The NodeZero® Platform
Autonomously find, fix, and validate real risks.
NodeZero transforms how organizations secure their environments by running unlimited pentests that uncover exploitable paths, guide remediation, and immediately verify that your fixes are effective. No agents. No waiting.
Continuous, self-directed security.
Attackers don’t hack in, they log in
Continually verify the effectiveness of your credential policies with NodeZero’s AD Password Audit.
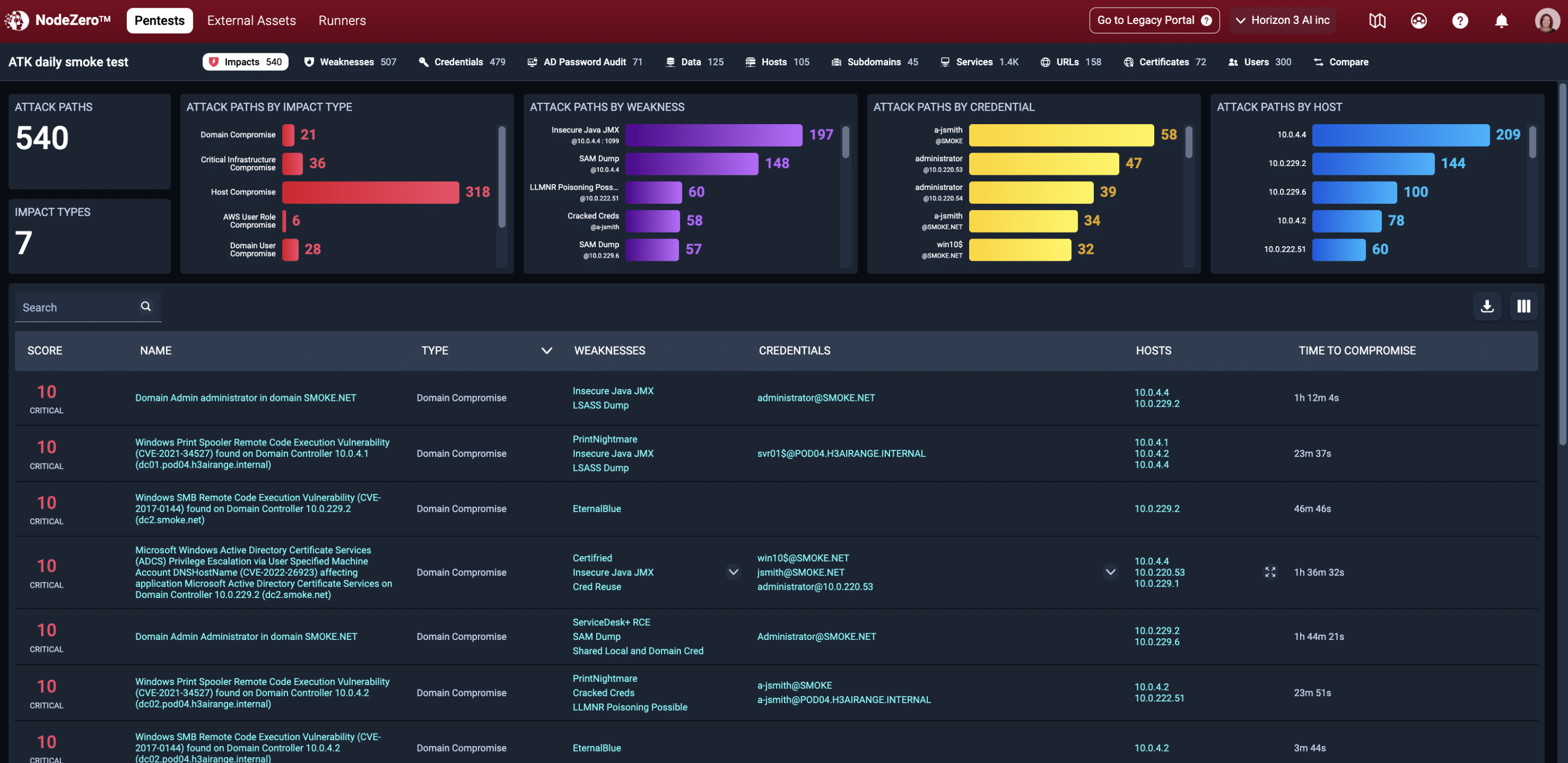
Find your most critical risks, fix what matters most
Uncover blind spots in your security posture that go beyond known and patchable vulnerabilities, such as easily compromised credentials, exposed data, misconfigurations, poor security controls, and weak policies.
NodeZero pivots through your network, chaining together weaknesses just as an attacker would and then safely exploits them. You have full visibility into your pentest’s progress and the exploits being executed in a real-time view.
When the test is complete, the results are prioritized for your immediate action. The dashboard reveals your critical weaknesses, their impact to your organization, and provides detailed remediation guidance for addressing them at a systemic level as well as individually.
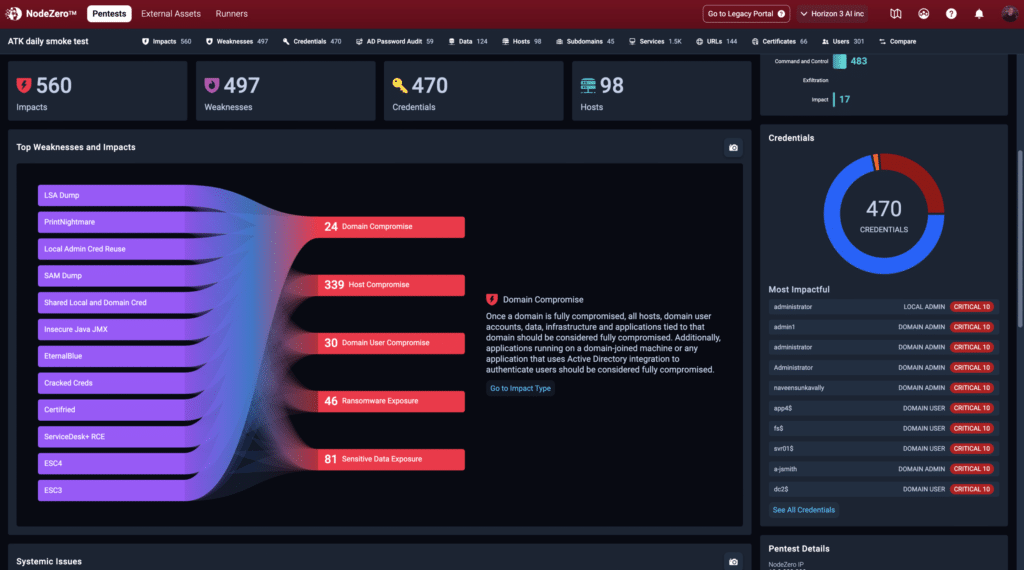
Understand the path, proof, and impact
You have clear visibility into proven attack paths, step-by-step summaries of each path, and a clear understanding of their impact on your organization.
