Overview
On 8 March 2023, PaperCut released new versions for their enterprise print management software, which included patches for two vulnerabilities: CVE-2023-27350 and CVE-2023-27351. The PaperCut security advisory details CVE-2023-27350 as a vulnerability that may allow an attacker to achieve remote code execution to compromise the PaperCut application server. PaperCut also details in this advisory that they became aware of it from Zero Day Initiative (ZDI). The ZDI case, ZDI-CAN-18987, details the vulnerability as an authentication bypass which leads to code execution.
On 19 April 2023, PaperCut became aware of in-the-wild exploitation of the product and published additional details including several indicators of compromise such as log file entries, known malicious domains, and YARA rules to detect observed malicious activity.
Subsequent research by Huntress also detailing this vulnerability was released on 21 April 2023 – including exploitation details and additional indicators of compromise.
In this post we’ll walk through the methodology of discovering the vulnerability given the security advisory, look at the root cause, analyze the patch, and develop an exploit proof-of-concept.
Locating the Vulnerability
Inspecting the ZDI case reveals valuable information within the Vulnerability Details:
The specific flaw exists within the SetupCompleted class. The issue results from improper access control. An attacker can leverage this vulnerability to bypass authentication and execute arbitrary code in the context of SYSTEM.
We find that the JAR that contains this SetupCompleted class is within C:\Program Files\PaperCut NG\server\lib\pcng-server-web-19.2.7.jar.
Decompiling a JAR can be done several ways, in this case we use CFR. CFR is a useful utility that can decompile Java via the command line to human-readable code that can be used as input for diff’ing tools.
java -jar cfr-0.152.jar v19.2.7/web-jar/pcng-server-web-19.2.7.jar --outputdir v19.2.7/web-jar/decompiled/
Looking at the decompiled class ./biz/papercut/pcng/web/setup/SetupCompleted.java, we see that upon submitting the form it calls performLogin() for the Admin user on line 48.
The performLogin() function can be found at ./biz/papercut/pcng/web/pages/Home.java.
This function is normally called throughout the software only after a user has had their password validated through a login flow. However, here in the SetupCompleted flow, the logic accidentally validates the session of the anonymous user. This type of web application vulnerability is called Session Puzzling.
Comparing the vulnerable SetupCompleted class from v19.2.7 to the patched version in v21.2.11 with Meld, we see that if setup has already been completed, visiting this page will now redirect to the “Home” page – eliminating the session puzzling logic flaw.
Confirming the authentication bypass in the GUI, we browse to the page at http://10.0.40.56:9191/app?service=page/SetupComplete and click “Login”.
Developing the Exploit
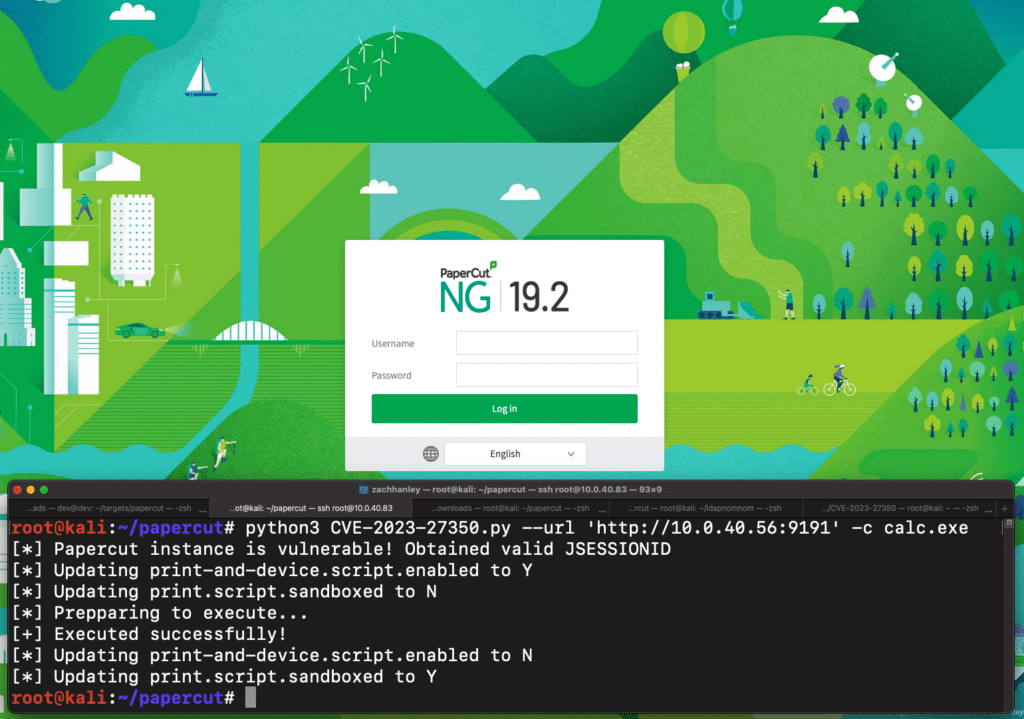
Huntress`s blog details a method to obtain remote code execution by abusing the built-in “Scripting” functionality for printers. Inspecting the Device Scripting page, we see that it enables the administrator to develop hooks to customize printing across the enterprise.
The scripts are written in JavaScript and execute in the context of the PrintCut service – which runs as NT AUTHORITY\SYSTEM on Windows deployments.
Developing a script to interact with the site normally would be pretty straight forward, but the PaperCut web application uses dynamic form fields based on the last request – so it makes it slightly less straightforward.
To develop the exploit proof-of-concept, you’ll have to use sessions and individually request each page as you would through the user interface to ensure the form fields are populated properly.
Our full proof-of-concept exploit can be found on our GitHub.
Indicators of Compromise
PaperCut has been compiling indicators as observed from exploitation in-the-wild in their advisory and will be the best source of all indicators to be on the look out for. This section lists indicators that are observed when exploiting this vulnerability using our proof-of-concept.
Navigating to the native application logs in the Logs -> Application Log tab, several indicators can be observed. While most of the indicators will appear in normal use, special attention should be given to unfamiliar source IP addresses, times, and all of these events happening in quick succession.
Authentication Bypass Indicator:
User "admin" logged into the administration interface.
Settings Change Indicator (Precursor to RCE):
User "admin" updated the config key "<A>" to "<B>".
Specifically print.script.sandboxed and print-and-device.script.enabled.
Remote Code Execution Indicator:
Admin user "admin" modified the print script on printer "<printer>".
Internet Exposure
Querying Shodan for http.html:"papercut" http.html:"print" shows approximately 1700 internet exposed PaperCut servers.
The PaperCut application is popular with the State, Local, and Education (SLED) type organizations, where just education makes up 450 of those results.