The Challenge: Healthcare Faces an Aggressive Threat Landscape.
One of our clients, a leading U.S. hospital and healthcare system, consistently earns high marks for clinical excellence and is among the top 10 percent in the nation for patient safety. Recognizing the growing cybersecurity threats to healthcare organizations and importance of importance of maintaining compliance with regulatory standards like HIPAA, PCI, and other privacy rules, the organization’s IT staff worked hard to ensure a strong security posture.
Our client’s IT team had adopted many security best practices and tools, including state-of-the-art firewalls, vulnerability scanning, endpoint detection and response (EDR), automated patch management, network segmentation, and a managed security service provider (MSSP). In addition, the team began implementing a zero-trust architecture and has tools to monitor the many specialized medical devices on its hospital networks.
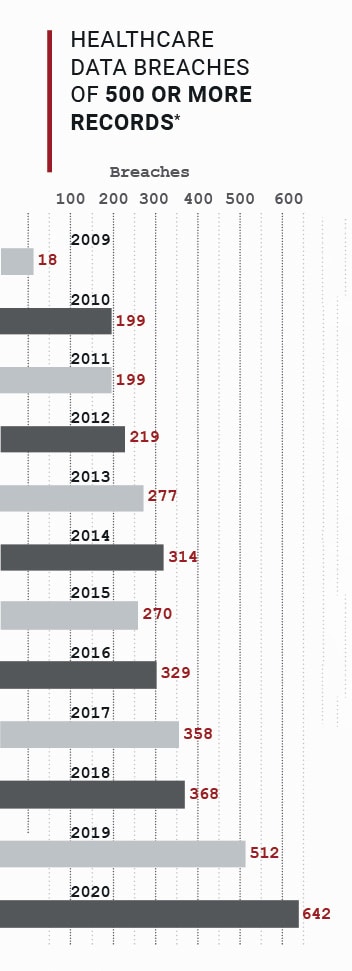
Even with these comprehensive security practices in place, the team wanted to do more. Hackers have increasingly targeted the healthcare industry. In 2020, over 600 data breaches of 500 or more patient records were reported. Ransomware attacks continue to be extensively used against healthcare organizations, and these attacks are becoming more costly.
The Solution: NodeZero™ Automated Red Teaming
Liberman Networks, a managed security and IT services company, recognized that even with their many controls implemented, our client could still be vulnerable to an attack.
Liberman Networks called on Horizon3.ai to help validate our client’s defenses and provide proof of what was truly effective and which deficiencies remained.
Our client used Horizon3.ai’s NodeZero – a fully autonomous SaaS offering that views the network from the attacker’s perspective – to conduct a comprehensive penetration test across its enterprise. In a matter of minutes and with virtually no configuration, NodeZero began its reconnaissance, mapping the organization’s infrastructure and over 8,400 hosts, probing for misconfigurations, open ports, and other vulnerabilities an attacker could exploit, whether alone or by chaining multiple weaknesses.
The Findings: Unauthenticated Access to Domain Controller’s
NodeZero ran for eight days with no adverse impact to the network.
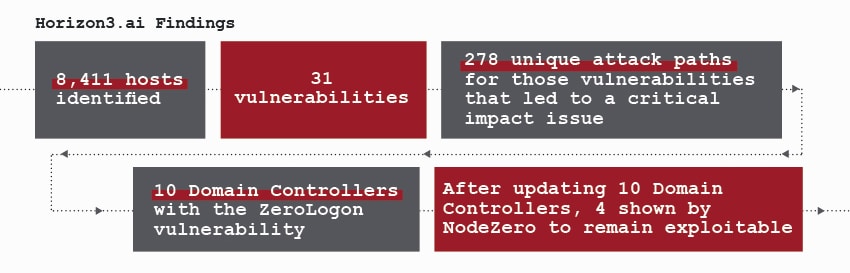
NodeZero identified 31 vulnerabilities with 278 unique attack paths, proofs for each, and remediation guidance.
