Active Directory Analytics Solution Enables Domain Compromise
Due to lessons learned from the SolarWinds breach a few years ago, organizations should be wary of products that require privileged credentials since they may have the potential of increasing risk. In similar context, here is an example of a NodeZero™ successfully compromising the ADAudit Plus admin credential during a penetration test to become a Domain Admin.
Background
ADAudit Plus is a user-behavior analytics solution from ManageEngine that audits all access to active directory (AD) to identify anomalous behavior. According to the product website, “ADAudit Plus provides a clear picture of all changes made to your AD resources … [and] helps detect and respond to insider threat, privilege misuse, and other indicators of compromise, and in short, strengthens your organization’s security posture.” ADAudit Plus is required to be configured with a high privilege domain user credential to function.
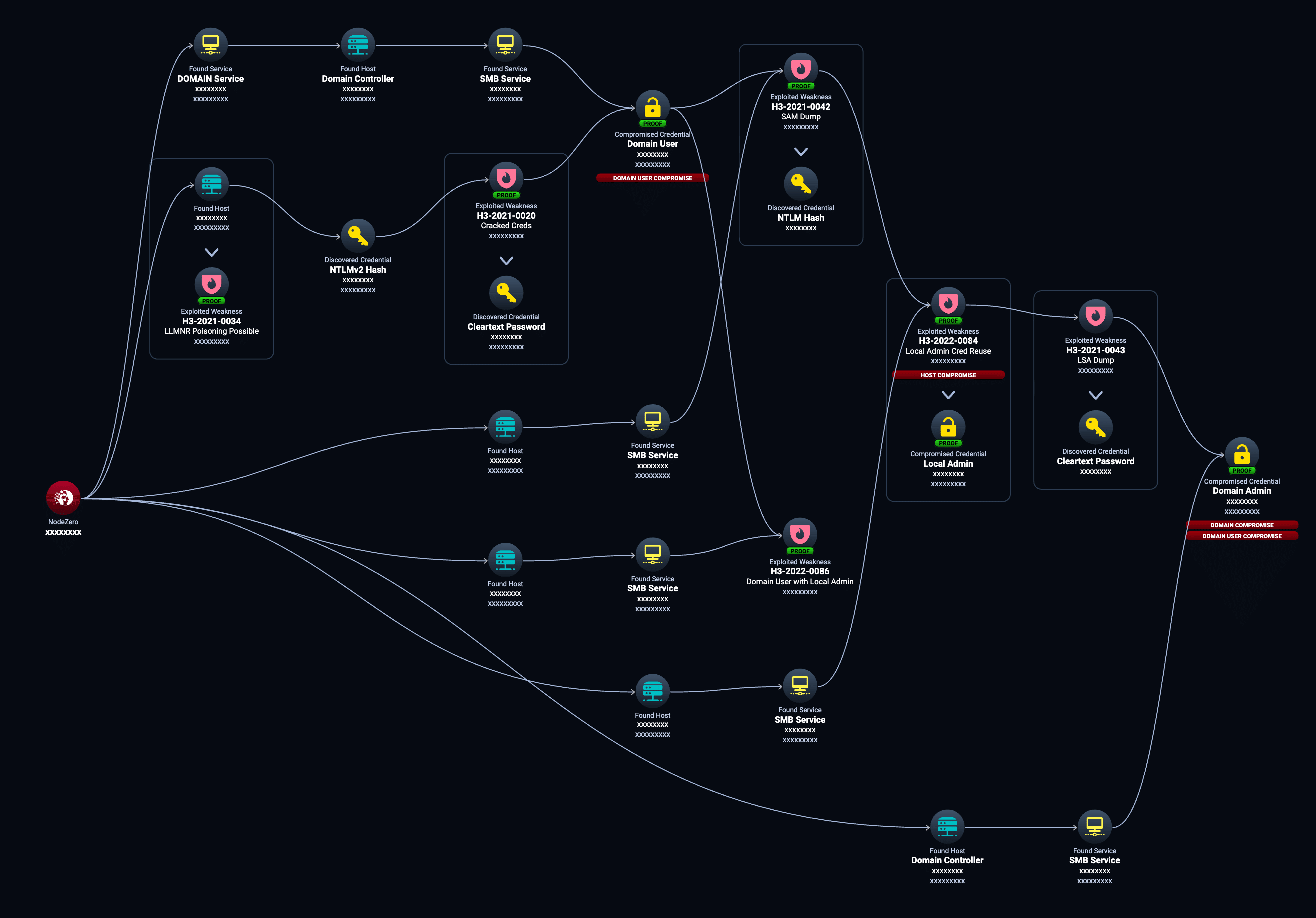
In this attack path example, NodeZero performs the following steps to discover the ADAudit credential that eventually led to domain compromise. Note that this penetration test was against real production systems and no humans were involved in this discovery.
In this example case, NodeZero:
- NodeZero poisoned LLMNR network traffic originating from host host1 and acquired the NTLMv2 hash for domain user user1.
- NodeZero cracked the hash for user1 and logged in as user1 to the domain.
- NodeZero determined user1 had local admin privileges on a host host2.
- NodeZero logged into host2 as user1 and dumped the Security Account Manager (SAM) database file containing all local user credentials in NTLM hash format. One of the credentials dumped was for a local administrator user.
- NodeZero found the local administrator credential was being reused on another host host3. NodeZero “passed the hash” and logged in as a local administrator on host3.
- NodeZero used the local administrator credential on host3 to dump credentials from the Local Security Authority (LSA secrets). Among these secrets was the cleartext credential for the domain user adauditplus configured with ADAudit Plus.
- NodeZero logged in as the adauditplus user to the domain and discovered it was a domain admin.
Along the way, NodeZero identified and raised the following weaknesses:
- H3-2021-0034: LLMNR Poisoning Possible affecting host host1.
- H3-2021-0020: Weak or Default Credentials – Cracked Credentials affecting the credential for user1.
- H3-2022-0086: Domain User with Local Administrator Privileges affecting the credential for user1 on host2.
- H3-2021-0042: Credential Dumping – Security Account Manager (SAM) affecting host2.
- H3-2022-0084: Credential Reuse – Windows Local Administrator Accounts affecting the administrator credential on host3.
- H3-2021-0043: Credential Dumping – Local Security Authority (LSA) Secrets affecting host3.
Why is this frustrating?
First, the role of ADAudit Plus is to monitor for these types of credential-based attacks. It is ironic that a tool that is supposed to help users detect AD attacks is itself something that can be used to compromise AD in the end.
ADAudit does not require a domain admin credential, but users often set up the ADAudit credential to have domain admin privileges. ADAudit makes it easy to run with a domain admin but more work is required to configure a new account with least privileges that users don’t often want to spend the time to do.
Ultimately, and as shown in Figure 1, NodeZero chained six different issues together and none of them were CVEs. They were all misconfigurations or weak credentials across six different hosts, buried among thousands of hosts, to find this successful attack path.
Key takeaway
The attack path NodeZero executed above was primarily enabled by two key issues: Privilege Management and Weak Security Controls.
Privilege management came up twice. The first domain user NodeZero acquired had local admin rights on a system, allowing NodeZero to use it to dump credentials. And the domain user credential for ADAudit Plus that NodeZero discovered at the end, turned out to be a domain admin, even though it didn’t need to be.
NodeZero also performed OS credential dumping twice, once to dump SAM and another time to dump LSA secrets, yielding credentials that furthered the attack. EDR was either not present or not configured to block credential dumping.