- Weak or Reused Credentials
- Weak or Default Credential Checks in Protocols (SSH, FTP, Web, etc.)
- Credential Dumping from Windows and Linux Hosts
- Credential Attack Leads to Ransomware Exposure
- Implications of Credential-based Attacks
- Policy Recommendations and Mitigation Actions

Regardless of what the headlines in our newsfeeds may say, cyber threat actors do not often use sophisticated hacking tools and techniques like zero-day exploits to gain access to a network; they simply log in with legitimate user credentials. According to CrowdStrike, 62% of all detections indexed by the fourth quarter of 2021 were malware-free – meaning attackers were “living off the land,” using legitimate credentials and built-in tools to evade detection instead of sophisticated malware.
We know that nefarious actors exploit credential requirements in many ways. They can:
- Take advantage of weak password strength requirements or weak account lockout thresholds,
- Capture and then crack hashes,
- Take advantage of accounts that reuse compromised credentials,
- Use the default credentials that remain unchanged in a variety of web applications and systems processes.
Some cyber threat actors may even go so far as to buy cleartext credentials made available on the dark web. Once they gain initial access, threat actors then appear as legitimate users and can move laterally within a network to gain further access and establish persistence, steal sensitive data, bring down systems, and/or hold the organization hostage through ransomware.
Weak or Reused Credentials
Horizon3.ai customers are keenly aware of the risks that credential-based attacks pose to their organizations because NodeZero allows them to safely assess their environment against them. In the last year, NodeZero successfully executed credential-based attacks over 6,000 times (out of the 34,000 times in which NodeZero successfully executed an attack compromising at least one host), and to great effect. Take for instance when a North Carolina-based medical clinic ran an internal pentest with NodeZero (See Figure #1). The clinic found that its systems were exploitable after NodeZero conducted open-source intelligence on the company’s name, scraped potential employees from LinkedIn, then executed the password spraying technique to find a potential logon name with a common, weak, or publicly available password.
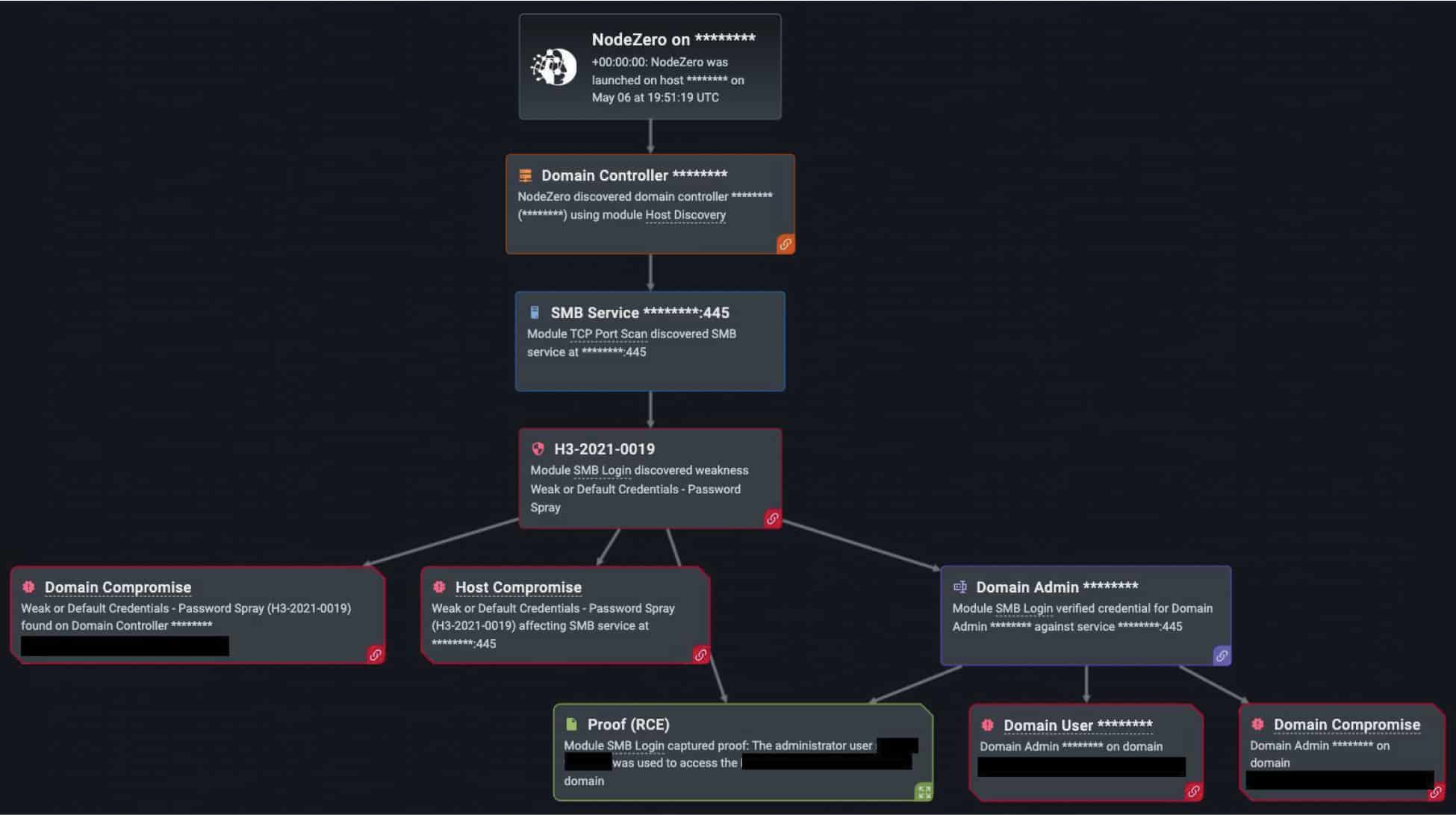
Figure #1: Horizon3.ai’s NodeZero used password spray in a pentest run by a small medical clinic and achieves domain user and domain compromise.
