Ransomware Impact
Ransomware is an increasingly common and lucrative attack.
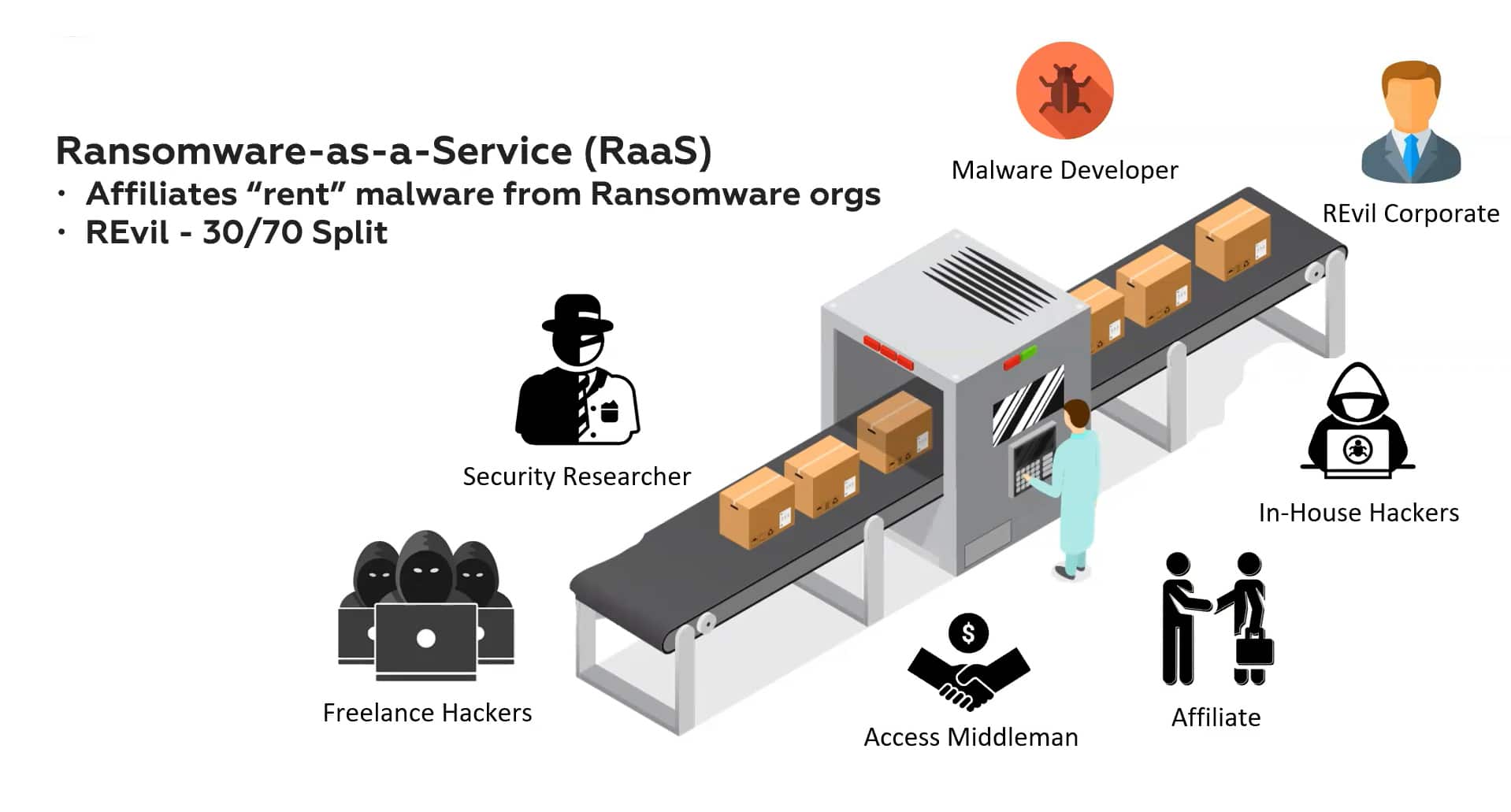
Ransomware attacks have become democratized, with criminal groups establishing Ransomware-as-a-Service (RaaS) operations, renting ransomware to recruited affiliates that, in turn, run attacks against organizations and pay a “royalty” to the RaaS providers.
