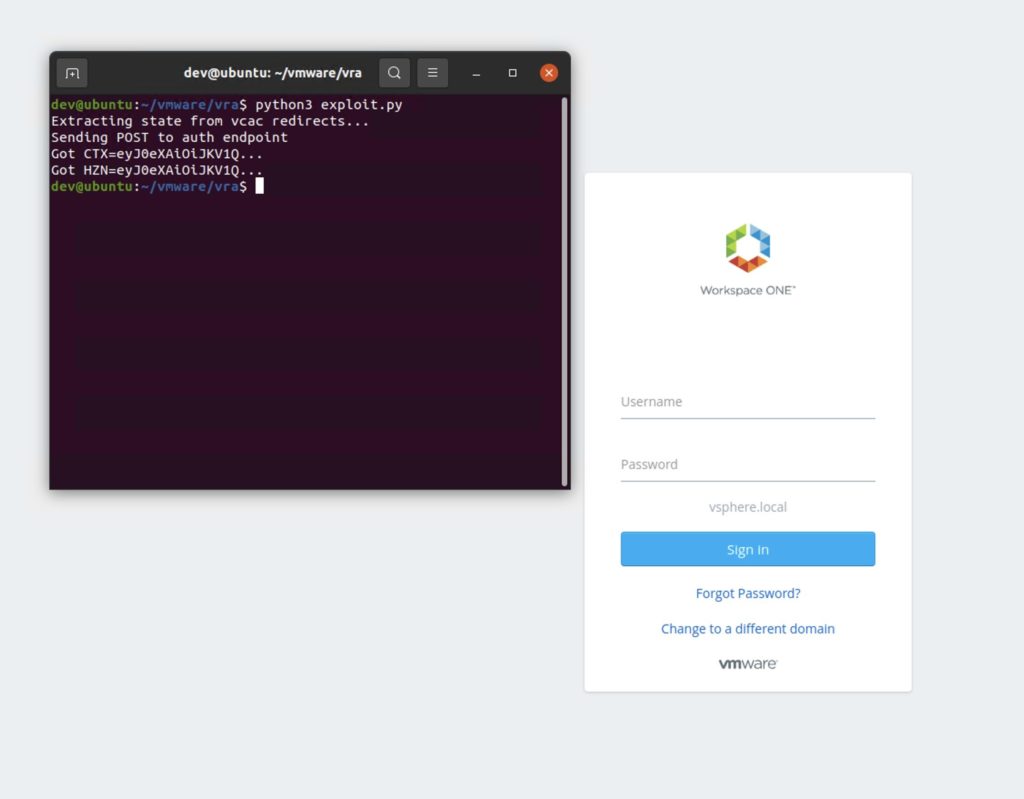
Let’s kick this week’s roundup off with a bang: the Horizon3.ai Attack Team released their VMware Authentication Vulnerability (CVE-2022-22972) Technical Deep Dive. The deep dive explores the team’s findings following a recent patch from VMware addressing a critical authentication bypass vulnerability in the VMware Workspace ONE Access, Identity Manager, and vRealize Automation products. The vulnerability allows an attacker to log in as any known local user. Take a look at what the attack team uncovered in their extensive, educational article.
The vulnerability made news across the industry, including Bleeping Computer, TheStack, and IT Nerd.
“Given that it took us about a week to develop a PoC, we fully expect motivated attackers to have already developed a PoC and began exploiting it,” Zach Hanley, Chief Attack Engineer with Horizon3.ai, told IT Nerd.
IT Nerd wrote: “The fact that this was reproduced by Horizon3.ai is good for Horizon3.ai, but bad for anyone using the affected products as that means the treat actors can do the same.”
On the Airwaves – the Healthcare Landscape
Meanwhile, CEO and co-founder Snehal Antani was a guest on this week’s AST Cybersecurity podcast, exploring how “Healthcare Faces an Aggressive Threat Landscape – How to Remediate It with NodeZero.”
Check out the podcast here for an informative dive into the threat landscape healthcare organizations face right now.
Plus, Antani joined the Cyberheroes Adventure Show for a Micro Briefing to discuss how autonomous pentesting is on the rise, recognizing the potential to apply machine learning and AI to conduct offensive cyber operations.
Meanwhile, Antani weighed in on surviving a period of financial crisis through innovation on LinkedIn.
Horizon3.ai in the News
Brad Hong, Customer Success Lead, spoke with Lifewire about the recent news that an unpatched PayPal vulnerability enables clickjacking attacks.
“The PayPal clickjack vulnerability is unique in that typically hijacking a click is step one to a means of launching some other attack,” Hong said. “But in this instance, with a single click, [the attack helps] authorize a custom payment amount set by the attacker.
In other news, Horizon3.ai announced that Chris Hill has been named as Federal and Public Sector head. You can learn more about Hill and his role with Horizon3.ai on GovConWire. Hill will be responsible for implementing the organization’s strategy to help government customers manage their cybersecurity posture with the use of Horizon3.ai’s NodeZero platform.
Quick Hits
Check out the latest review of NodeZero on Gartner Peer Insights.
The Chicago Journal reports that a breach exposed the data of a half-million Chicago students and staff.
CISA adds 20 known exploited vulnerabilities to its catalog.
Google says that spyware let government hackers break into Chrome and Android, writes Gizmodo.
ArsTechnica writes about why it’s hard to sanction Russian ransomware groups.
AT&T is set to modernize the Army National Guard’s enterprise network.




