Blogs
SEARCH
CATEGORIES
TAGS
From Patch Tuesday to Pentest Wednesday®: Continuous Validation in a Regulated Environment
February 11, 2026
By moving from annual snapshots to continuous validation, this organization replaced assumptions with proof. Findings became easier to prioritize. Remediation became easier to justify. Fixes could be verified instead of assumed.
How Horizon3.ai’s NodeZero® Platform Supports the Realtime Evaluation of the Effectiveness of Zero Trust Functionality for the US Federal Government.
February 5, 2026
NodeZero® enables federal agencies to continuously validate Zero Trust controls in production environments, delivering real-time, adversary-driven proof aligned to FedRAMP, NIST, CMMC, and DoD Zero Trust mandates.
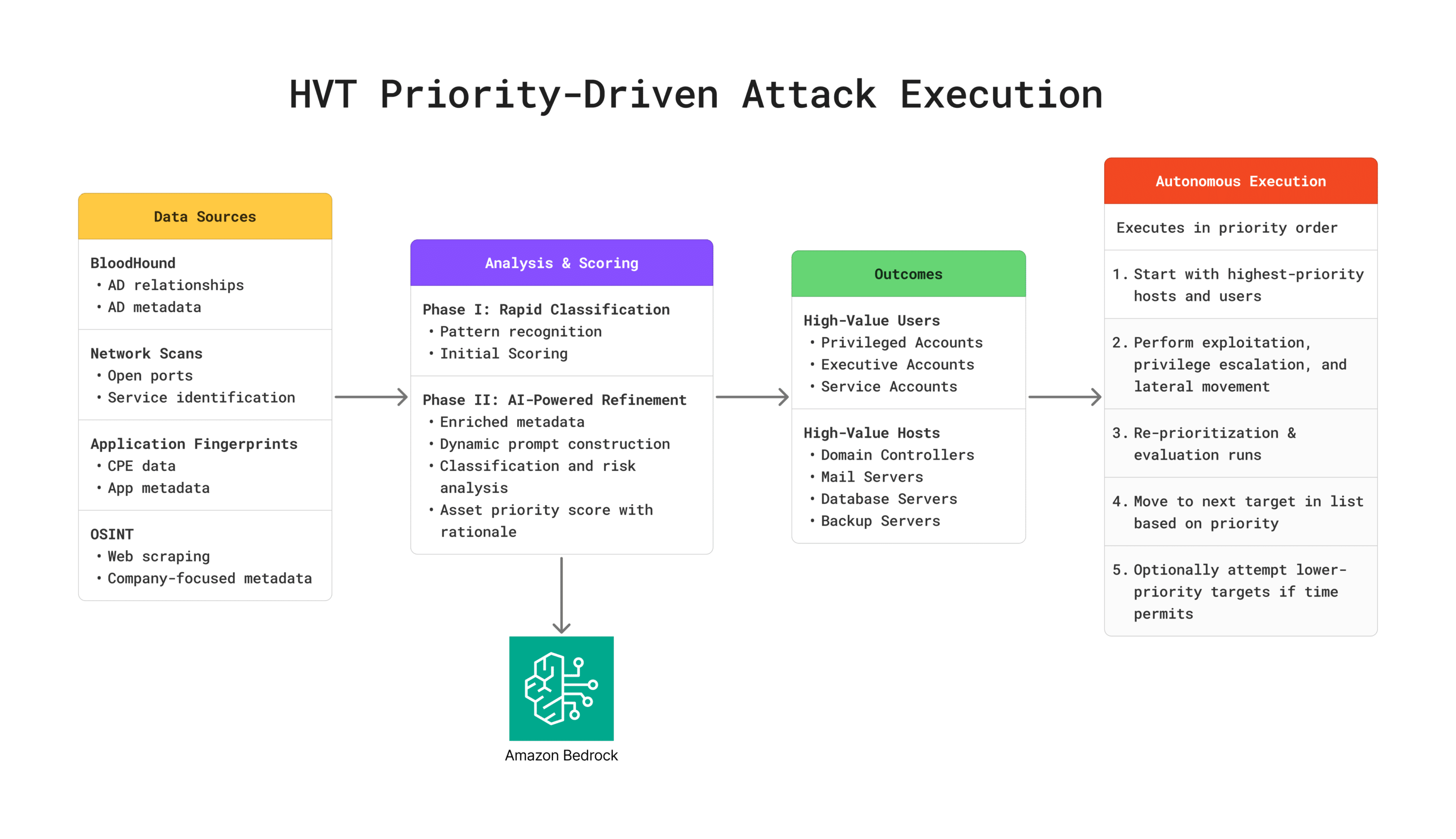
Introducing NodeZero® High-Value Targeting: Think Like an Attacker, Prioritize What Matters
January 20, 2026
High-Value Targeting (HVT) analyzes and prioritizes systems and accounts based on business impact, replicating how sophisticated attackers identify and prioritize targets after establishing initial access. It identifies domain controllers, privileged accounts, and critical infrastructure, directing NodeZero to test the most critical attack paths first. As NodeZero discovers new systems, credentials, and network relationships, HVT continuously…
From Patch Tuesday to Pentest Wednesday®: When Proving Compliance Becomes Cyber Resilience
January 14, 2026
A Pentest Wednesday® story showing how one of the world’s largest payments providers replaced point-in-time compliance testing with continuous, attacker-aligned validation.
