On 22 January, Ivanti published an advisory stating that they discovered two new, high-severity vulnerabilities (CVE-2024-21888 and CVE-2024-21893) after researching previously reported vulnerabilities affecting Ivanti Connect Secure, Ivanti Policy Secure and ZTA gateways. Ivanti provides enterprise solutions, including patch management and IT security solutions to over 40,000 customers worldwide.
While there is no evidence of any customers being impacted by CVE-2024-21888, Ivanti has acknowledged CVE-2024-21893 has impacted some customers in targeted instances.
- CVE-2024-21888 (CVSS Score 8.8) – A privilege of escalation vulnerability in the web component of Ivanti Connect Secure (9.x.22.x) and Ivanti Policy Secure (9.x.22.x) allows a user to elevate privileges to that of an administrator.
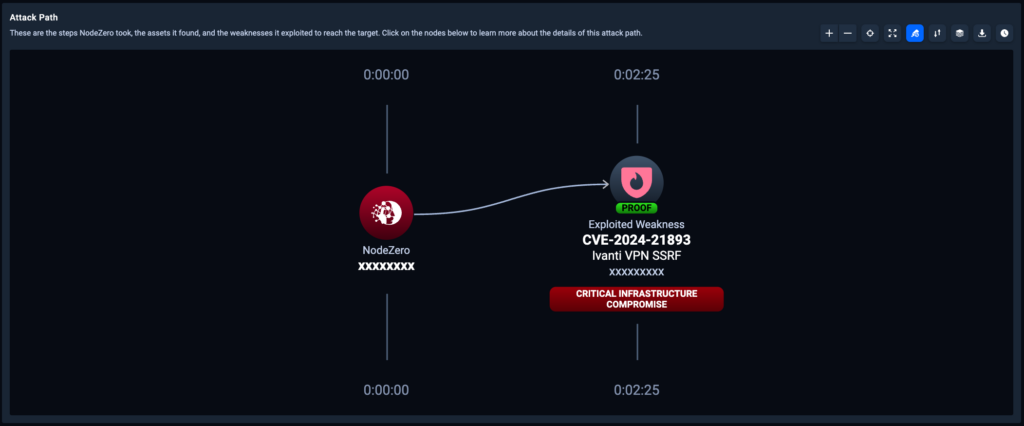
- CVE-2024-21893 (CVSS Score 8.2) – A server-side request vulnerability in the SAML component of Ivanti Connect Secure (9.x.22.x), Ivanti Policy Secure (9.x.22.x) and Ivanti Neurons for ZTA allows an attacker to access certain restricted resources without authentication.
In response to the new Ivanti vulnerabilities, the Cybersecurity & Infrastructure Security Agency (CISA) ordered all federal government agencies to disconnect all instances of Ivanti Connect Secure and Ivanti Policy Secure from their networks until proper mitigation steps are taken and reported to CISA.
Who is Affected?
Users who are running Ivanti Connect Secure (9.x, 22.x) and Ivanti Policy Secure (9.x, 22.x) and Ivanti Neurons for ZTA.
How Can I Fix It?
Ivanti has released patches for Ivanti Connect Secure (versions 9.1R14.4, 9.1R17.2, 9.1R18.3, 22.4R2.2, 22.5R1.1 and 22.5R2.2) and Ivanti Policy Secure version 22.5R1.1 and ZTA version 22.6R1.3.
According to Ivanti, users can also import the “mitigation.release.20240126.5.xml file as a temporary workaround.
How Can NodeZero Help?
All NodeZero™️ users can run an autonomous pentest to determine if their systems are vulnerable to the Ivanti vulnerability. We also recommend running a follow-on pentest to verify that any remediation steps taken, such as patching, are effective.
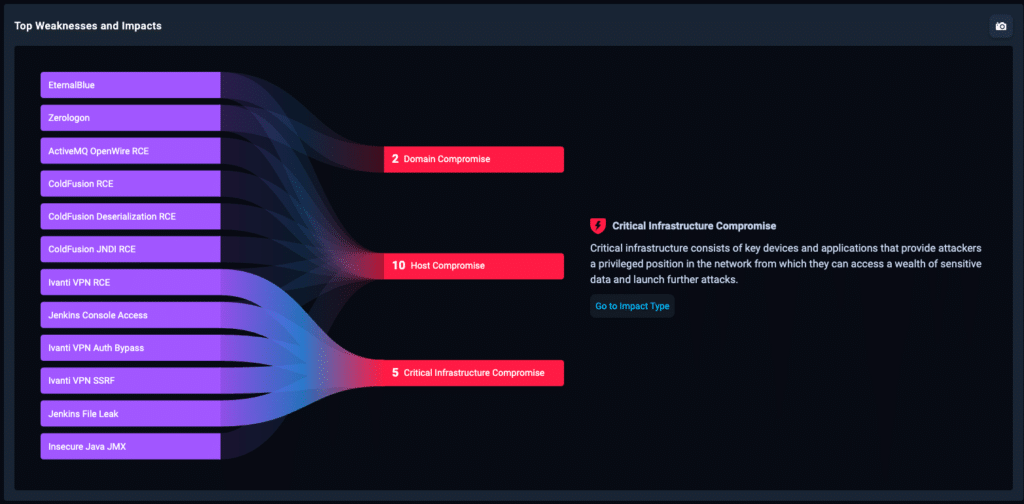
Example Impacts:
Example Attack Path: