The Typical Assessment Approach
Penetration testers, vulnerability scanners, and installed agents are supposed to alert you on potential vulnerabilities and suspected breaches. You receive a list, or a notification, and you respond. Have you ever wondered how often you spend time fixing or updating systems and software that may not even be exploitable?
You may be surprised to hear that a large majority of all vulnerabilities are unexploitable. For example, the US Government’s National Vulnerability Database (NVD) currently has over 242,919 entries. However, CISA’s known exploited vulnerabilities catalog (dating back to 2021), only contains 1093 entries. To date, less than 0.45 percent of all vulnerabilities being tracked are known to have been exploited in the wild.
The prioritization of these often low-risk or no-risk vulnerabilities alongside, or even above, your truly exploitable vulnerabilities can cause your organization’s security posture to suffer. It takes significant time and coordination to find the vulnerable-asset owners, bring them up to speed on the issue, prepare downtime for the asset, remediate the issue, and then confirm that the issue is resolved. Meanwhile, more critical vulnerabilities are waiting to be remediated. If you don’t understand what’s exploitable, and prioritize your remediation efforts, you will never be able to adequately secure your network.
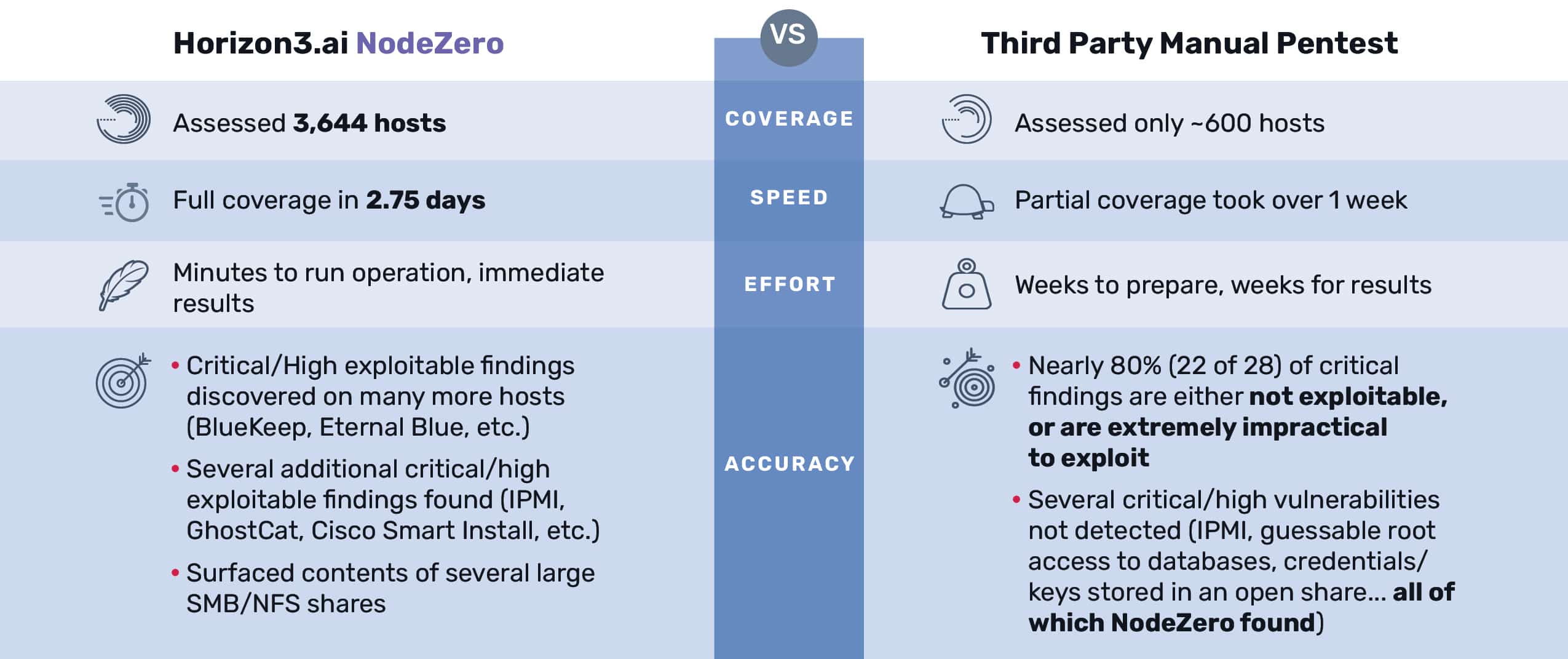
A client came to Horizon3.ai with the goal of validating the services they were using for pentesting, vulnerability scanning, and remediation. Their IT services had all been outsourced to a third party, and they wanted to make sure they were getting what they paid for. Plus, they were interested in comparing the results from the third party’s manual pentest to a Horizon3.ai’s NodeZero™ autonomous pentest.The third party had just conducted their annual pentest of the organization’s network environment. Then, Horizon3.ai used NodeZero to assess the same organization’s network, with the following comparative results:
Why Coverage and Accuracy matter
The hardest part of cyber security is deciding what NOT to fix because of limited time and resources.