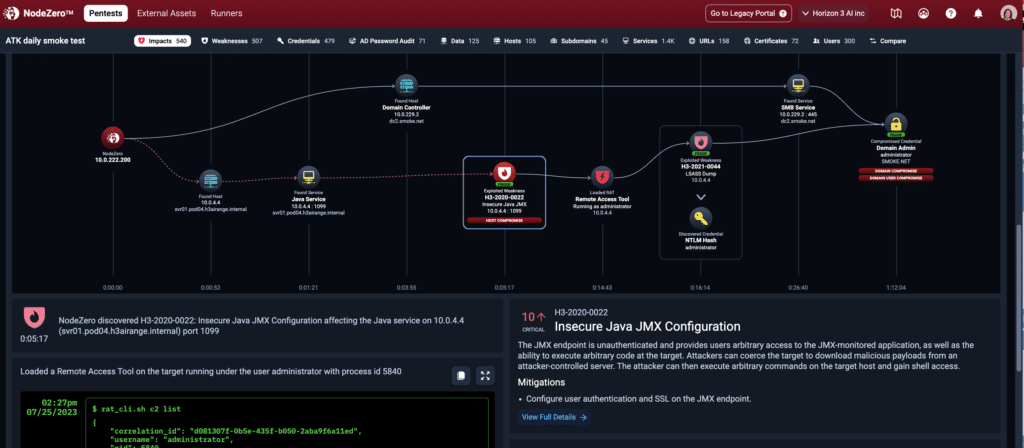
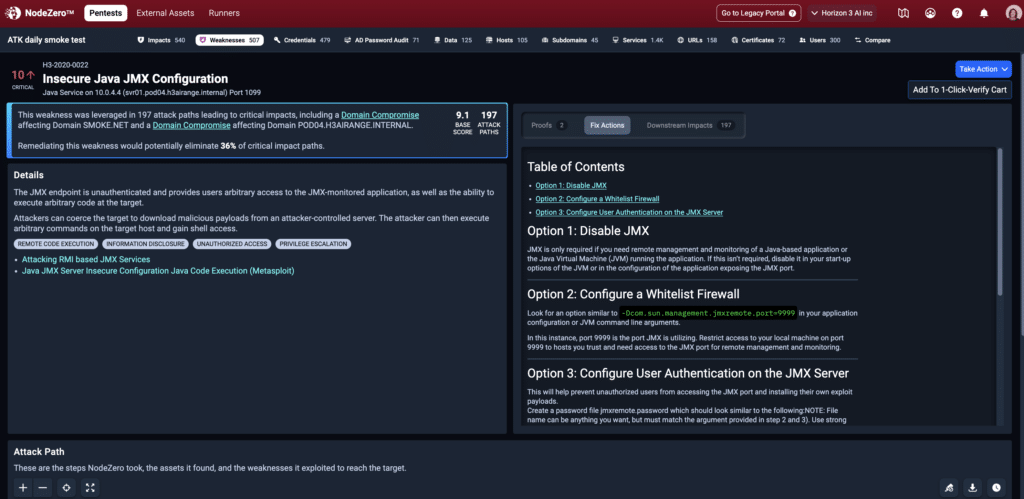
Use detailed fix guidance, then quickly verify that your fixes worked
Your team will save time using the detailed remediation guidance for every weakness identified and a complete Fix Action report for your reference. The platform highlights systemic issues where making one change may fix numerous issues at the same time. In the image here, the guidance suggests that just fixing the insecure JAVA JMX configuration could eliminate 36% of the identified critical paths.
Once you have completed your remediations, it’s easy for you to do a Quick Verify to ensure that your fixes are effective.
Uplevel your team’s skills
NodeZero improves the capacity of your security and IT team members, regardless of their level of expertise, and helps you measure your improvements over time.
Begin by addressing your most critical impacts at a systemic level for best efficiency and implement a continuous find, fix, verify loop to proactively defend your organization.
You can set up and start your first NodeZero pentest in minutes
Then you can schedule pentests to run every day thereafter for continuous risk assessment.
