Recent CVE Affecting Veeam Backup Software Leads to Domain and AWS Takeover
Veeam Backup and Replication software is commonly used by enterprises for data protection and ransomware recovery. Earlier this year a vulnerability affecting Veeam,CVE-2023-27532, was disclosed. This vulnerability enables attackers to dump highly privileged credentials used by Veeam for backup operations.
NodeZero has been able to successfully exploit the Veeam CVE in many environments. In the example below, NodeZero leveraged the Veeam vulnerability to fully compromise a client’s on-prem environment and AWS infrastructure.
To be clear, attack paths that NodeZero discovers are completely valid paths that an attacker could take, and in doing so, can completely lead to compromise. This is a real attack performed by NodeZero with no human penetration testers involved. The attack was executed safely against production systems that were not in a lab environment.
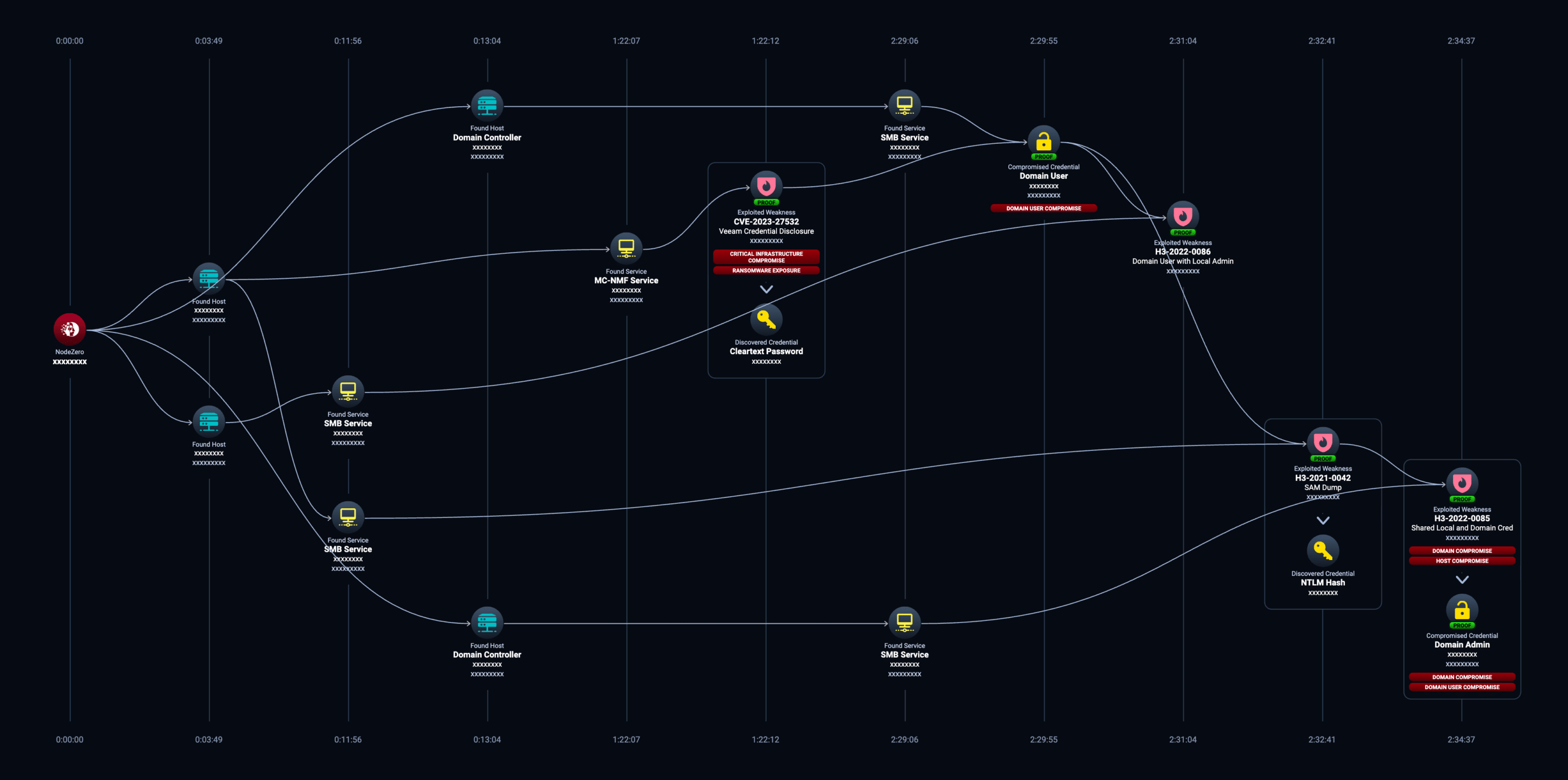
Attack Path #1: The Path to Domain Compromise
In this attack path, NodeZero leveraged 4 weaknesses, one being the recent Veeam CVE to become domain admin. The attack path involved 2 compromised credentials and spanned 4 hosts.