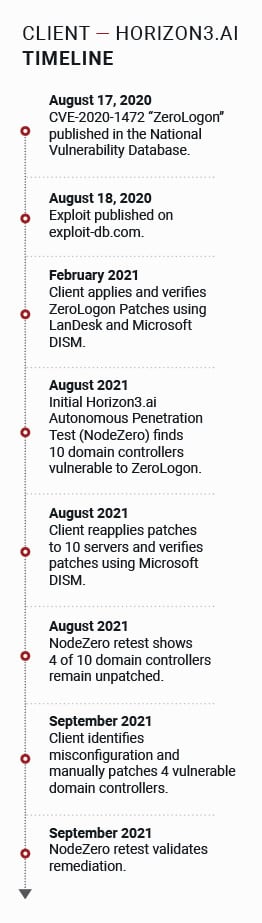
The most significant and surprising finding was immediately communicated to our client by Liberman Networks – even before NodeZero completed its testing. Ten Microsoft Active Directory domain controllers included ZeroLogon – a “critical” and potentially catastrophic privilege escalation vulnerability allowing unauthenticated accesses to devices first disclosed a year prior to the NodeZero test. Worse, an exploit was publicly available, making the vulnerability an easy target. Had attackers targeted the vulnerable hosts they could have quickly created their own credentials and gained unfettered access to every system in the organization. The result could include stealing patient information and financial data or installing ransomware on our client’s endpoints and databases.
“We patched this back in February. All of our reporting shows it as patched.” — Director of Infrastructure
Lesson 1: Reporting Tools Can Lie.
At first, our client believed NodeZero was in error. They were diligent in their patching and their records showed a successful update for the ZeroLogon vulnerability months earlier. Our client also had evidence; reporting from Qualys and Microsoft Deployment Image Servicing and Management (DISM) showed all systems were patched, and they trusted their tools.
In this case trusting the tools was a mistake. Liberman Networks and Horizon3.ai’s customer success team investigated further and confirmed that the updates had been unsuccessful. When our client reapplied patches to the 10 servers, a subsequent test by Liberman Networks and Horizon3.ai showed that 4 of the 10 devices remained vulnerable – despite showing as patched – again – in Microsoft.
A security solution blocked security updates for 18 months.
After further analysis, our client found the problem; a misconfiguration in their EDR solution had blocked patches on the domain controllers for the past 18 months! The failures were not propagated back to the patch management system, resulting in their vulnerability management and monitoring tools to incorrectly report a successful patch install. After manually pushing patches to each domain controller NodeZero was quickly re-run, proving that the problem had truly
been remediated.
“This is a good experience for me to teach the team the importance of credential use and reuse. We never would have found this vulnerability without NodeZero.” — Director of Infrastructure
Lesson 2: Patching ≠ Remediation
The lesson our client learned was simple; patching is not the same as remediating. Our client followed standard best practices in the defenses. They tracked security updates to their systems, promptly patched for critical issues using industry-leading tools and verified the patches using Microsoft DISM. As they saw, the tools can be wrong, leaving organizations vulnerable to attacks.
With assistance from Horizon3.ai and Liberman Networks, our client’s IT staff improved their security profile and their internal in monitoring, detection, and response skills. The IT team’s increased knowledge and confidence is generating greater trust in IT by the business. By using an offensive strategy to test its defenses, the healthcare system is evolving its cybersecurity posture to match the threat landscape that it faces.
Lesson 3: Follow Patch Tuesday with Pentest Wednesday.
According to the NIST Cyber Security Framework, organizations should validate through systematic audit and assessment that they have truly fixed vulnerabilities after deploying patches. In reality, most IT teams lack the resources to do penetration testing after every patch.
After their experience with misreported patching – with proof from Liberman Networks and NodeZero – our client added a step to “Patch Tuesday”: “Pentest Wednesday” with NodeZero to validate all patches are correctly implemented and risks are mitigated.