Threat Intelligence Reference
Attacks involving weak or reused credentials can have disastrous effects. We know this because hackers are using them in real life. Take for instance the data breach involving the New York City Law Department last year. The Department fell victim to a cyber-attack that resulted in the attackers gaining access to the personal data of thousands of city employees, evidence of police misconduct, medical records, and the identities of children charged with crimes. The Department’s attorneys were also unable to remotely access electronic files after the incident, causing further delays in legal proceedings. All of this happened because of a single employee’s stolen email account password.
Weak or Default Credential Checks in Protocols (SSH, FTP, Web, etc.)
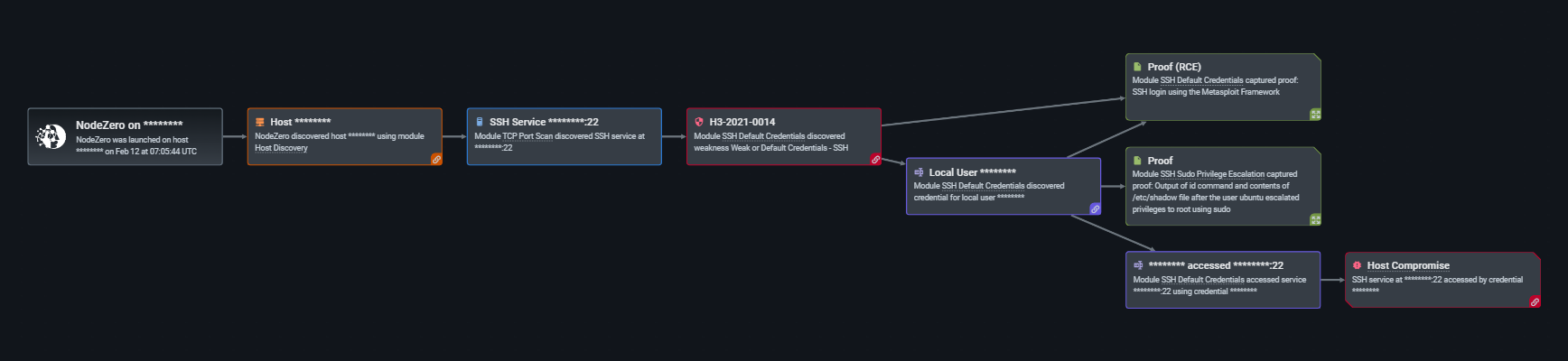
NodeZero is also adept at exploiting weak or default credentials in protocols like secure shell (SSH), file transfer protocol (FTP), web applications, and simple network management protocol (SNMP), to name a few. So much so that NodeZero took advantage of protocols over 5,000 times in the last year (out of the 34,000 times in which NodeZero successfully executed an attack compromising at least one host).

One of our customers, a New York-based IT solutions provider, ran a pentest in which NodeZero exploited weak and default credentials in SNMP, FTP and SSH with varying levels of criticality. As a result, over 20 credentials were compromised that had access to data stores that had “write” access, thereby exposing sensitive data and providing an opportunity for ransomware exposure. Further, an actual threat actor could openly maneuver throughout the environment and access information if a password were compromised and further exploited.
Threat Intelligence Reference
This is important to keep in mind because we have seen cyber threat actors exploit weak or default credential checks in protocols. Take for instance the Golang peer-to-peer botnet called FritzFrog that has been actively exploiting SSH servers since early 2020. According to researchers, FritzFrog is a worm that brute-forces credentials at entities like governmental offices, educational institutions, medical centers, financial institutions and more. Within the span of a single month, the botnet infected a total of 1500 hosts. while the botnet’s infection rate peaked at 500 incidents per day in January 2022. The botnet is able to propagate over SSH to drop a malware payload that then executes instructions received from the command and control (C2) server to then gather system information and files before exfiltrating them back to the server.
Credential Dumping from Windows and Linux Hosts
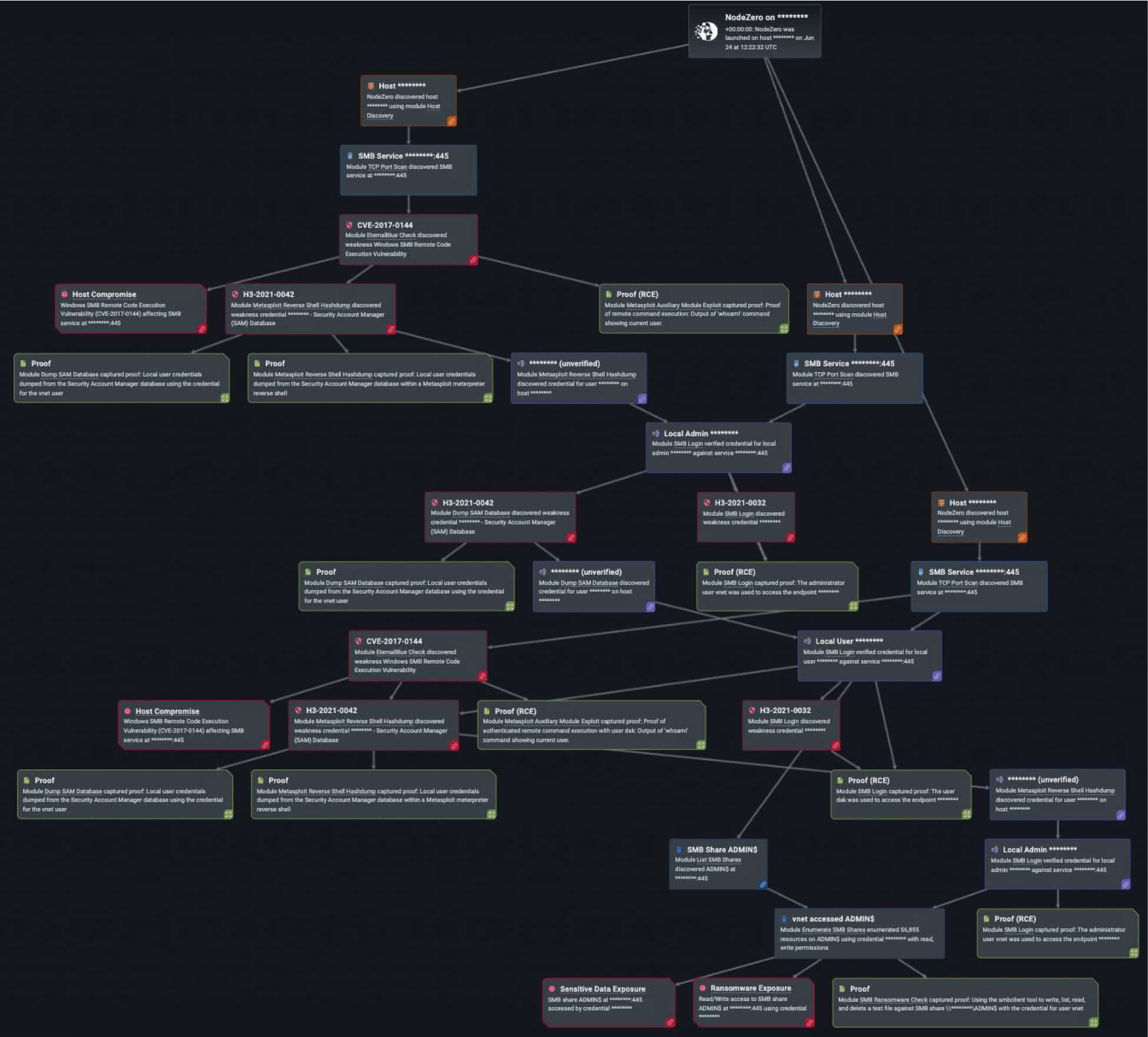
In addition to exploiting weak or default credentials, NodeZero over the past year also compromised hosts with local admin credentials, then dumped more credentials over 1,200 times (out of the 34,000 times in which NodeZero successfully executed an attack compromising at least one host). With the credential dumping technique, adversaries may attempt to dump credentials to obtain account logins, clear text passwords, and/or hashes from an operating system or software. The credentials can then be used to perform lateral movement across a system and access restricted information. Just as malicious threat actors target various Windows and Linux hosts like Kerberos, the Local Security Authority (LSA) Secrets, and the Local Security Authority Subsystem Service (LSASS) that contain the login and password information, so does NodeZero.
