With the advent of NodeZero, Horizon3.ai customers can (and have) run multiple penetration tests (pentests) in a year to find, fix, and verify what is reachable, vulnerable, and exploitable in their environment, an accomplishment previously reserved only for the most well-funded companies and organizations. Throughout the year, Horizon3.ai customers ran nearly 7,000 pentests with NodeZero. In fact, many of our customers have eschewed the previous model of infrequent or annual pentests altogether to constantly verify their security posture by running multiple pentests in a single month. Some of our most prolific users run over 40 pentests a month with NodeZero, which is well above the often-cited recommendation of one to two pentests a year.
Within the NodeZero portal, Horizon3.ai customers view a graphical representation of actual attack paths that an attacker could use to chain together misconfigurations, vulnerabilities, and weaknesses to compromise their organization. NodeZero further provides the customer with the insight necessary to mitigate risk by prioritizing exploitable weaknesses with their corresponding fix actions and then enables customers to verify each weakness has been remediated.
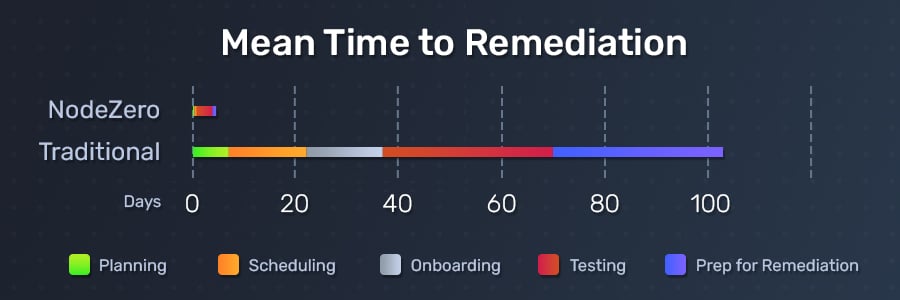
Prior to using NodeZero, our customers hired outside consultants to run pentests on an infrequent or annual basis. Not only was this a costly and unscalable proposition for our customers, it left many of them accepting a large amount of risk. Many of our customers also report that the consultants that they hired often left them with quickly outdated, noisy reports about their security posture, with inaccurate and unactionable information about how to prioritize fixing their organization’s vulnerabilities. To make matters worse, these hardworking cybersecurity professionals would receive blame for any deficiencies that the report generated.
Historically, companies used traditional pentesting for one of three reasons –
To do so, companies would spend large sums of money to contract out highly skilled and in-demand pentesters to conduct pentests. This also had the adverse effect of leaving smaller or lesser funded companies unable to schedule or afford those same pentesters, because there are simply not enough pentesters in the cybersecurity industry.

To solve this issue, new thinking emerged. Companies began organizing and crowdsourcing that small community of pentesters to execute bug bounties, poke at web applications, and identify and attack their public-facing assets. The next iteration then came in the form of automation, as savvy attackers were enabled by the creation of runbooks or scripts to synchronize an attack across multiple assets. While the value of these efforts can be high, the pain points across each of these methods have plagued the cybersecurity industry for years – from the high cost to contract or maintain, to limited scope, speed, and accuracy.
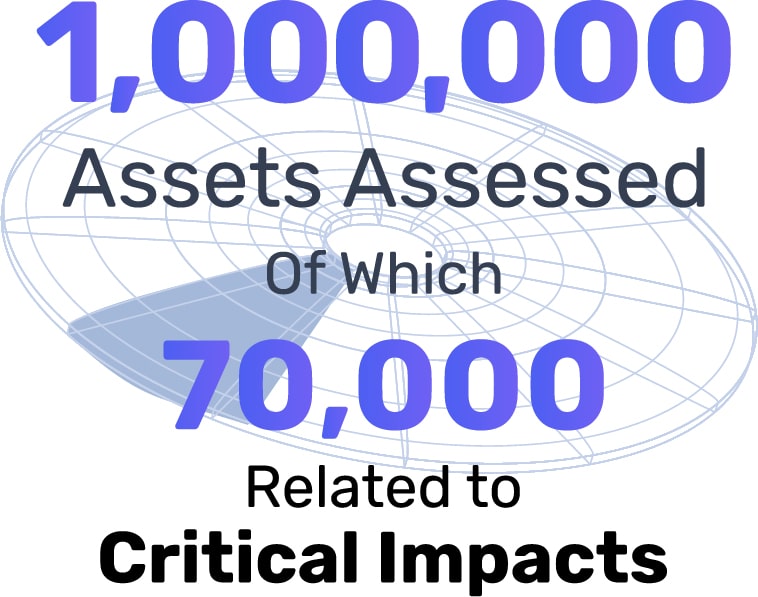
Of the nearly 7,000 pentests run in the last year, NodeZero has tested almost 1 million assets, with a staggering 7% of those assets contributing to or directly affected by a critical impact – an event that would cause program failure and an inability to achieve the customers’ minimum acceptable requirements – with over 200,000 different attack paths or ways an attacker can take to exploit a weakness in a system to impact. These are results from companies that deploy industry-leading security tools, employ experienced cybersecurity practitioners, and implement compliance policies.
