CISA Known Exploited Vulnerability Enables Initial Access and Lateral Movement Leading to Domain Compromise
Here is a real-world example of NodeZero exploiting a recently disclosed, pervasive vulnerability in an internal pentest to fully compromise a client environment.
Background
Apache ActiveMQ is a Java-based message broker used as a part of many software products. It is backend infrastructure that facilitates communication between different software components operating in a distributed architecture, similar to Redis and RabbitMQ.
At the end of October 2023, a critical vulnerability, CVE-2023-46604, affecting ActiveMQ was disclosed. This vulnerability enables unauthenticated attackers to compromise the host running ActiveMQ by sending a crafted network request to the broker’s Openwire port (default port 61616). Similar to Log4Shell, the exploit induces the vulnerable ActiveMQ instance to connect back to an attacker-controlled server to download a malicious payload. The vulnerable ActiveMQ instance unmarshalls the payload, resulting in the execution of arbitrary operating system commands contained in the payload, leading to host compromise.
The vulnerability was immediately exploited in the wild by threat actors, landing it on CISA’s known exploited vulnerabilities (KEV) catalog. As of this writing, according to Shodan there are thousands of ActiveMQ instances exposing the Openwire port to the Internet, with the majority of these instances in China.
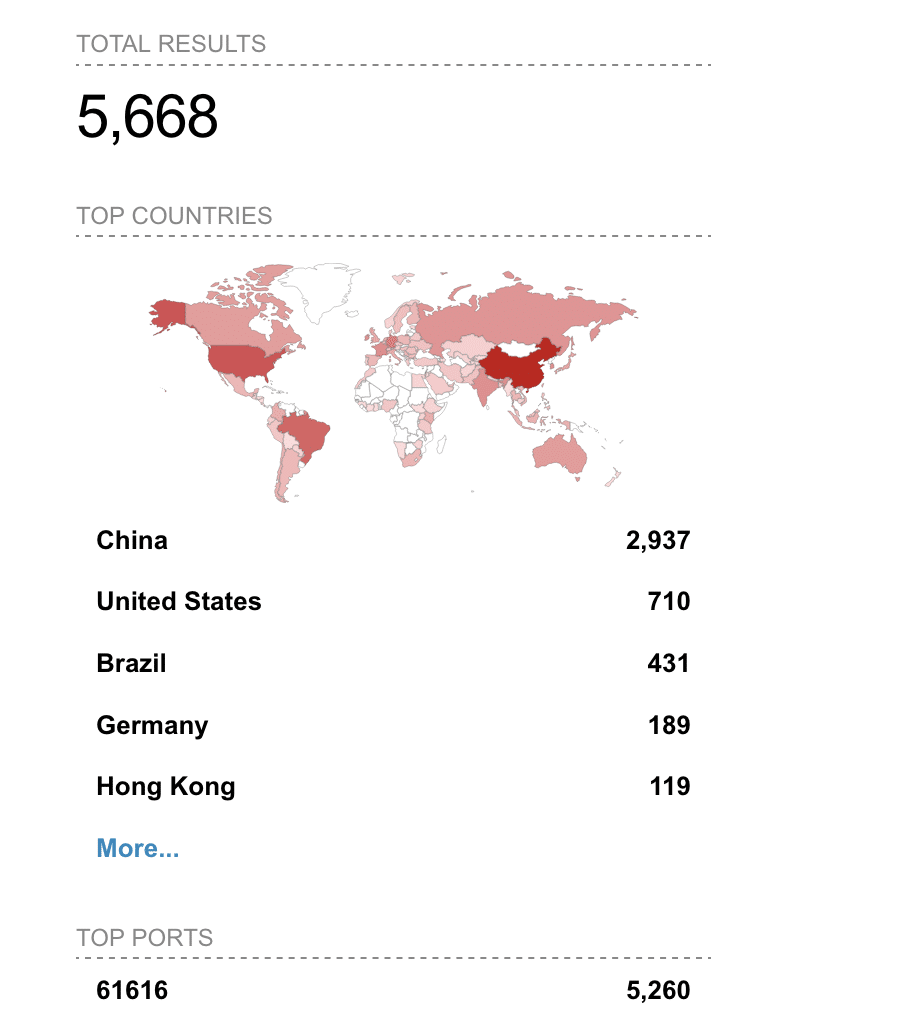
While dangerous externally, the vulnerability is an order of magnitude more dangerous and prevalent in internal networks. ActiveMQ is installed as part of many software products, including Atlassian Bamboo, Commvault, Powerschool SIS, and Solarwinds WebHelpDesk.etc. This is the type of vulnerability that will linger in internal networks, and be fodder for pentesters and attackers alike for years to come.
