Low-Level Vulnerability Leads to Domain Compromise
Although vast numbers of organizations purchase and utilize some sort of vulnerability management solution and may perform in-house penetration tests on their own networks, most struggle with knowing what not to fix because they lack context about what is truly exploitable. As a result, organizations spend vast amounts of time fixing issues that are of minimal risk.
There is a considerable difference between being vulnerable and being exploitable, and lacking context is an enormous challenge most organizations face. In many cases, organizations are using some sort of assessment tool that labels their findings with CVSS scores, but often they are of little use since these scores are primarily used to measure severity—and are not used to measure “your” risk. Severity refers to the seriousness of an issue, but risk refers to the possibility of loss or injury. If something is seen as not being severe, how much risk can really be involved? Lots.
It’s become all too clear that a more advanced pentesting approach is the only viable way to unravel the two questions that follow:
- How do we determine the difference between weaknesses that make our organization vulnerable vs. weaknesses that make us exploitable?
- How do we accurately prioritize each occurrence of a vulnerability finding based on its downstream impacts, and what should we fix first?
Let’s look at an example
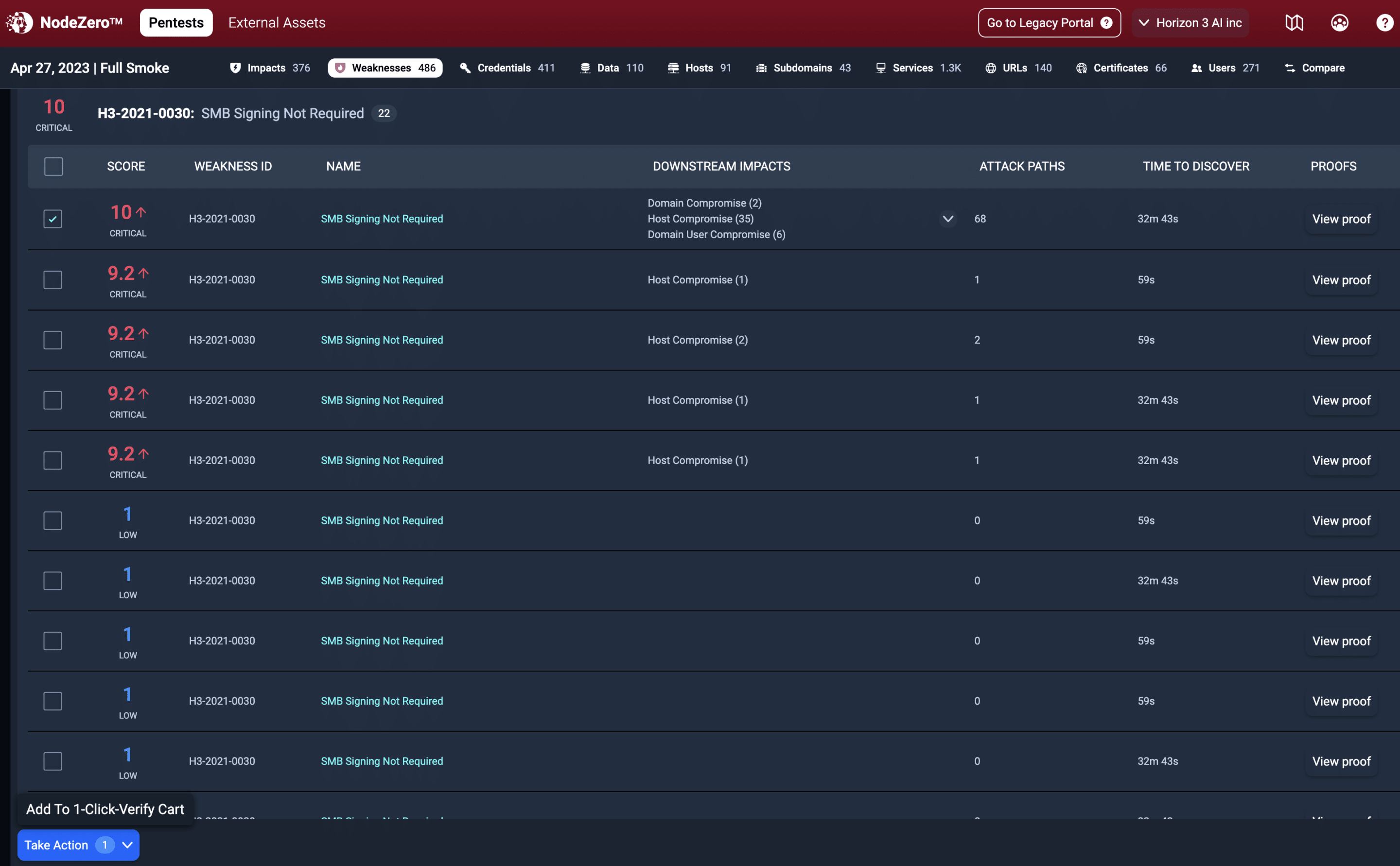
An SMB Signing Not Required vulnerability is a notable example of having a low severity CVSS score (~5.0) but can still be a substantial risk. The vulnerability is viewed as elevating risk because an unauthenticated, remote attacker could potentially exploit it to conduct man-in-the-middle attacks. Most people believe these attacks are difficult to pull off but that is not always the case. Remember, risk is all about the possibility of loss or injury.
Although SMB Signing Not Required has a low CVSS score, a savvy attacker can chain this misconfiguration together with other issues and become a Domain Administrator, compromise hosts and users, and/or gain access to sensitive data. And even worse, a run-of-the-mill vulnerability scanner will classify all occurrences of SMB Signing Not Required as “low” because vulnerability scanners lack the attacker’s perspective and provide little, if any context.
