Table of Contents
- Option 1: Disable the IPMI Service
- Option 2: Implement a Strong Password
- Option 3: Implement a Strong Password Policy
- Option 4: Implement a Configuration Management Policy
This weakness is the result of a flaw in the protocol design. As a result, there is not a software patch or fix action that can completely remove the weakness without disabling the service (option 1). However, the weakness can be mitigated using options 2-4. These options do NOT prevent an attacker from obtaining password hashes, but can increase the complexity of offline password cracking attacks. These fix actions may reduce the likelihood of an attacker obtaining a cleartext password, but NodeZero will continue to report the weakness.
Option 1: Disable the IPMI Service
The IPMI service settings can typically be managed via the web page in the Administration section. Specifically, on the HP iLO, navigate to the Administration->Access Settings page and set the “IPMI over LAN Access” to “Disabled”. 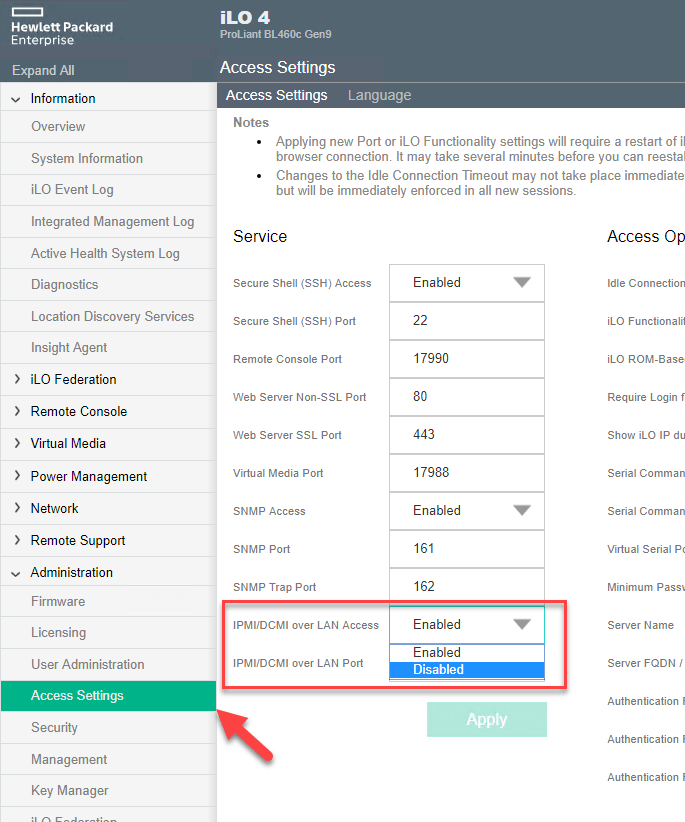
Option 2: Implement a Strong Password
If disabling the service is not an option, updating the password to be much stronger will prevent attackers from cracking the hash obtainable from this vulnerability. Change the credential’s password and consider implementing additionally security policies. Typically to update passwords on these systems, log in via the web page, access the account settings, and update the password.
Option 3: Implement a Strong Password Policy
Ensure a strong password policy is in place and users are properly trained on best practices. The National Institute of Standards and Technology (NIST) commonly releases guidance on password best practices which include:
- A minimum length of 8 characters
- Blacklisting passwords that contain dictionary words, repetitive or sequential characters, and the company name
- Implement Multi-Factor Authentication when available
- For more detail see NIST 800-63-3
Option 4: Implement a Configuration Management Policy
Often, systems and applications will be installed without the default credentials being changed. Identify a configuration management process that ensures default credentials are changed before systems are deployed in a production environment.


