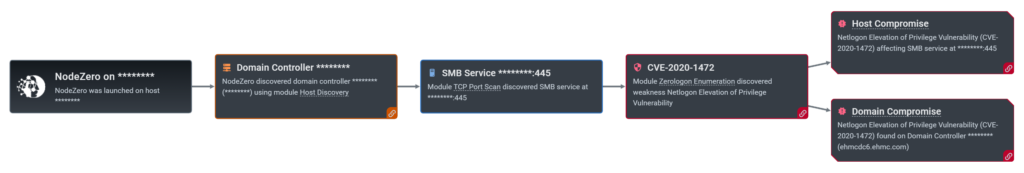
A teaching hospital had a diligent IT team. They tracked security updates to their systems, promptly patched for critical issues using industry-leading tools, and verified the patches using Microsoft DISM. When NodeZero exploited a critical but year-old vulnerability in under one day on several of their Active Directory domain controllers, they insisted it was a false positive. The ZeroLogon vulnerability had been patched months earlier. They even had evidence; reports from Qualys and Microsoft DISM showed all systems had been successfully patched.
NodeZero proves ZeroLogon was NOT patched despite Microsoft & Qualys Reports
NodeZero also had evidence; a detailed attack chain showing each step taken to get credentials, escalate privileges, and gain administrative rights to Active Directory. The hospital reapplied the patch to those servers and repeated the NodeZero autonomous pen test.
The result: Four servers remained vulnerable. A misconfiguration in their endpoint security solution had blocked patches on the domain controllers for the past 18 months! The failures were not propagated back to the patch management system, resulting in their vulnerability management and monitoring tools to incorrectly report a successful patch install.