This is a system file in Linux that stores encrypted user passwords. It is only accessible to a root user and therefore prevents unauthorized access to cyber threat actors from breaking into a system. Attackers who can crack password hashes from this file can log in with those credentials and appear like legitimate users. This way they can also exploit password reuse to move laterally across systems. The Horizon3.ai customer was able to learn that at least four of their credentials were discovered in this pentest and elevated their risk of sensitive information disclosure from medium to high.
Threat Intelligence Reference
We also know that cyber threat actors, to include government-sponsored advanced persistent threat (APT) actors that are able to gain access to a network and remain undetected for an extended period of time, continue to use credential dumping to gain additional access. In February, CISA released a joint advisory with the FBI, US Cyber Command and the UK National Cyber Security Center warning of MuddyWater, an Iranian-backed APT group that is subordinate to the Iranian Ministry of Intelligence and Security (MOIS), that conducts cyber espionage and malicious cyber operations. Their targets include government and private-sector organizations in the telecommunications, defense, local government, and oil and natural gas industries in Asia, Europe, and North America. CISA confirms that MuddyWater targets password stores and has performed credential dumping with LaZagne and other tools, including by dumping passwords saved in a victim’s email. The group has also used various tools to dump LSASS memory, LSA Secrets, and cached domain credentials.
Credential Attack Leads to Ransomware Exposure
This pentest raises a lot of questions for us and the customer, and rightfully so. Why was NodeZero able to dump the SAM credential? Was there a misconfiguration that allowed this? And why was the EDR solution, if one is implemented, not able to stop it from occurring? Did the company’s security team receive an alert on the issue and log it? More specifically to our point about credentials, we would suggest that this customer implements better password policies and Local Area Password Solution (or LAPS) with multifactor authentication for their privileged users with local administrator rights so that they can’t reuse the same credentials on multiple machines. This would at least limit the blast radius of what a cyber threat actor could gain access to, further ensuring that a threat actor’s compromised credential access would be limited to one system.
Implications of Credential-based Attacks

NodeZero achieved a critical impact in each of these examples, including domain compromise, host compromise, sensitive data exposure, critical infrastructure compromise, or ransomware exposure. While it is important for the customer to remediate chained weaknesses leading to these impacts in their environment, it is also important to rectify the underlying systemic issues that contribute to these issues. In our conversations with our customers, and within the NodeZero portal itself, we highlight that many companies and organizations either implement poor authentication and/or credential policies and poorly enforce those policies. This also leads us to ask whether the security tools that our customers have in place are set up correctly and are effective in detecting, logging, alerting, and stopping these threats from achieving a critical impact.
Policy Recommendations and Mitigation Actions
Fortunately, there are relatively simple changes that can be made within an organization to help prevent credential-based attacks. They are:
- Increase training for employees on basic cyber security, including the dangers of credential reuse and weak or easily guessed passwords. Additionally, for your privileged admins implement a Local Administrator Password Solution (LAPS) solution to help organizations prevent local admin credential reuse.
- Institute password policies that include sophistication and length requirements as described in the latest recommendations from NIST Special Publication 800-63B to include:
- All passwords must be 12 characters or longer
- No passwords matching the list of known breached passwords
- No passwords derived from dictionary terms
- No passwords derived from well-known contextual terms such as the company name, product, etc…
- No passwords derived from well-known information about the user such as the username, first name, or last name
- All passwords should be unique, and no passwords should be “too similar” to each other
- When creating a temporary password for a new user or a user that requires an account unlock, require the password to be used within a specific timeframe before the account becomes disabled.
- Require the use of multifactor authentication for logging into external environments and segmented networks when possible. This ensures a high degree of certainty that a cyber threat actor will not be able to gain access to public facing instances unless they also have control of the second device, such as a registered cellphone or other device to confirm a login attempt.
- There are a variety of tools to set and enforce password policy. For instance, if you’re using Azure AD, you can enable Azure AD Password Protection to automatically ban well-known bad passwords. Of Note, password managers are good, but don’t store your MFA tokens in your password manager!
- Implement a configuration management process that directs default credentials are changed before systems are deployed in a production environment.
- Implement good access controls to include the principle of “least privilege”. Users should only have access to specific data, resources, and applications needed to complete required tasks within their role. This can help ensure that organizations are limiting their overall attack surface, while improving their security posture and reduce “over privileged” users that could misuse critical systems and increase liability.
- Disable the accounts of current or former employees who no longer require access. Oftentimes, cyber threat actors are disgruntled employees or former employees that would like to seek retribution against an organization and already have access. Disabling and not deleting the former user account allows the organization to retain any files or data that individuals may have generated while limiting the organization’s risk.
- And lastly, verify that each of the above guidelines are implemented, enforced, and effective by attacking your environmental teams, tools, and rules using NodeZero.