From the comparative results just mentioned, it’s safe to say that manual penetration testing can create an incomplete snapshot:
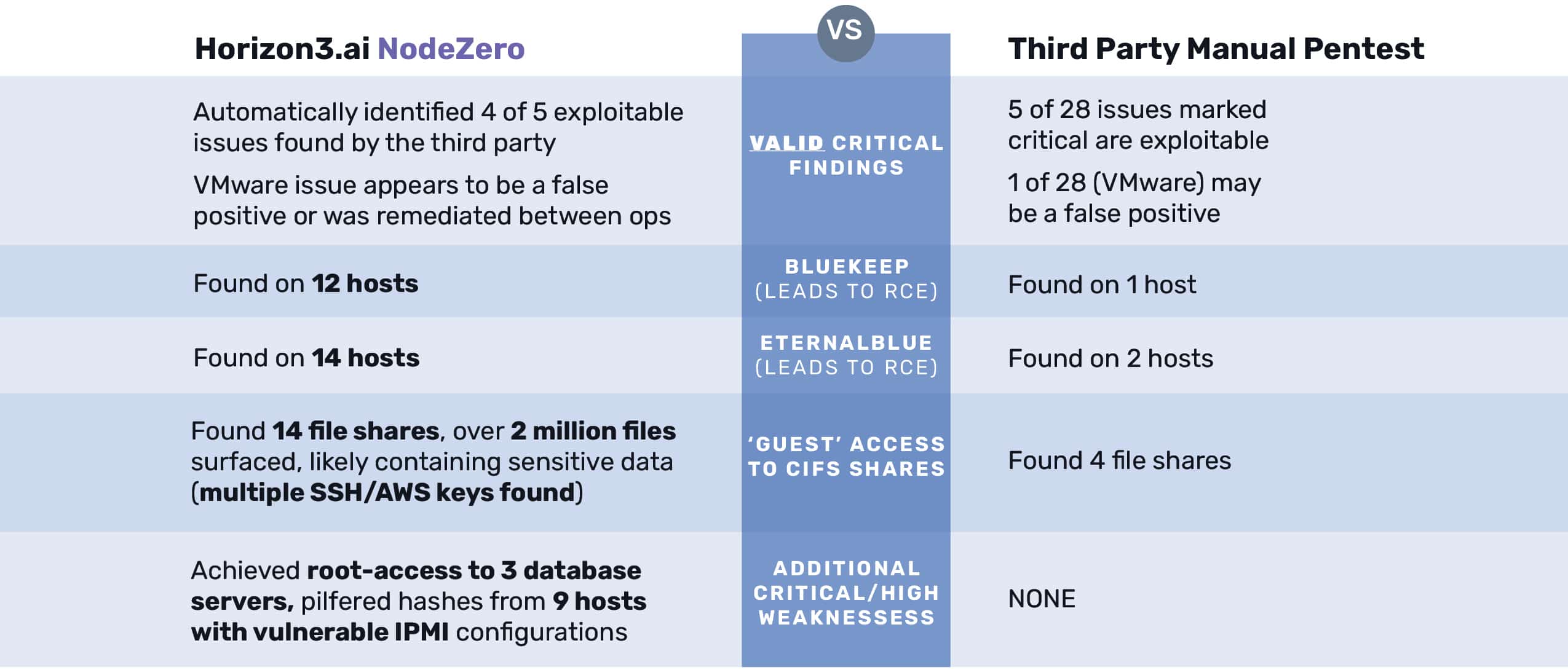
- For 22 of the 28 critical findings from the third party, no
exploits exist, or the conditions to exploit these issues are extremely unlikely. - Poor enumeration leads to blind spots, and incomplete
fingerprinting provides a false sense of security, proving port
scans are not enough! - Partial test coverage leads to missed critical findings.
Fixing 79% of the critical issues highlighted in the third party’s report would have been an inefficient use of time and effort. These discovered “critical issues” did not have available exploits, were likely assumed due to poor enumeration, or the conditions for exploitability were extremely unlikely.
Meanwhile, the third party’s team only identified one host vulnerable to BlueKeep, while NodeZero found an additional 11. NodeZero also proved three additional critical/high weaknesses, including easily guessable root access to a database server.
When the noise is removed, the critical findings are revealed.
The Horizon3.ai Difference
Using the same tactics, techniques, and procedures attackers use, NodeZero gives you a distinct advantage.
Organizations of all sizes who have adopted NodeZero as part of their risk assessment process, and added it into their cybersecurity programs, experience the following benefits, and more:
- Eliminate risks and validate security with continuous assessments. Provides proof of current security levels, highlights effective remediations, tracks improvement over time, and generates reports that analysts and auditors understand.
- Improve security performance and visibility of risk level. Delivers reports that leaders will appreciate and verifies risks are identified, prioritized, and addressed, plus justifying their investment, and proving its effectiveness.
- Spot attack vectors before they’re exploited through easy-to-understand attack paths. Proactively identifies weaknesses and provides top-level views of larger systemic issues, and how to address them at a macro level for long-term cyber resilience.