Active Directory Enumeration
SMB Share Enumeration
Credential Dumping
Encryption of SMB shares
Encryption of VMWare ESXi virtual machines
Wiping/Reformatting
In a ransomware attack, like a data theft attack, criminals infiltrate a company’s network and then move laterally to identify sensitive business data. Initial access to the network often comes from compromising a legitimate credential. Instead of simply stealing a copy of the data, however, they encrypt it and demand payment in cryptocurrency before providing a decryption key. Starting with a compromised credential, the ransomware conducts:
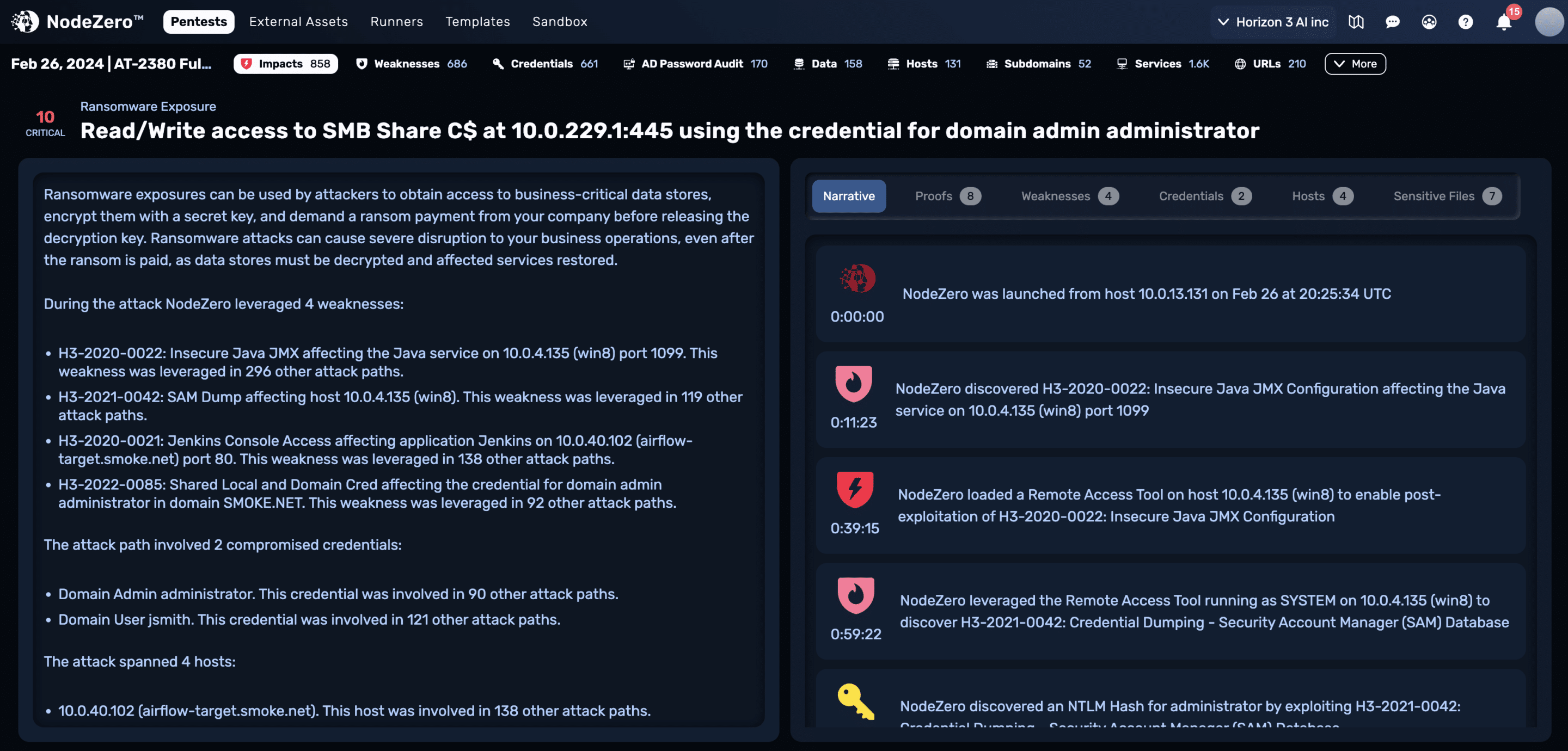
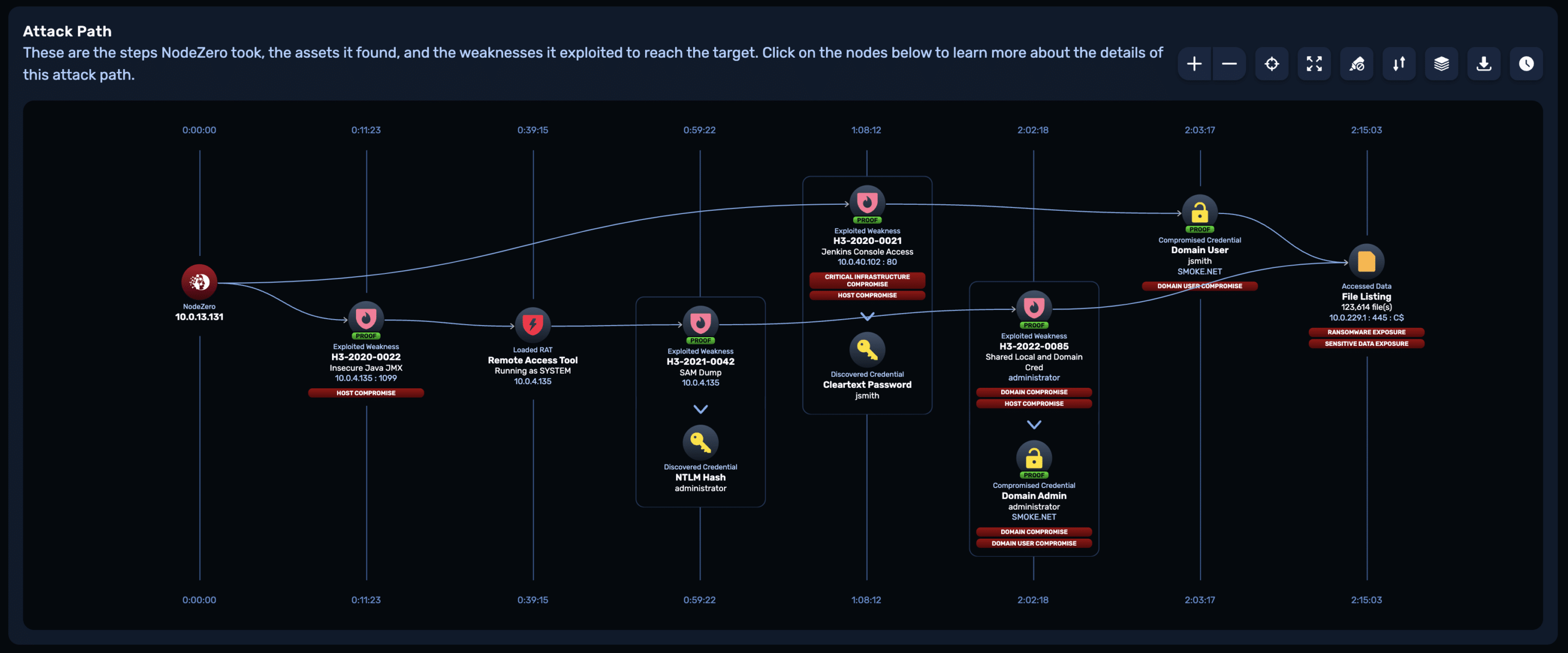
How do you assess Ransomware risk?
NodeZero can help.
NodeZero helps organizations understand the impact ransomware could have on their environments by utilizing the same tactics and techniques used by skilled attackers. NodeZero identifies attack vectors, verifies the effectiveness of each, provides a “proof” to verify each weakness (or chain of weaknesses), enumerates all data and hosts it could compromise, and provides remediation guidance to eliminate the threat. Since it is an Autonomous Penetration Testing as a Service offering, pentests can start in minutes, not hours or days.
The ransomware threat landscape has changed: here’s how defenders must adapt.
In the face of the current ransomware threat landscape, cybersecurity teams are left feeling like they’re constantly setting up roadblocks in the dark, while their adversaries have night vision and the ability to circumvent nearly any obstacle. It’s time to shift that balance. Check out our article with Cybersecurity Dive.
What can NodeZero tell you?
Run NodeZero and inject it with a “compromised” domain user credential.
NodeZero will then use this domain user credential to:
Discover hosts on the network.
Figure out which machines the domain user has administrative access to.
Find all data stores that the domain user has read/write access to.
Including SMB shares