to work effectively. Let’s do the “checks and balances” work together by ensuring your TrendMicro Apex ONE solution flags credential dumping. And, of course, don’t forget to flip it back to on!