How NodeZero Works

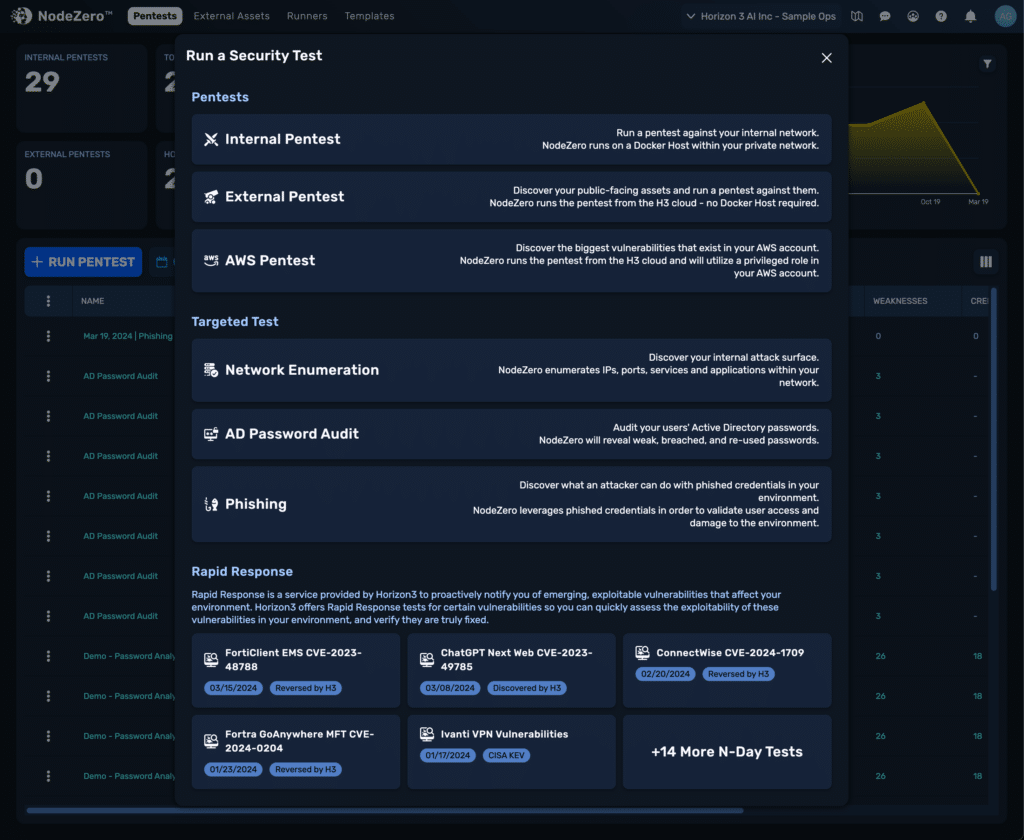
Get Started in Minutes
For continuous verification of your security posture: create an account. Choose from a variety of operations: internal autonomous pentesting, password audits, and more. Test safely from any network with or without credentials.
Quickly Set Up a Host
Internal tests are run from a free Docker host or open virtualization appliance (OVA) that you can set up in minutes; simply copy and paste the execution script into it. External tests are automated from the Horizon3.ai cloud. Schedule tests to run without setup.
Launch Your Test
Use defaults designed for safe execution, customize with Open-source Intelligence (OSINT), choose exploitation types, and more. Horizon3.ai sets up dedicated, ephemeral resources —a one-time-use architecture — for your test in an isolated virtual private cloud network.