A Real World Example
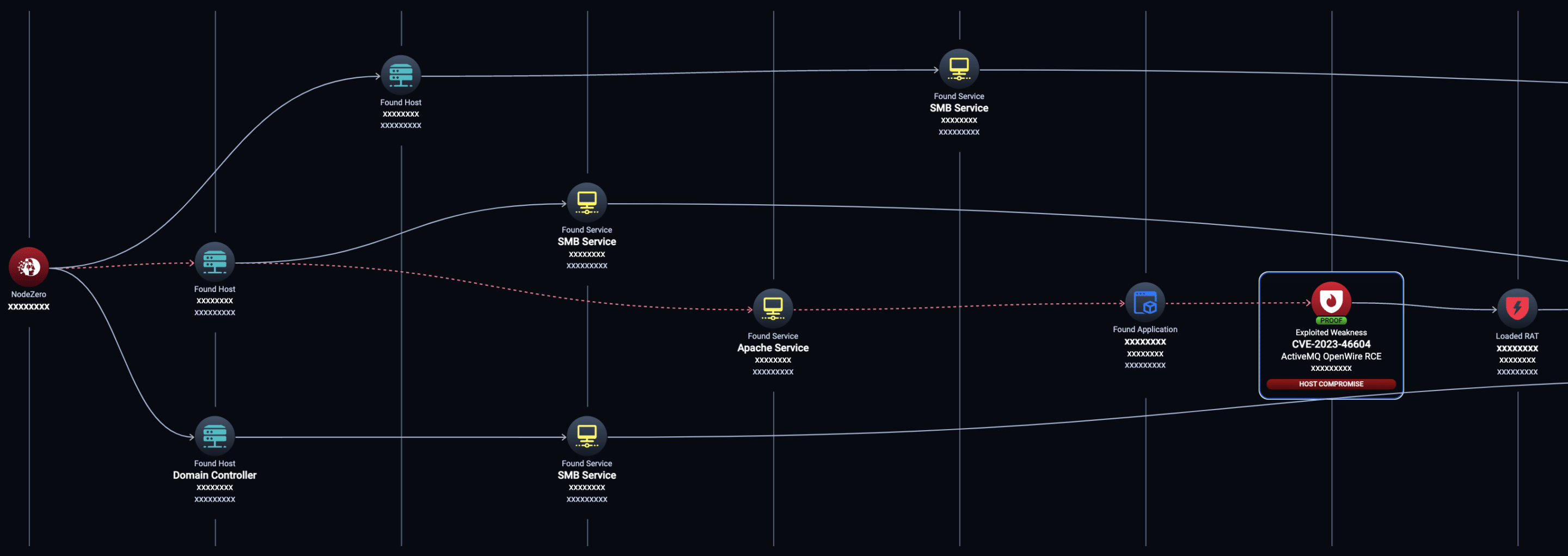
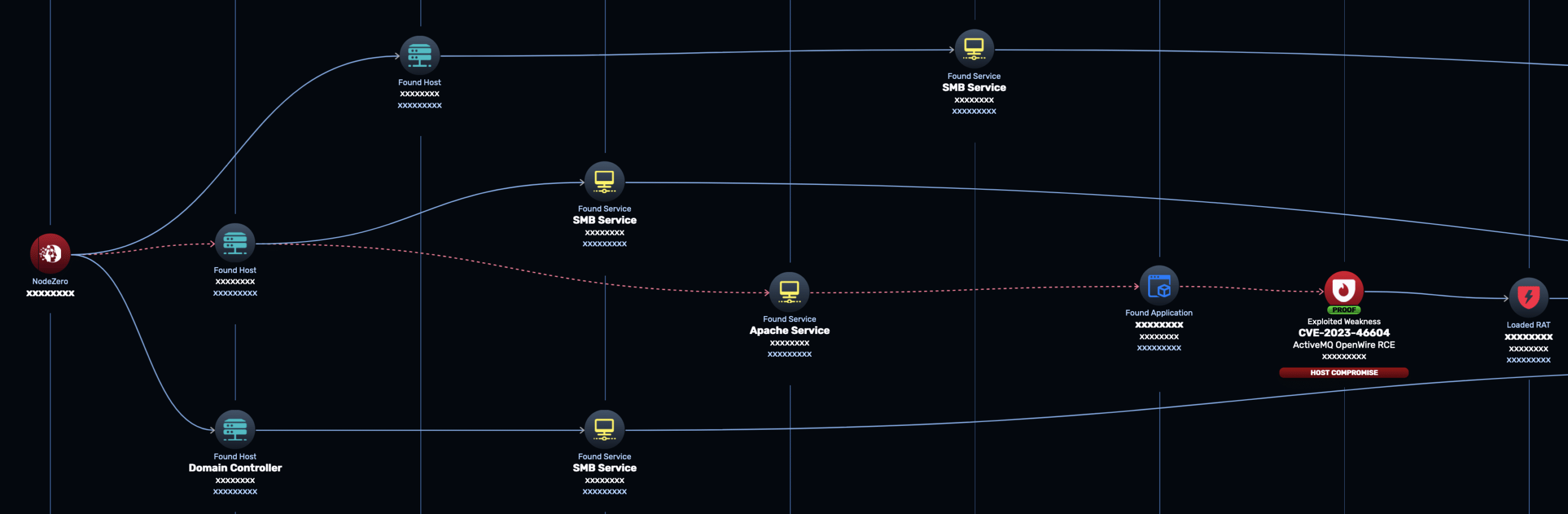
Within days of public disclosure, an exploit for CVE-2023-46604 was added to NodeZero. Here’s an actual production internal pentest in which NodeZero exploited this vulnerability to ultimately compromise the domain administrator account.