- Obtain a prioritized list of what needs fixing most urgently. Eliminates time-consuming false positives and improves the capacity of security and IT teams regardless of the level of expertise or size of the overall team.
- Perform assessments on demand. Allows teams to find, fix, and verify as often as they like – and even concurrently – without additional costs while reducing the need to hire third party assessors and penetration testers.
Find your most critical risks, fix what matters most.
NodeZero is easy to use, safe for production, and scales to support your largest networks.
NodeZero pivots through your network, chaining together weaknesses just as an attacker would and then safely exploits them. You have full visibility into your pentest’s progress, and the exploits being executed in a real-time view.
When the test is complete, the results are prioritized for your immediate action. The dashboard reveals your critical weaknesses, their impact to your organization, and provides detailed remediation guidance for addressing them at a systemic level as well as individually.
The Future State
Overall, the comparison between the third party’s pentest report and the NodeZero report shows that NodeZero provides broader coverage, proves exploitability, contextualizes weaknesses, and provides the defensive team with the information they need to fix what matters most.
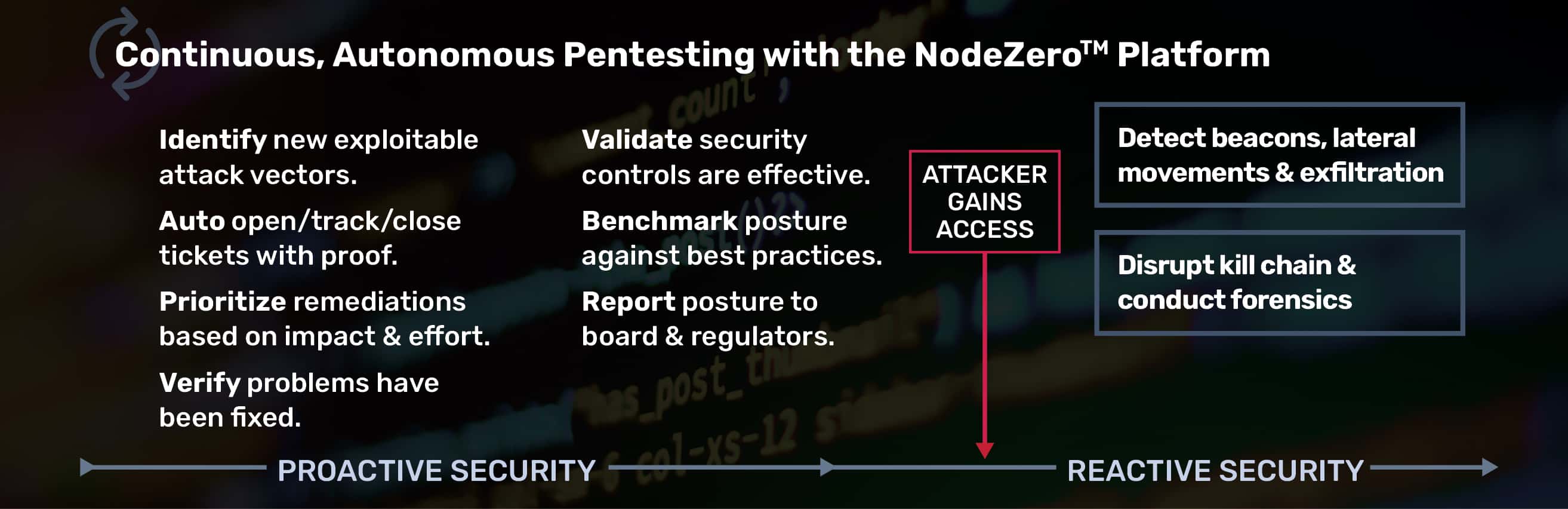
Our work with this client exemplifies the need for a proactive security posture that includes continuous assessment, so you can catch up, keep up, and stay ahead of the exploitable risks in your environments.
Catch Up
Identify exploitable attack paths that must be fixed immediately, significantly reducing the risk of exploitation, sensitive data exposure, elevated privileges, or remote code execution.
Your first NodeZero operation will provide this insight and minimize the time spent dealing with false positives.
NodeZero’s offensive approach discovers and proves where your greatest vulnerabilities exist.
For me, the biggest benefit is the attack path identification and actual prioritization of the vulnerabilites. Other tools simply pull the CVE value, and we get hundreds of criticals and highs.
Keep Up
Following a NodeZero pentest, blue teams can remediate identified vulnerabilities and re-run the test with a One-Click Verify to validate their remediation actions were successful.
NodeZero can also act as a force multiplier for red teams. It can autonomously execute pentests, freeing those teams to focus on more sophisticated, pinpointed attacks.
Run multiple NodeZero operations per week – our licenses give you unlimited access.
Stay Ahead
Continuously verify your security controls, tools, processes, and policies by measuring and optimizing your detection, remediation, and compliance response times.
Use NodeZero reports to show your leadership and board where you stand. Not just a compliance checkbox; this is effective security.
Use NodeZero’s compare feature to power your security standups.