WHAT?
Attackers don’t need to hack in – they log in. This is why we believe Credentials are the new RCE.
Why do attackers choose to target credentials? Two reasons:
- With a valid credential, the attacker appears legitimate…and when they look legit, they set off fewer alerts, are harder to catch, and they can persist in your environment.
- Using an existing credential is often easier and cheaper than exploiting an N-day vulnerability or building and employing a Zero-day Remote Code Execution (RCE).
This is why Horizon3.ai focused NodeZero’s development so intensely on credentials attacks. While our digital landscape and footprints have changed – drastically over the pandemic – a tried-and-true primary attack vector has not: reusing credentials.
- The Marriott Data Breach: In 2018, Marriott International announced that the personal information of up to 500 million guests had been compromised in a data breach. The attackers reportedly used a combination of stolen employee credentials and a sophisticated phishing campaign to gain access to the company’s systems.
- The SolarWinds Supply Chain Attack: In December 2020, it was revealed that a group of Russian state-sponsored hackers had compromised the software supply chain of SolarWinds, a company that provides IT management software to many major corporations and government agencies. The attackers used stolen credentials to gain access to the systems of the organizations that use SolarWinds’ software.
- The Twitter Hack: In July 2020, a group of hackers were able to gain access to the Twitter accounts of several high-profile individuals, including Joe Biden, Bill Gates, and Elon Musk. The attackers used a combination of phishing and social engineering tactics to obtain the credentials of Twitter employees, which they then used to take control of the targeted accounts.
No matter how complicated the credential, if people reuse it and an attacker discovers it, the race is on. That credential might as well be a personal RCE vulnerability. Why?
- A Carnegie Mellon University study found that only one-third of users change their passwords following a data breach announcement.
- A recent study conducted by LastPass ,a top password manager and vault application that was also hacked just last year, found that people reuse their passwords an average of 13 times.
NodeZero helps our customers not only find their credential misconfigurations, so they can fix and remediate, but to understand the impact credential reuse can have on their network, business, and brand. Because those credentials are not only attempted on a single endpoint…but chained and reused in an attack path.