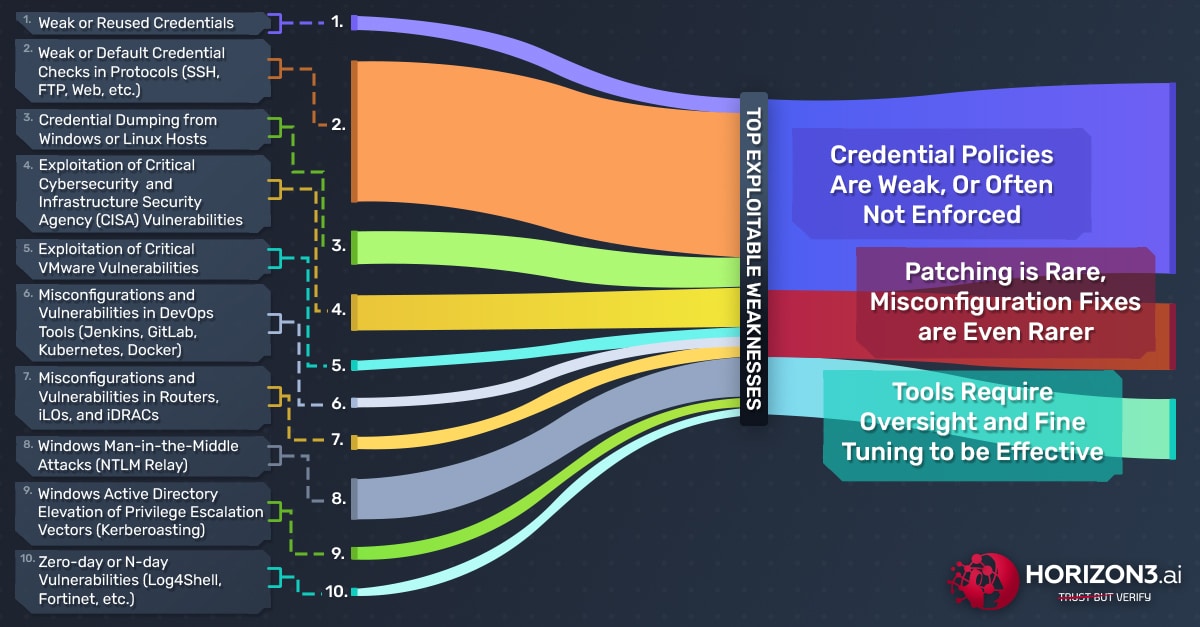
From the last year, we learned that teams, tools, and policies all require tuning and enforcement. Further, the data from the last year also confirms what we have always known – to truly understand if our security posture is effective, we must continually attack our environment in the same way a malicious cyber threat actor would. Our customers have done exactly that. They continuously and thoroughly tested their respective environments with NodeZero, learned where they were weak, and addressed the results to improve their security posture. Based on their attacker’s perspective, we have seen three main themes arise over the past year:
- Credential policies are weak, or often not enforced;
- Patching is rare, but misconfiguration fixes are even rarer;
- Tools require oversight and tuning to be effective.
The good news is, we’ve seen each of these themes remediated when a practitioner and/or leader sees the results and impacts of a potential attack. When security vulnerabilities are exposed and prioritized based on pentest results, the impacts of weak credentials, misconfigured domains, and unpatched vulnerabilities are made relevant and visceral. Those practitioners and leaders have patched and rerun a pentest to verify they remediated that remote code execution (RCE) vulnerability. They’ve implemented new password policies and pushed Local Administrator Password Solutions so users, especially those with elevated privileges, aren’t reusing the same credentials. They’ve tuned their endpoint detection and response (EDR) tools to actually stop techniques like credential dumping.
In this report, we focus on these three themes and show you how the top weaknesses NodeZero found and exploited over the past year led to critical impacts, deeper implications, and ultimately positive action by the customer to remediate vulnerabilities and weaknesses.
The Top 10 vulnerabilities and weaknesses that NodeZero enumerated and exploited over the last year are:
- Weak or reused credentials
- Weak or default credential checks in protocols (SSH, FTP, Web, etc.)
- Credential dumping from Windows or Linux hosts
- Exploitation of Critical Cybersecurity & Infrastructure Security Agency (CISA) vulnerabilities
- Exploitation of Critical VMware vulnerabilities
- Misconfigurations and vulnerabilities in DevOps tools (Jenkins, GitLab, Kubernetes, Docker)
- Misconfigurations and vulnerabilities in Routers, iLOs, and iDRACs
- Windows Man-in-the-Middle attacks (NTLM Relay)
- Windows Active Directory Elevation of Privilege Escalation Vectors (Kerberoasting)
- Zero-day or N-day vulnerabilities (Log4Shell, etc.)