Blogs
SEARCH
CATEGORIES
TAGS
What is ITDR and Why Active Directory (AD) Tripwires Make It Real
Annual pentesting leaves blind spots. Learn why modern threats demand frequent or continuous pentesting to stay ahead of attackers.
How Often Should You Pentest?
Annual pentesting leaves blind spots. Learn why modern threats demand frequent or continuous pentesting to stay ahead of attackers.
From Patch Tuesday to Pentest Wednesday®: Proof That Reshaped Security for a Gaming Operator
September 17, 2025
A U.S. casino's first pentest uncovers 756 weaknesses & 143 attack paths, sparking a new, proof-driven approach to security.
Threat Actor Intelligence: Known Threats, Known Weaknesses, Known Outcomes
September 12, 2025
Awareness doesn’t equal defense. Threat Actor Intelligence helps you go beyond the headline: “Are these attackers using techniques that would actually work in our environment?”
From Patch Tuesday to Pentest Wednesday®: Proof That Redefined Security for a Large Insurer
September 10, 2025
The simple truth is that supply chain security depends on validation, not paperwork. Pentest Wednesday is about moving from forms and annual tests to continuous testing and measurable risk reduction, replacing paperwork with proof.
Endpoint Security Effectiveness: From Assumption to Proof
EDR and XDR platforms are positioned as the backbone of endpoint protection. They promise to detect, block, and contain threats before attackers can gain a foothold. Yet many organizations are left asking the same questions: Where is our EDR deployed? Is it configured properly? Could something be slipping through? The uncomfortable truth is that most…
From Patch Tuesday to Pentest Wednesday®: Proof That Redefined Security for the Defense Industrial Base
September 3, 2025
The simple truth is that supply chain security depends on validation, not paperwork. Pentest Wednesday is about moving from forms and annual tests to continuous testing and measurable risk reduction, replacing paperwork with proof.