SO WHAT?
For instance, one of our mid-market customers ran a pentest operation at a geographically separated location and was astonished at the results.
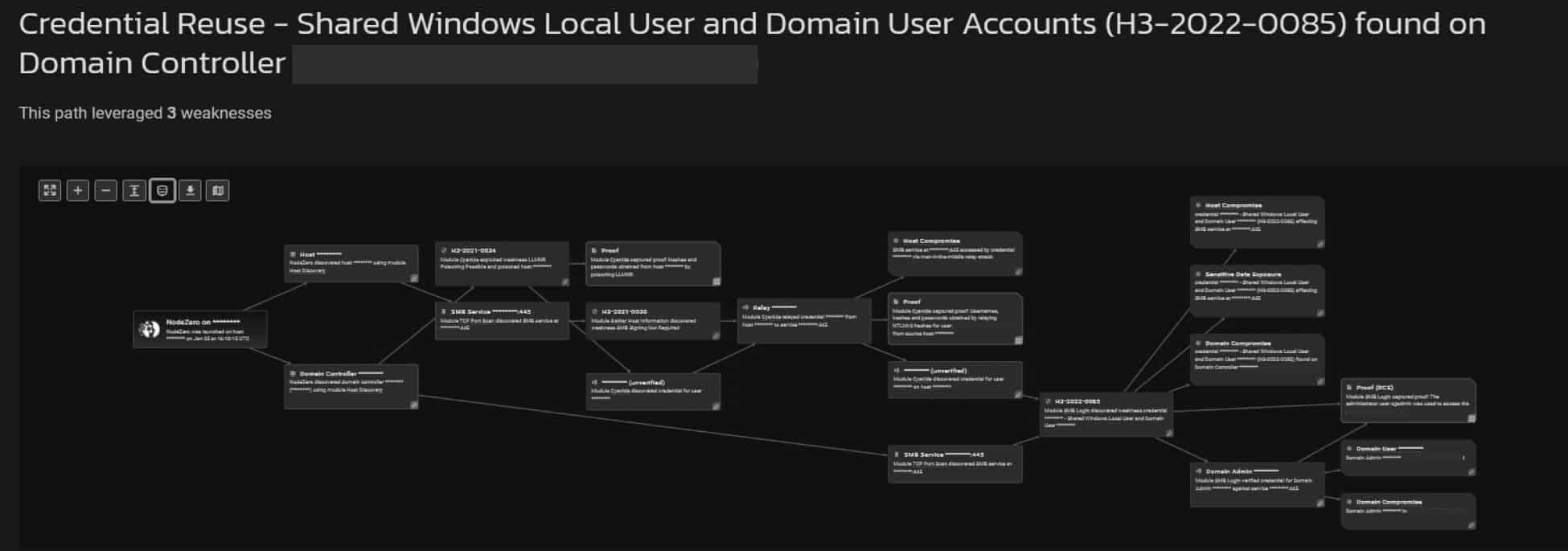
The attack path below illustrates how NodeZero autonomously:
- Enumerated and found two hosts, one of which is a Domain Controller
- Executed a Man-in-the-Middle attack and poisoned a host
- Captured a credential, and because Server Message Block (SMB) signing wasn’t required, was able to relay that credential and compromise the poisoned host
- From the compromised host, discovered a second local user credential and successfully logged in to the domain, proving it was a shared Windows local user and Domain user account
- Gained read/write access to the SMB shares of the Domain Controller as this credential was also a Domain Administrator
Without any prior knowledge of the network or any credentialed access, it literally took NodeZero less than a minute to chain together this attack path. This isn’t just because we have a good AI, but because credentials are the new RCE.
One credential:
- Local user
- Domain user
- Domain admin
NOW WHAT?
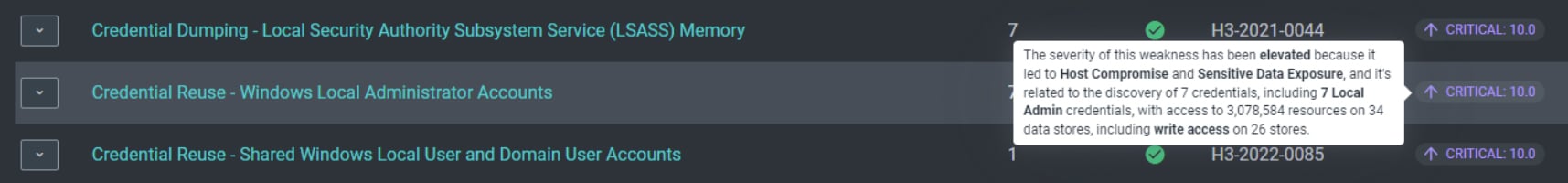
Now that you’ve seen what happened and why it matters, accurate and relevant remediation is key. NodeZero’s built-in context scoring allowed this customer to easily see which weaknesses and impacts they needed to focus on first.
NodeZero advises and gives immediate remediation and mitigation options:
- Implement Microsoft’s Local Administrator Password Solution (LAPS) to centrally manage local administrator accounts from Active Directory.
- Separate the local user and domain user account. Update the passwords for both accounts to be unique and ensure it follows current password guidelines.
- Update the password to be unique and ensure it follows current NIST password guidelines.
You’re now armed to ask the right questions:
- Teams: Are we looking for suspicious behavior such as logins from unusual locations or at unusual times?
- Tools: Is our monitoring and detection activity effective? Beyond LAPS, are there any other capabilities we can implement to automate our detection, logging, alerting, and preventing?
- Rules: Do we need to update our account and credential policies? Are they being enforced? Would MFA have helped us here?
Consequentially, you’re more prepared to answer the question your CEO and CFO are asking: “Are we prepared?”
This is one more example of how Credentials are the new RCE, and why Horizon3.ai continuously verifies your security posture so you can fix what matters.