NodeZero started off as an unauthenticated member of the internal network. Then:
- NodeZero was launched from host x.x.x.x on ~Jun 19
- NodeZero discovered the Veeam Backup and Replication service running in the environment on port 9401.
- NodeZero identified that the Veeam service is vulnerable to CVE-2023-27532 (Veeam Backup and Replication Credential Disclosure Vulnerability). NodeZero exploited the vulnerability to dump cleartext credentials from Veeam.
- One of the credentials NodeZero acquired from Veeam is for a domain user, service1. NodeZero verified service1’s credential by logging into the domain domain1 as that user over SMB.
- NodeZero discovered that service1 has local Administrator privileges on a Windows machine, machine1. NodeZero raised a new weakness, H3-2022-0086: Domain User with Local Administrator Privileges.
- Logged in as service1 on machine1, NodeZero dumped credentials (NTLM hashes) for all local users from the Security Account Manager (SAM) database. NodeZero raised a weakness H3-2021-0042: Credential Dumping – Security Account Manager (SAM) Database
- One of the NTLM hashes NodeZero acquired from the SAM dump on machine1 is for a local user admin1. Using a Pass-the-Hash attack, NodeZero discovered that the credential for admin1 also happens to be a domain user on domain1. NodeZero raised a weakness H3-2022-0085: Credential Reuse – Shared Windows Local User and Domain User Accounts
- NodeZero further identified that domain user admin1 is a domain admin.
In other words, NodeZero proved it could become a domain admin and takeover all machines connected to the domain in approximately 2.5 hours. Figure 1 highlights this attack path.
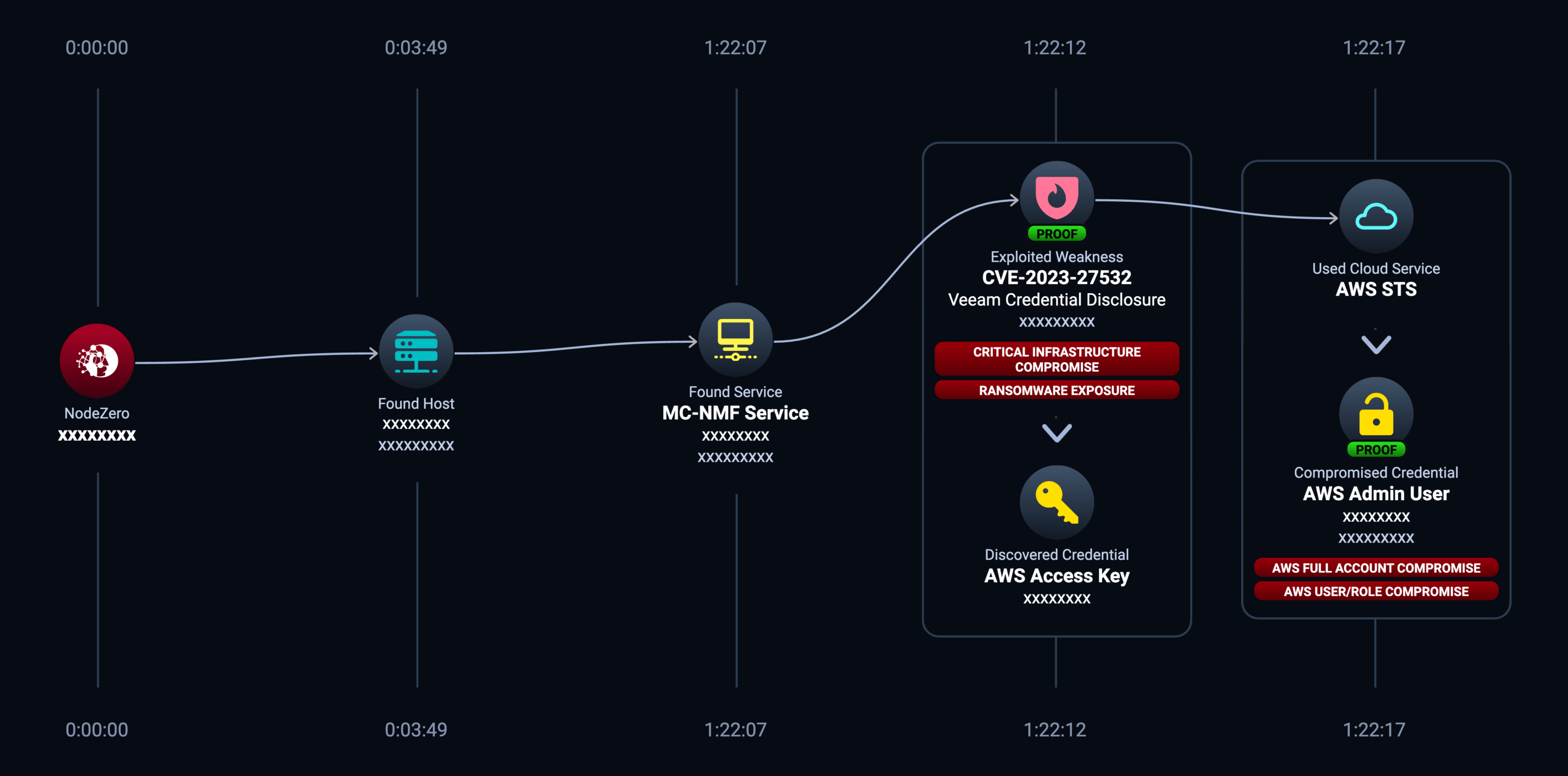
Attack Path #2: The Path to AWS Compromise
Now let’s look at another attack path in the same environment that led to full AWS account compromise via the same Veeam CVE.