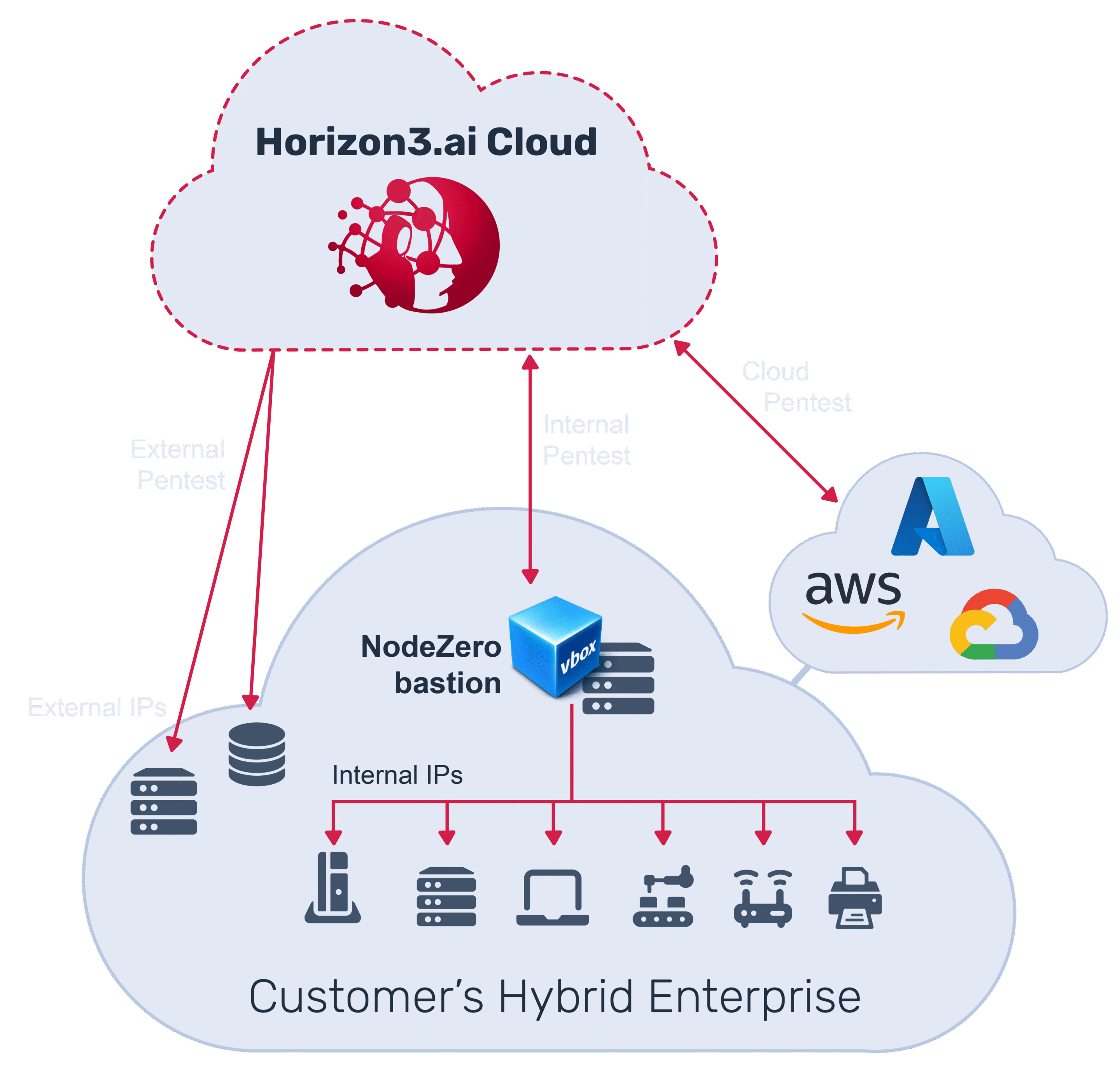
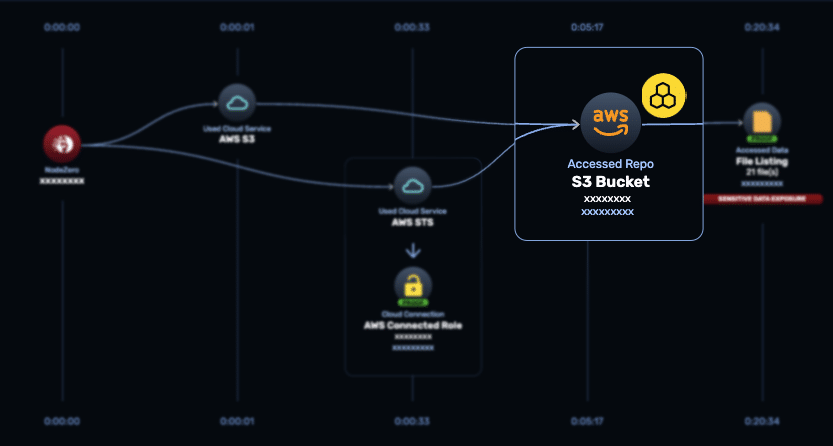
NodeZero Executes Autonomously
NodeZero navigates through your network without scripts. It exploits weaknesses based on its discoveries just as attackers do, chaining weaknesses to demonstrate impacts far beyond CVEs. Use RealTime View to monitor the state of your test and its significant findings.
Understand the Impact
Prioritized impacts show you what to fix first and how to do it most efficiently. See diagrammed attack paths, clear proof of successful exploitation, streamlined fix verification, and detailed reporting so that demonstrates your progress with your C-suite and auditors.