- First NodeZero identified the Apache ActiveMQ broker service running on the default port 61616 on a host in the network.
- NodeZero checked for CVE-2023-46604 and then exploited it to install a Remote Access Tool (RAT) on the vulnerable host.
- Through the RAT, NodeZero dumped credentials from LSASS. One of these credentials was the NTLM hash for a domain user. NodeZero “passed the hash” to login as domain user on the network.
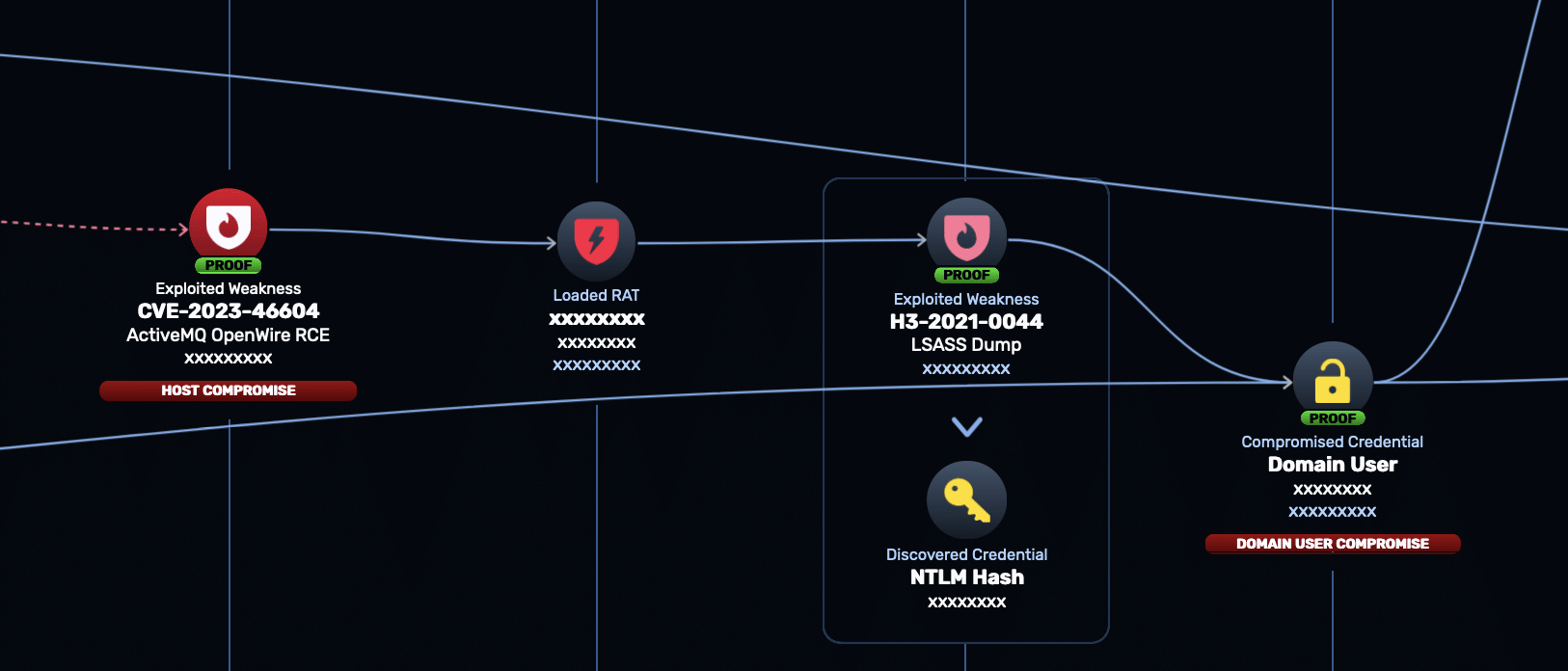
- Next, NodeZero identified that the compromised domain user was also a local admin on another host in the network. Using the administrative privileges of this domain user, NodeZero installed a second Remote Access Tool on this second host.
- NodeZero once again dumped LSASS through this RAT. This time NodeZero acquired the NTLM hash for a domain administrator, which it used to log in to the domain.
Takeaways
It took NodeZero about 1 hour and 15 minutes to execute the attack path leading to domain compromise. This attack was performed autonomously with no human assistance or prior scripting. Along the way, NodeZero identified and raised the following weaknesses:
- CVE-2023-46604: Apache ActiveMQ Openwire Transport Remote Code Execution Vulnerability
- H3-2021-0044: Credential Dumping – Local Security Authority Subsystem Service (LSASS) Memory
- H3-2022-0086: Domain User with Local Administrator Privileges
While CVE-2023-46604 provided NodeZero initial access to a host in the network, the subsequent weaknesses – lack of security controls preventing LSASS dumping and a over-privileged domain user – enabled NodeZero to move laterally in the network and compromise the domain. NodeZero can help you stay on top of emerging weaknesses, and it can help you harden your security controls and credential policies to prevent widespread compromise.