- NodeZero was launched from host x.x.x.x on ~Jun 19
- NodeZero discovered CVE-2023-27532: Veeam Backup and Replication Credential Disclosure Vulnerability affecting the MC-NMF service on Veeam1 port 9401
- NodeZero discovered an AWS Access Key XXXXXXXXXXXXXXXXXXXX on the MC-NMF service on Veeam1 port 9401 by exploiting CVE-2023-27532: Veeam Backup and Replication Credential Disclosure Vulnerability
- NodeZero verified the credential for AWS admin user aws1 in AWS account xxxxxxxxxxxx on AWS STS (Security Token Service)
NodeZero executed the attack path in Figure 2 in about 1 hour and 20 minutes. NodeZero would go on to compromise other AWS accounts this organization used with the same credential.
Key Takeaways
The attack path examples above highlights the value of autonomous pentesting.
One of the interesting aspects of the Veeam CVE is that it is rated as a 7.5 (High) by the National Vulnerability Database (NVD). In many organizations, this vulnerability would not be prioritized for patching relative to other Critical level vulnerabilities. The reality, as proven here by NodeZero, is that exploiting this vulnerability can lead to full compromise. NodeZero can be used to assess the true impact of a vulnerability in any environment
In addition to the Veeam CVE, NodeZero also identified and exploited other important weaknesses common in many environments: over-privileged domain users, insufficient EDR controls to prevent credential dumping, and credential reuse. In the attack path to domain compromise, the Veeam CVE provided NodeZero initial access, and the subsequent weaknesses enabled NodeZero to take over the domain. NodeZero performed the same actions a human pentester would by chaining multiple weaknesses together to arrive at the greatest impact possible.