How is NodeZero™ different?
NodeZero is the industry’s first fully autonomous pentesting platform and is far more advanced than your typical vulnerability scanner. NodeZero will utilize each occurrence of an issue in an attack path, then it will accurately score each occurrence of that weakness based on its downstream impacts (see Figure 1), capturing the proof of exploitation along the way. In this example, NodeZero:
- Provides a true vulnerability SCORE
- Supplies the NodeZero WEAKNESS ID
- Delivers context into the number of DOWNSTREAM IMPACTS
- Shows all potential ATTACK PATHS
- Provides TIME TO DISCOVER
- And allows the user to select and view PROOFS
When looking at the SCORE column in Figure 1, we see that this risk is a 10+. Then when looking at the DOWNSTREAM IMPACT column, the at-risk hosts are exploitable to one or more of the following outcomes:
- Domain Compromise
- Host Compromise
- Domain User Compromise
And according to NodeZero, there are at least 73 attack paths where this vulnerability could be exploited. This is what we mean by “context-based scoring” which is much different than a CVSS score.
NodeZero has proven that a low severity issue suddenly has an extremely elevated risk of exploitation because it knows it could exploit these vulnerabilities and achieve domain, host, and/or user compromise.
Security teams now get context on what to prioritize
Once a security team receives the results from a NodeZero, they now understand what to prioritize for remediation. When they have remediated the issues at hand, they normally want to verify that they have properly fixed each occurrence of this issue.
Rather than having to rerun the entire pentest, security teams can select the specific occurrences they want to test and execute a “retesting” workflow on NodeZero, which is a narrowly scoped pentest that only checks for those specific weaknesses. Not only do they immediately know what to fix, they can also prove that their fix was effective. This is a valuable time-saving feature.
Key takeaway
Context-based scoring on downstream impacts, combined with our retesting workflow, is one of the most used features within NodeZero. This enables organizations to accurately prioritize fixing security weaknesses that can be exploited, then quickly verifying that the detected issues have been remediated. In all reality, context into risk is what matters most.