From Patch Tuesday to Pentest Wednesday®: Proof That Redefined Security for a Manufacturer
August 27, 2025
Patch Tuesday is a known event, but attackers are moving faster than ever. For a leading U.S. manufacturer, shifting from simple patching to continuous validation became the key to proving their fixes worked, turning uncertainty into confidence.
From Patch Tuesday to Pentest Wednesday®: Proof That Protects Healthcare
August 20, 2025
A Pentest Wednesday® Story Every security leader knows about Patch Tuesday. It’s the rhythm Microsoft set decades ago to deliver updates and fixes, and it quickly became a mainstay of IT and security operations. Teams plan change-windows around it. Vendors align updates to it. And for many organizations, Patch Tuesday has become the de facto…
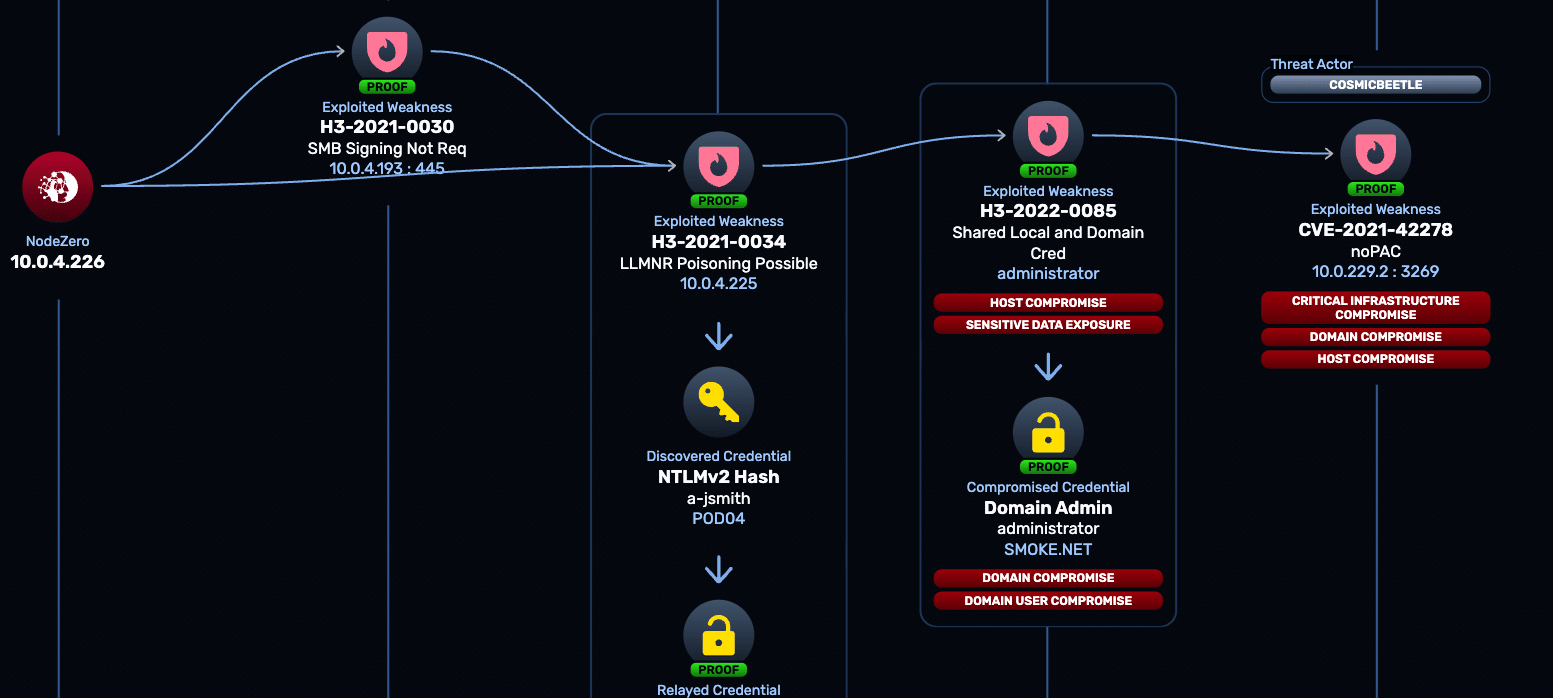
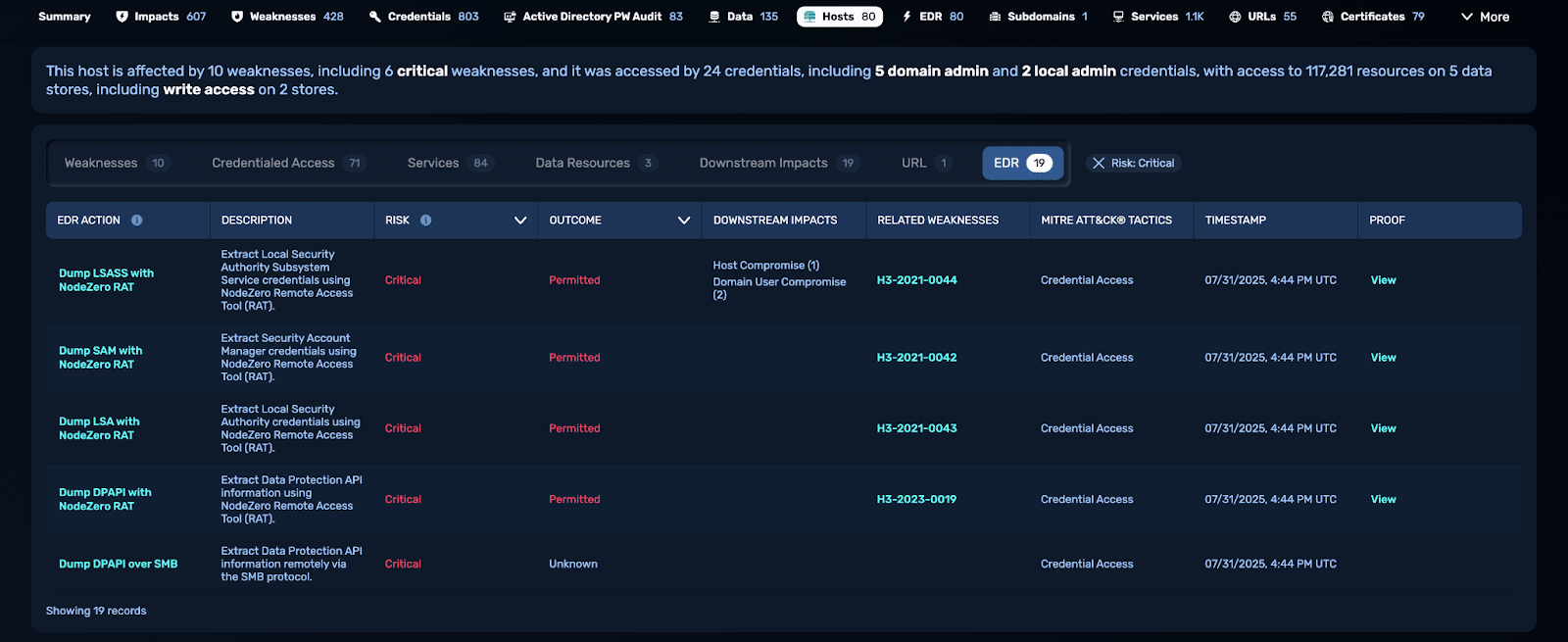
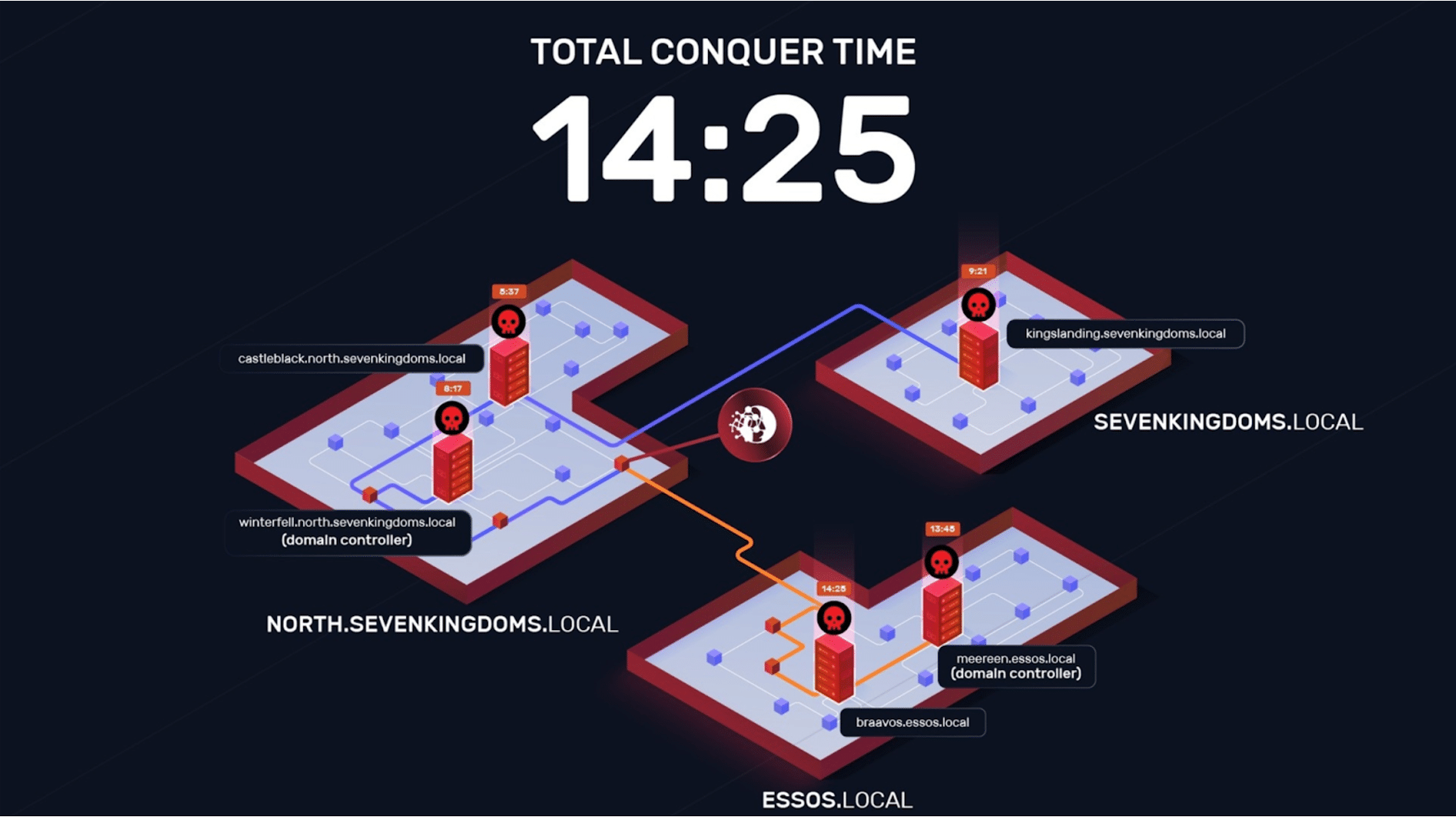
NodeZero® vs. GOAD: Technical Deep Dive
NodeZero autonomously compromised GOAD in 14 mins by exploiting common Active Directory misconfigurations.