How Horizon3.ai is Supporting the DoW Cybersecurity Risk Management Construct (CSRMC)
December 17, 2025
The DoW’s new Cybersecurity Risk Management Construct demands continuous, evidence-driven security. Learn how Horizon3.ai’s NodeZero delivers real-time, attacker-validated proof to support mission resilience.
From Patch Tuesday to Pentest Wednesday®: Proof That Redefined Security for a Manufacturer
December 10, 2025
Patch Tuesday is a known event, but attackers are moving faster than ever. For a leading U.S. manufacturer, shifting from simple patching to continuous validation became the key to proving their fixes worked, turning uncertainty into confidence.
Introducing Threat Informed Perspectives: A More Strategic Way to Measure Security Posture
Threat Informed Perspectives give organizations a structured, attacker-aligned way to measure exposure, track real security improvement, and validate remediation over time using continuous, evidence-driven insights from NodeZero.
Endpoint Detection and Response: What It Is and How to Know Yours Is Working
November 24, 2025
EDR tools offer visibility, but visibility isn’t protection. Learn why credential-driven attacks often bypass EDR and how NodeZero validates real-world detection, blocking, and effectiveness across your endpoints.
Prioritize What’s Proven: The NodeZero® Approach to Risk‑Based Vulnerability Management
November 18, 2025
Horizon3.ai’s NodeZero® redefines Risk-Based Vulnerability Management by connecting exploitability, business context, and attacker behavior. With new capabilities for High-Value Targeting, Advanced Data Pilfering, Threat Actor Intelligence, and Vulnerability Risk Intelligence, NodeZero moves vulnerability management from noise to proof—helping security teams prioritize, fix, and verify what truly matters.
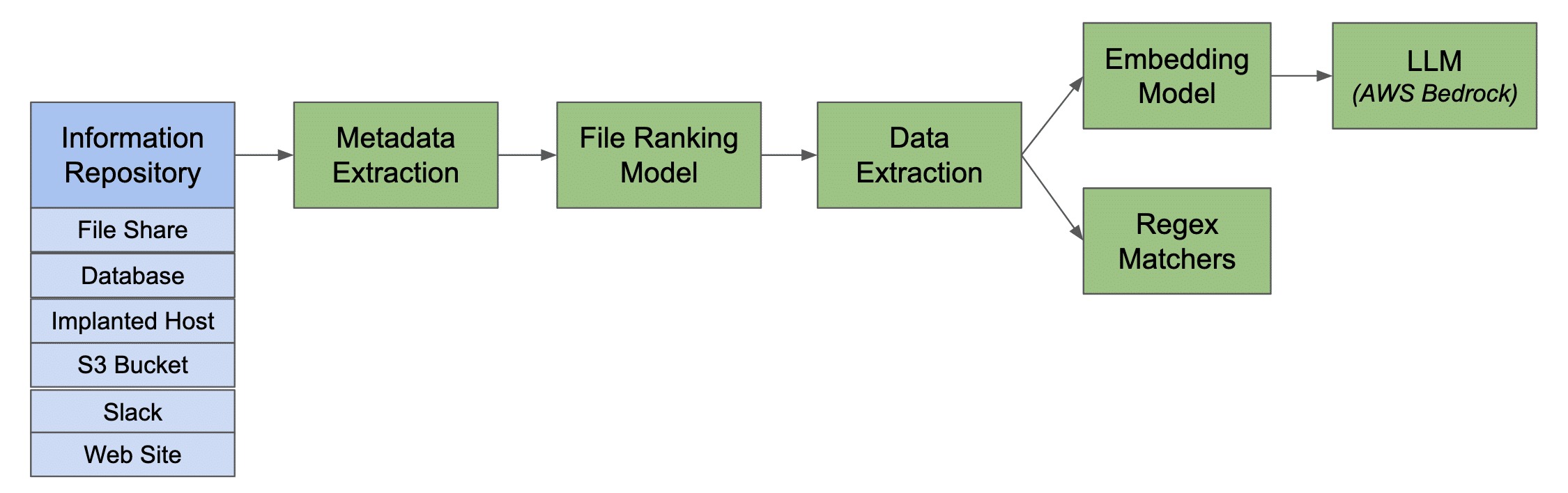
Introducing NodeZero® Advanced Data Pilfering: View Your Data Through the Eyes of an Attacker
NodeZero’s Advanced Data Pilfering uses LLMs to find hidden credentials and classify compromised files—revealing attacker paths and the real business risk in unstructured data.